Data Risk

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
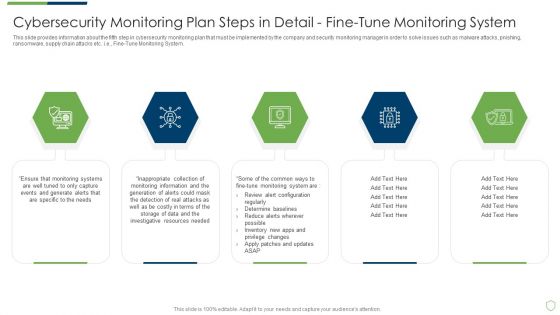
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

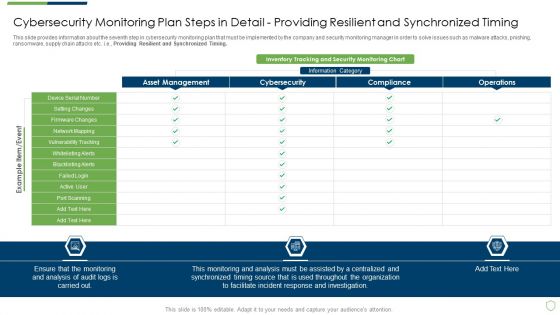
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
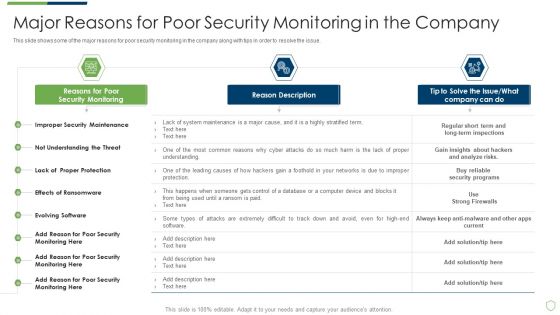
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
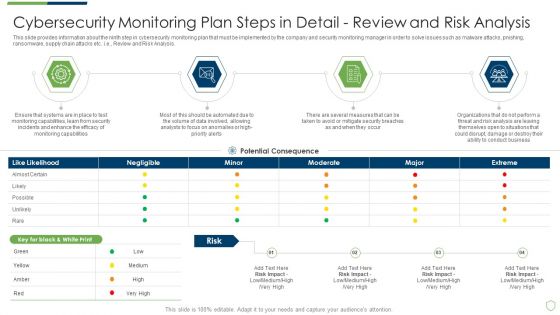
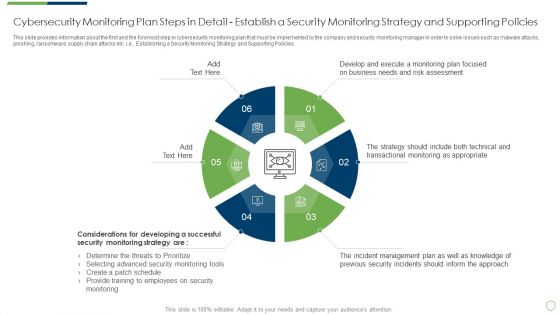
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF. Use them to share invaluable insights on Required Standard Rating Actual, Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risks Of Process Oriented Data Stewardship Model Data Custodianship Icons Pdf
This slide talks about the risks associated with the process oriented data stewardship model, including the complexity of data ownership assignment, and company constituents can get confused due to so many definitions for exact information and getting feedback from a single end user. Explore a selection of the finest Risks Of Process Oriented Data Stewardship Model Data Custodianship Icons Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Risks Of Process Oriented Data Stewardship Model Data Custodianship Icons Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Risks Of System Oriented Data Stewardship Model Data Custodianship Information Pdf
This slide represents the risks associated with the system oriented data stewardship model. Business users can get confused between data ownership and data stewardship, and they can consider data stewardship as an IT issue, data stewards can be short sighted, and so on. The Risks Of System Oriented Data Stewardship Model Data Custodianship Information Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
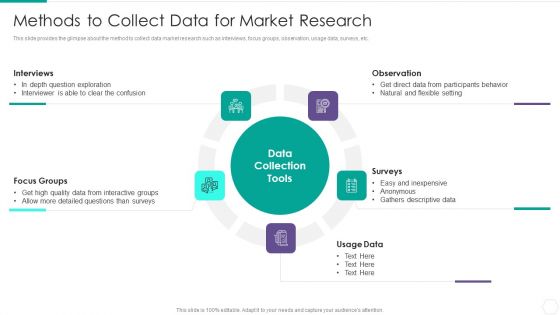
Quantitative Risk Assessment Methods To Collect Data For Market Research Guidelines PDF
This slide provides the glimpse about the method to collect data market research such as interviews, focus groups, observation, usage data, surveys, etc. Presenting Quantitative Risk Assessment Methods To Collect Data For Market Research Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Observation, Surveys, Usage Data, Focus Groups, Interviews. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
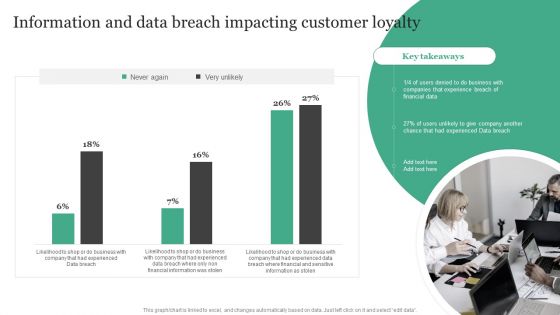
Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF
The purpose of this slide is to represent a process for cybersecurity digital risk assessment to analyze business threats. It includes various stages such as classifying information assets, evaluating risks, examining risk, observing and reviewing effectiveness and implementing security controls. Presenting Cybersecurity Online Risk Assessment Process To Enhance Data Protection Introduction PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Classify Information Assets, Evaluate Risk, Examine Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Credit Risk Management Process With Gather Data Ppt PowerPoint Presentation Inspiration Templates PDF
Presenting credit risk management process with gather data ppt powerpoint presentation inspiration templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including quantitative analysis, quantitative analysis, recent developments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Threat Administration Bundle Organization Risk Assessment And Tracking Log Data Designs PDF
Presenting threat administration bundle organization risk assessment and tracking log data designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like analysis, prototype, monitor, inadequate team, data collection inaccurate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technology Guide For Serverless Computing Business Risk Related To Cloud Computing Data Portrait PDF
This is a technology guide for serverless computing business risk related to cloud computing data portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
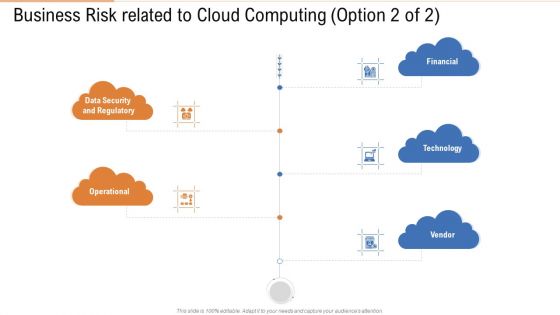
Business Risk Related To Cloud Computing Data Ppt Outline Slide Portrait PDF
This is a business risk related to cloud computing data ppt outline slide portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, technology, financial, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Bank And Finance Risk Management Tools And Methodologies Data Analysis On Bank Ideas PDF
This slide shows the data analysis of XYZ banks NPAs with other competitor banks and also the loans and advances for the same. Explore a selection of the finest Bank And Finance Risk Management Tools And Methodologies Data Analysis On Bank Ideas PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Bank And Finance Risk Management Tools And Methodologies Data Analysis On Bank Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
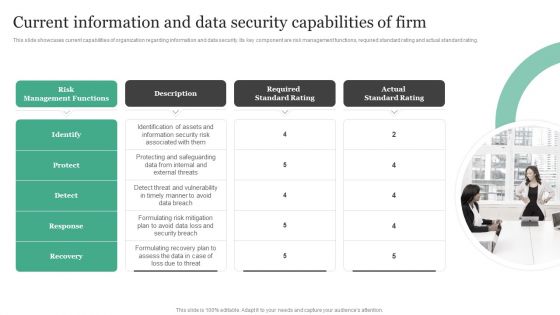
Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating.Do you know about Slidesgeeks Current Information And Data Security Capabilities Of Firm Information Security Risk Administration Designs PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
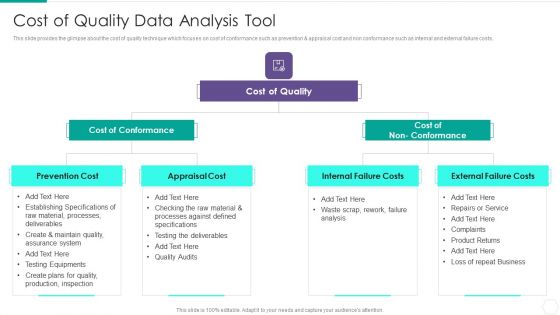
Quantitative Risk Assessment Cost Of Quality Data Analysis Tool Graphics PDF
Presenting Quantitative Risk Assessment Cost Of Quality Data Analysis Tool Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Cost Of Conformance, Cost Of Quality, Internal Failure Costs, External Failure Costs, Appraisal Cost. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Companys Data Safety Recognition Effect After Implementing Cyber Risk Security Awareness Program Formats PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition effect after implementing cyber risk security awareness program formats pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
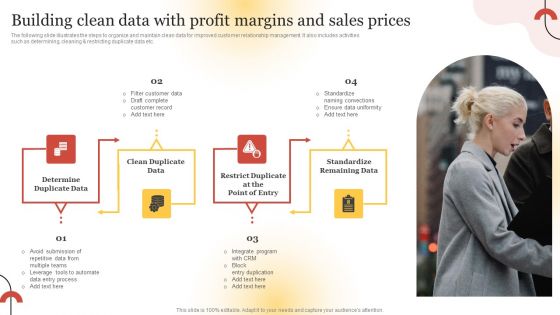
Executing Sales Risk Reduction Plan Building Clean Data With Profit Margins And Sales Prices Template PDF
The following slide illustrates the steps to organize and maintain clean data for improved customer relationship management. It also includes activities such as determining, cleaning and restricting duplicate data etc. Want to ace your presentation in front of a live audience Our Executing Sales Risk Reduction Plan Building Clean Data With Profit Margins And Sales Prices Template PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Data Safety Initiatives KPI Dashboard To Track Security Risk Events Portrait PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this data safety initiatives kpi dashboard to track security risk events portrait pdf. Use them to share invaluable insights on risk category, total risk rating, residual risk by period, technology risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Safety Initiatives Responsibility Matrix To Ensure Effective Risk Management Summary PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver and pitch your topic in the best possible manner with this data safety initiatives responsibility matrix to ensure effective risk management summary pdf. Use them to share invaluable insights on cybersecurity strategy and program phase, technical team, leadership and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
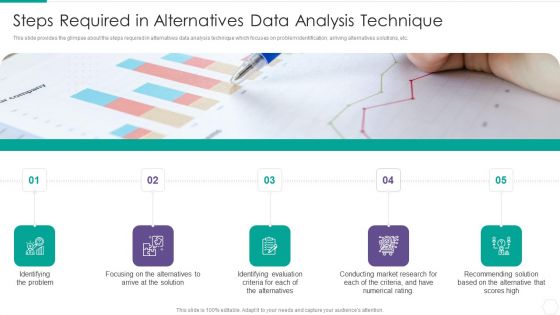
Quantitative Risk Assessment Steps Required In Alternatives Data Analysis Technique Portrait PDF
