Cybersecurity
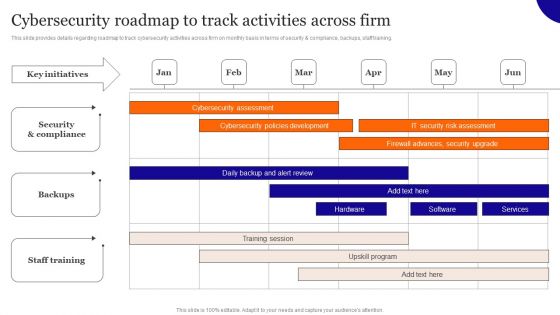
Cybersecurity Roadmap To Track Activities Across Firm Inspiration PDF
This slide provides details regarding roadmap to track cybersecurity activities across firm on monthly basis in terms of security and compliance, backups, staff training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Roadmap To Track Activities Across Firm Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Roadmap To Track Activities Across Firm Inspiration PDF today and make your presentation stand out from the rest

Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF
This slide provides details regarding cybersecurity trends existing across globe in terms of rise in automotive hacking, IoT with 5G, cloud platform as potential vulnerable, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Highlighting Ongoing Cybersecurity Trends Across Globe Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF
This slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. ITOT industrial cyber security deployment. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Two Way Interactions Between Safety Security And Cybersecurity Microsoft PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cybersecurity Employee Training Status With Completion Status Structure PDF
This slide exhibits a security awareness training checklist to educate employees and protect the company from malware attacks. It includes categories for training such as password protection, browsers, devices, and network connection. Pitch your topic with ease and precision using this Cybersecurity Employee Training Status With Completion Status Structure PDF. This layout presents information on Training Status Completion Status, Cybersecurity Employee. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
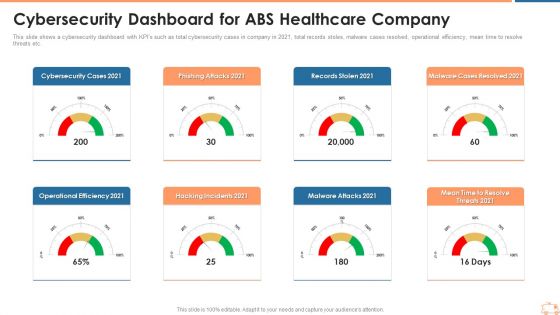
Cybersecurity Dashboard For ABS Healthcare Company Ppt Themes PDF
This slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Presentingcybersecurity dashboard for abs healthcare company ppt themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like phishing attacks 2021, records stolen 2021, malware cases resolved 2021, malware attacks 2021, hacking incidents 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
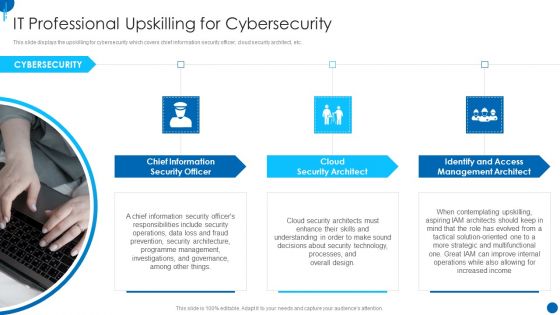
Information Technology Strategy IT Professional Upskilling For Cybersecurity Guidelines PDF
This slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. This is a information technology strategy it professional upskilling for cybersecurity guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like chief information, security officer, cloud security architect, identify and access management architect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Resilience Matrix For Corporate Organization Rules PDF
This slide illustrates the cybersecurity resilience matrix for business organization such as initial, recognition, maturity stage and optimization. An organization achieves high level of resilience at fourth quadrant. Persuade your audience using this Cybersecurity Resilience Matrix For Corporate Organization Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Optimization, Maturity, Recognition. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Top Cybersecurity Threats In Net Banking Download PDF
The following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Persuade your audience using this Top Cybersecurity Threats In Net Banking Download PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Unencrypted Data, Spoofing, Phishing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF
Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Puzzle Cybersecurity Risk Assessment And Administration Plan Inspiration PDF.