This slide provides the glimpse about the steps required in alternatives data analysis technique which focuses on problem identification, arriving alternatives solutions, etc. This is a Quantitative Risk Assessment Steps Required In Alternatives Data Analysis Technique Portrait PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Steps Required In Alternatives Data Analysis Technique. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Assessing Sales Risks Building Clean Data With Profit Margins And Sales Prices Template PDF
The following slide illustrates the steps to organize and maintain clean data for improved customer relationship management. It also includes activities such as determining, cleaning and restricting duplicate data etc. There are so many reasons you need a Assessing Sales Risks Building Clean Data With Profit Margins And Sales Prices Template PDF The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
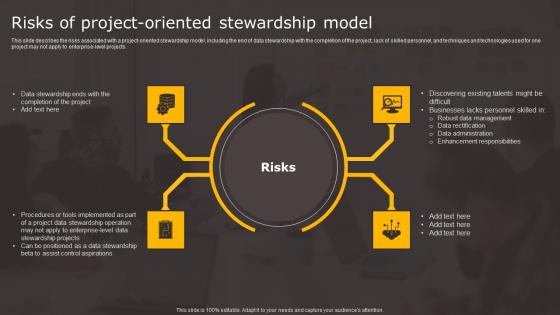
Data Stewardship In Business Processes Risks Of Project Oriented Stewardship Sample Pdf
This slide describes the risks associated with a project oriented stewardship model, including the end of data stewardship with the completion of the project, lack of skilled personnel, and techniques and technologies used for one project may not apply to enterprise level projects. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Data Stewardship In Business Processes Risks Of Project Oriented Stewardship Sample Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
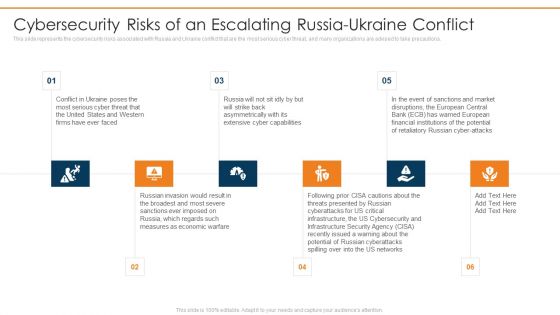
Data Wiper Spyware Attack Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Background PDF
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions.This is a data wiper spyware attack cybersecurity risks of an escalating russia ukraine conflict background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extensive cyber capabilities, russian invasion would, measures as economic warfare You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risks And Mitigation Strategies For Data Data Center Migration For Information Graphics PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Risks And Mitigation Strategies For Data Data Center Migration For Information Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Risks And Mitigation Strategies For Data Data Center Migration For Information Graphics PDF.
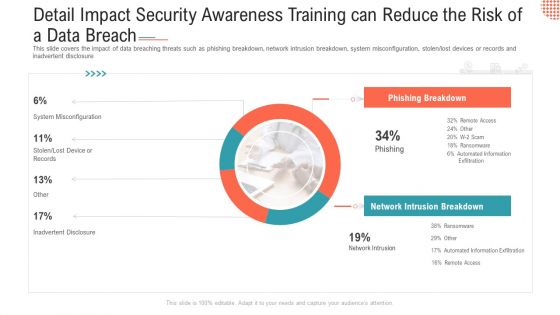
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Layouts Examples PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen lost devices or records and inadvertent disclosure Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach ppt layouts examples pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
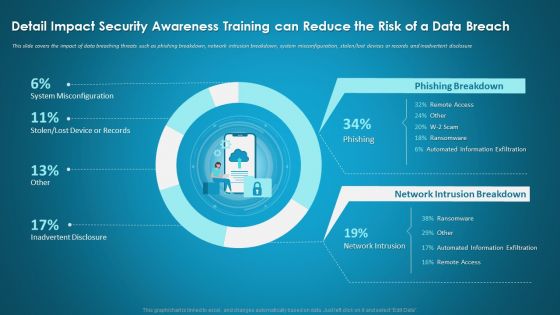
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Outline Gridlines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt outline gridlines pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Case Study Risk Reduction For Financial Importance Of Unstructured Data Ppt Presentation
This slide presents a case study on the use of dark data in a financial services organization. The purpose of case study explains how the organization started by identifying and categorizing its dark data, then evaluated the datas value and risk.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Risk Reduction For Financial Importance Of Unstructured Data Ppt Presentation a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Risk Reduction For Financial Importance Of Unstructured Data Ppt Presentation. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
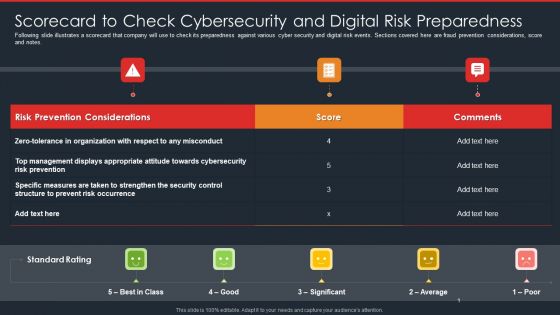
Data Safety Initiatives Scorecard To Check Cybersecurity And Digital Risk Preparedness Rules PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver an awe inspiring pitch with this creative data safety initiatives scorecard to check cybersecurity and digital risk preparedness rules pdf bundle. Topics like risk prevention considerations, score, standard rating, top management displays can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
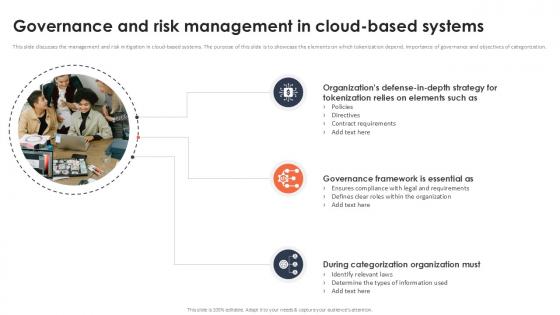
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Scale Up Plan For Data Inventory Model Major Risks And Mitigation Strategies For Database System Expansion Background PDF
This slide tabulates the key risks associated with data repository expansion. It also provides information regarding risk probability, impact, and corresponding mitigation strategies. Deliver and pitch your topic in the best possible manner with this scale up plan for data inventory model major risks and mitigation strategies for database system expansion background pdf. Use them to share invaluable insights on probability, risk, impact, mitigation strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
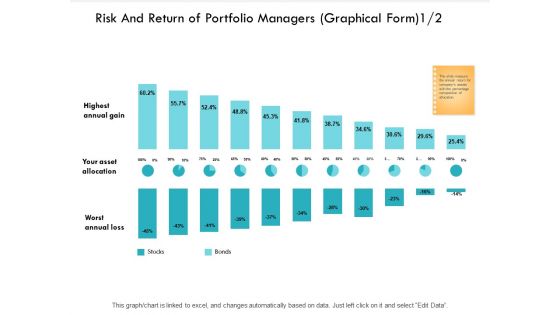
Risk And Return Of Portfolio Managers Graphical Form Edit Data Ppt PowerPoint Presentation Summary Graphics
Presenting this set of slides with name risk and return of portfolio managers graphical form edit data ppt powerpoint presentation summary graphics. The topics discussed in these slides are business, planning, strategy, marketing, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Corporate Security And Risk Management Addressing Internal And External Sources Of Threat Data Gathering Template PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Presenting corporate security and risk management addressing internal and external sources of threat data gathering template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like targeted intelligence, malware intelligence, reputation intelligence . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Detail Impact Information Technology Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Layouts Show PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this it security detail impact information technology security plan can reduce the risk of data breach in organization ppt layouts show pdf. Use them to share invaluable insights on detail impact information technology security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Business Risk Related To Cloud Computing Data Diagrams PDF
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risks And Mitigation Strategies For Data Center Relocation Ppt PowerPoint Presentation File Example PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. If you are looking for a format to display your unique thoughts, then the professionally designed Risks And Mitigation Strategies For Data Center Relocation Ppt PowerPoint Presentation File Example PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Risks And Mitigation Strategies For Data Center Relocation Ppt PowerPoint Presentation File Example PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF
The following slide provides information about the risks involved in data center relocation process and the strategies that must be implemented in order to mitigate the risks. Major risks are unwanted downtime, data loss, data security and added latency. This modern and well-arranged Assessment And Workflow Risks And Mitigation Strategies For Data Center Relocation Icons PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Risks And Incident Response Playbook Data Backup Evaluation Sheet Download PDF