Agenda Cybersecurity Guidelines IT Ppt PowerPoint Presentation Gallery Layout PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Agenda Cybersecurity Guidelines IT Ppt PowerPoint Presentation Gallery Layout PDF can be your best option for delivering a presentation. Represent everything in detail using Agenda Cybersecurity Guidelines IT Ppt PowerPoint Presentation Gallery Layout PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Cybersecurity Guidelines IT Puzzle Ppt PowerPoint Presentation Gallery Tips PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Guidelines IT Puzzle Ppt PowerPoint Presentation Gallery Tips PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Guidelines IT Puzzle Ppt PowerPoint Presentation Gallery Tips PDF,

ML Business Applications In Cybersecurity Business Information PDF
This slide represents machine learning use cases which industries utilize to combat cybersecurity threats, analyze vulnerabilities and provide protection against attacks. Use cases included in this slide are malware detection, software vulnerabilities, phishing attacks, etc. Presenting ML Business Applications In Cybersecurity Business Information PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Network Logs Analysis, Phishing Attacks, Malware Detection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
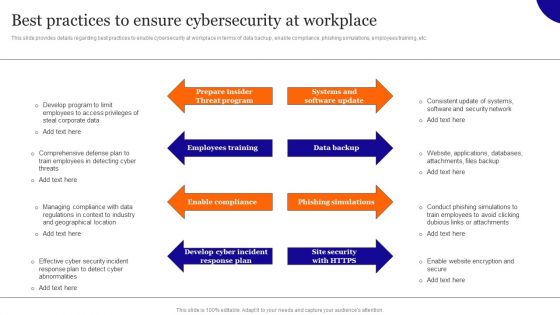
Best Practices To Ensure Cybersecurity At Workplace Structure PDF
This slide provides details regarding best practices to enable cybersecurity at workplace in terms of data backup, enable compliance, phishing simulations, employees training, etc. Present like a pro with Best Practices To Ensure Cybersecurity At Workplace Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF
This slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Want to ace your presentation in front of a live audience Our Cybersecurity Threat Management Activities Tracking Dashboard Pictures PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Issues Classification Impact And Solutions In Cybersecurity Pictures PDF
This slide presents categories of issues faced in cybersecurity along with impact and solutions, helpful in safeguarding organisation from hackers. It includes malware, password theft, traffic interception an phishing attack Pitch your topic with ease and precision using this Issues Classification Impact And Solutions In Cybersecurity Pictures PDF. This layout presents information on Malware, Password Theft, Traffic Interception. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
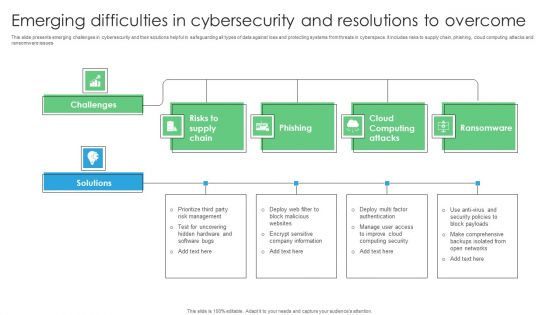
Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF
This slide presents emerging challenges in cybersecurity and their solutions helpful in safeguarding all types of data against loss and protecting systems from threats in cyberspace. It includes risks to supply chain, phishing, cloud computing attacks and ransomware issues. Introducing Emerging Difficulties In Cybersecurity And Resolutions To Overcome Rules PDF. to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risks Supply Chain, Phishing, Cloud Computing Attacks, using this template. Grab it now to reap its full benefits.