Mentioned slide addresses evaluation sheet which can be used for assessing data backup activities. Sections covered in the sheet are backup testing frequency, type of backup solution and responsible person details. Are you in need of a template that can accommodate all of your creative concepts. This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Risks And Incident Response Playbook Data Backup Evaluation Sheet Download PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Developing Organization Primary Data Storage Action Plan Major Risks And Mitigation Strategies For Database System Guidelines PDF
This slide tabulates the key risks associated with data repository expansion. It also provides information regarding risk probability, impact, and corresponding mitigation strategies. Deliver an awe inspiring pitch with this creative developing organization primary data storage action plan major risks and mitigation strategies for database system guidelines pdf bundle. Topics like major risks and mitigation strategies for database system expansion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach hacking prevention awareness training for it security professional pdf. Use them to share invaluable insights on system misconfiguration, network intrusion breakdown, phishing breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Sales Risk Assessment For Profit Maximization Building Clean Data With Profit Margins And Sales Prices Guidelines PDF
The following slide illustrates the steps to organize and maintain clean data for improved customer relationship management. It also includes activities such as determining, cleaning and restricting duplicate data etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Sales Risk Assessment For Profit Maximization Building Clean Data With Profit Margins And Sales Prices Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Risks Types Of Outsourcing Fraud Financial And Data Security Ppt PowerPoint Presentation File Example
Presenting this set of slides with name risks types of outsourcing fraud financial and data security ppt powerpoint presentation file example. This is a four stage process. The stages in this process are business process outsourcing, circular infographics, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF
This slide covers an overview of the spam rate to identify the number of recipients who mark messages as spam in their inboxes. It also includes strategies to reduce spam, such as sending emails only to those who have opted to receive them, segmenting your email list, etc. Get a simple yet stunning designed Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Marketers Guide To Data Analysis Optimization Tracking Spam Complaint Rate To Avoid Account Suspension Risk Template PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Determining Risks In Sales Administration Procedure Building Clean Data With Profit Margins And Sales Prices Topics PDF
The following slide illustrates the steps to organize and maintain clean data for improved customer relationship management. It also includes activities such as determining, cleaning and restricting duplicate data etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Determining Risks In Sales Administration Procedure Building Clean Data With Profit Margins And Sales Prices Topics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Mitigating Sales Risks With Strategic Action Planning Building Clean Data With Profit Margins And Sales Prices Slides PDF
The following slide illustrates the steps to organize and maintain clean data for improved customer relationship management. It also includes activities such as determining, cleaning and restricting duplicate data etc. Want to ace your presentation in front of a live audience Our Mitigating Sales Risks With Strategic Action Planning Aligning Cross Functional Team Activities Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Configuration Risk Management And Risk Analysis Software Report Download PDF
This slide covers the summary status report of different risks and errors accumulated during system configuration. It includes data backup error, roll back of source code, data recovery failure, unauthorised access, etc. with solutions. Persuade your audience using this Configuration Risk Management And Risk Analysis Software Report Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Source Code, Data Backup Error, Risk Summary. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home