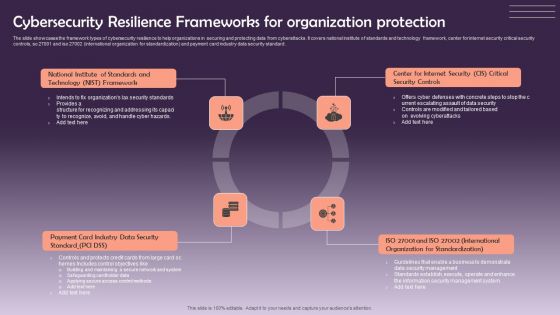
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
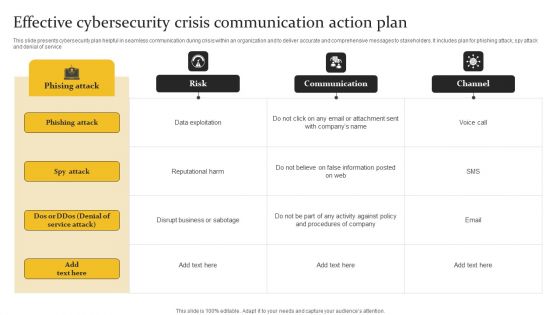
Effective Cybersecurity Crisis Communication Action Plan Graphics PDF
This slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Pitch your topic with ease and precision using this Effective Cybersecurity Crisis Communication Action Plan Graphics PDF. This layout presents information on Phishing Attack, Data Exploitation, Reputational Harm. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Implementation Framework Present Concerns Impeding Cybersecurity Clipart PDF
Presenting this set of slides with name cyber security implementation framework present concerns impeding cybersecurity clipart pdf. The topics discussed in these slides are data breaches and records exposed, reported financial losses due to increase cybercrimes, financial losses, cybercrimes incidents. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
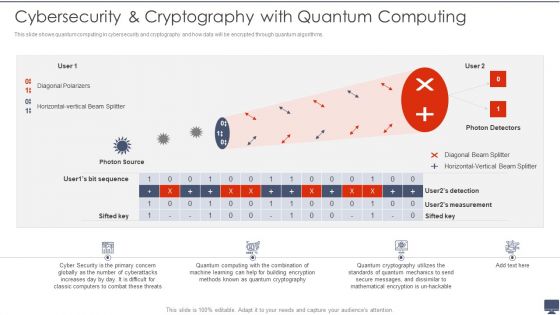
Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Andcryptography With Quantum Computing Ppt Pictures Backgrounds PDF. Use them to share invaluable insights on Cyber Security, Globally, Measurement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Computer Security Incident Handling Cybersecurity Maintenance Checklist Background PDF
Presenting this set of slides with name computer security incident handling cybersecurity maintenance checklist background pdf. The topics discussed in these slides are system monitoring real time, backup monitoring, preventive maintenance, virus scanning, security patches, executive reporting, review and planning meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
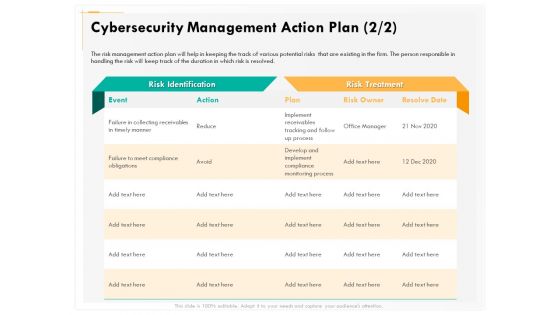
Computer Security Incident Handling Cybersecurity Management Action Plan Graphics PDF
Presenting this set of slides with name computer security incident handling cybersecurity management action plan graphics pdf. The topics discussed in these slides are risk identification, risk treatment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Worksheet Ideas PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
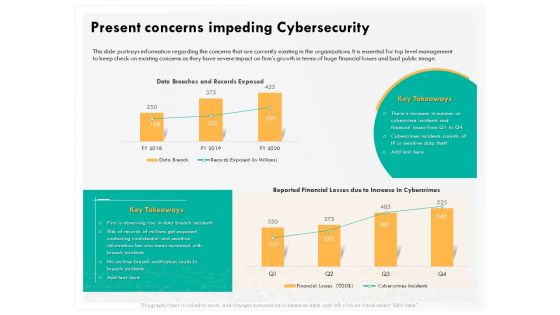
Computer Security Incident Handling Present Concerns Impeding Cybersecurity Formats PDF
Presenting this set of slides with name computer security incident handling present concerns impeding cybersecurity formats pdf. The topics discussed in these slides are reported financial losses due to increase in cybercrimes, data branches and records exposed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cybersecurity Process Technology Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name cybersecurity process technology ppt powerpoint presentation complete deck. The topics discussed in these slides are process, technology, management, analytics, development. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Approaches To Implement Advanced Cybersecurity Monitoring Plan Comparison Inspiration PDF
This is a approaches to implement advanced cybersecurity monitoring plan comparison inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Approaches To Implement Advanced Cybersecurity Monitoring Plan Roadmap Brochure PDF
Presenting approaches to implement advanced cybersecurity monitoring plan roadmap brochure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Tools To Be Implemented Topics PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring tools to be implemented topics pdf. Use them to share invaluable insights on security monitoring, password auditing tool, tool implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Scorecard Post It Notes Pictures PDF
Presenting cybersecurity risk scorecard post it notes pictures pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Icons Slide For Cybersecurity Risk Scorecard Structure PDF
Presenting our innovatively structured icons slide for cybersecurity risk scorecard structure pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For Mitigating Cybersecurity Threats And Vulnerabilities Microsoft PDF
Introducing our well designed icons slide for mitigating cybersecurity threats and vulnerabilities microsoft pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
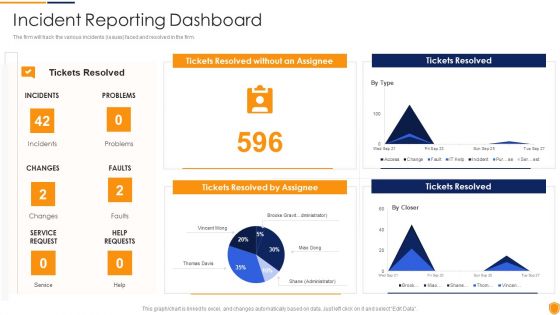
Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Dashboard Demonstration PDF
The firm will track the various incidents issues faced and resolved in the firm. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities incident reporting dashboard demonstration pdf bundle. Topics like incident reporting dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Impact Assessment Matrix Graphics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact Assessment Matrix Graphics PDF Use them to share invaluable insights on Minor To No Infringement, Suspected Malicious Intent, Operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Agenda Of Cybersecurity Risk Administration Plan Demonstration PDF
This is a Agenda Of Cybersecurity Risk Administration Plan Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For Cybersecurity Risk Administration Plan Brochure PDF
Download our innovative and attention grabbing Icons Slide For Cybersecurity Risk Administration Plan Brochure PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Cybersecurity Risk Assessment And Administration Plan Template PDF
Find a pre-designed and impeccable Cybersecurity Risk Assessment And Administration Plan Template PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
Icons Slide For Improving Cybersecurity With Incident Ideas PDF
Introducing our well designed Icons Slide For Improving Cybersecurity With Incident Ideas PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Purpose Of Improving Cybersecurity With Incident Icons PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Purpose Of Improving Cybersecurity With Incident Icons PDF from Slidegeeks and deliver a wonderful presentation.

Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF
This slide represents the severity level of application vulnerabilities and the number of total attacks. The purpose of this slide is to showcase the various threats caused by security vulnerabilities. The main threats include sensitive data leakage, unauthorized access to data and apps, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Problems With Current Network System Formats PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
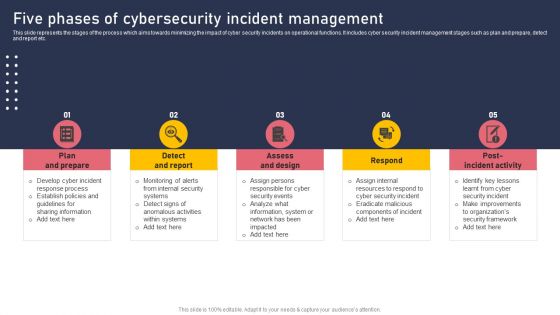
Five Phases Of Cybersecurity Incident Management Topics PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Five Phases Of Cybersecurity Incident Management Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Five Phases Of Cybersecurity Incident Management Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
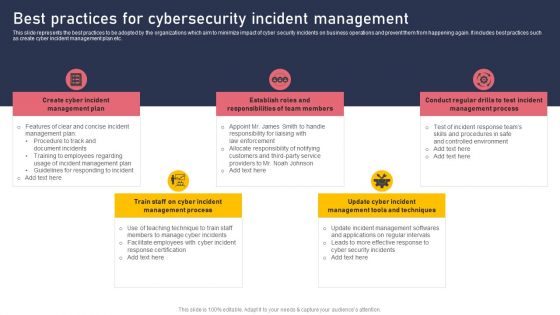
Best Practices For Cybersecurity Incident Management Summary PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Best Practices For Cybersecurity Incident Management Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Best Practices For Cybersecurity Incident Management Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Training Program Budget And Schedule Dates Graphics PDF
This slide covers the training schedule for various cyber security incidents program. It further includes budget allocated, training duration, dates for training and review sessions.Showcasing this set of slides titled Cybersecurity Training Program Budget And Schedule Dates Graphics PDF. The topics addressed in these templates are Malware Attack, Emergency Report, Capability Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Categorization Worksheet For System Improving Cybersecurity With Incident Demonstration PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information.Get a simple yet stunning designed Categorization Worksheet For System Improving Cybersecurity With Incident Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Categorization Worksheet For System Improving Cybersecurity With Incident Demonstration PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
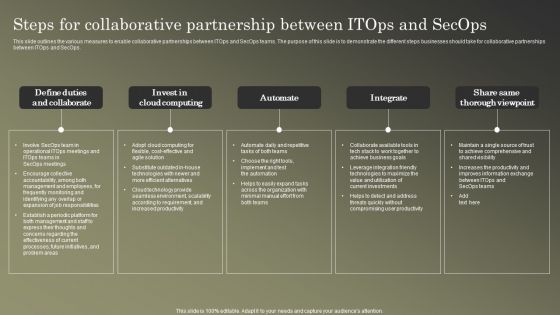
Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF
This slide outlines the various measures to enable collaborative partnerships between ITOps and SecOps teams. The purpose of this slide is to demonstrate the different steps businesses should take for collaborative partnerships between ITOps and SecOps. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Operations Cybersecops Steps For Collaborative Partnership Background PDF today and make your presentation stand out from the rest.
Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF
This slide represents the main advantages of deploying security operations in an organization. The purpose of this slide is to showcase the critical benefits of SecOps implementation, covering an increased workforce to deal with threats, fewer buggy apps, quick response to threats, fewer security breaches, and so on. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cybersecurity Operations Cybersecops Benefits Of Implementing Secops Icons PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF

Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF
This slide depicts the overview of a case study of the pharmaceutical company. The purpose of this slide is to highlight the clients requirements, services offered by the SecOps service provider and the impact of provided solutions on the client company. Create an editable Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cybersecurity Operations Cybersecops Case Study Pharmaceutical Company Summary PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF
This slide represents the comparison between the security operations center and DevOps. The purpose of this slide is to highlight the key differences between SecOps and DevOps teams based on definition, scope, approach, way of processing, goal and implementation of changes. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cybersecurity Operations Cybersecops Secops Vs Devops Slides PDF today and make your presentation stand out from the rest.
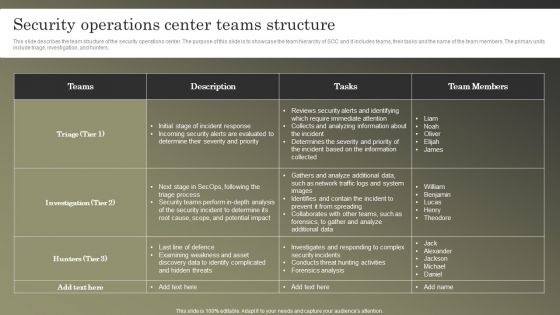
Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF
This slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF can be your best option for delivering a presentation. Represent everything in detail using Cybersecurity Operations Cybersecops Security Operations Center Teams Structure Introduction PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
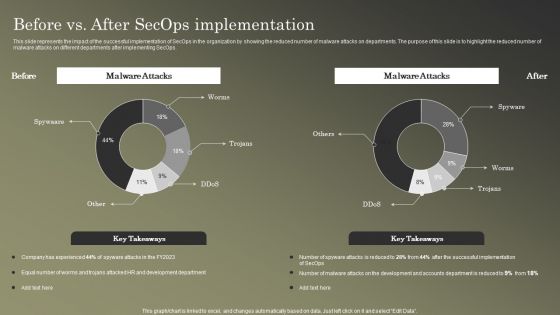
Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF
This slide represents the impact of the successful implementation of SecOps in the organization by showing the reduced number of malware attacks on departments. The purpose of this slide is to highlight the reduced number of malware attacks on different departments after implementing SecOps. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops Before Vs After Secops Implementation Inspiration PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Safety Initiatives Setting Scenario For Cybersecurity Control Inspiration PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative data safety initiatives setting scenario for cybersecurity control inspiration pdf bundle. Topics like scenario, technical controls, management controls, operational controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Major Benefits Of NIST Cybersecurity Framework Elements PDF
The slide highlights various benefits of Nist cyber security framework. It includes procedural consistency, removes silos, compliance and trust. Presenting Major Benefits Of NIST Cybersecurity Framework Elements PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Procedural Consistency, Removes Silos, Compliance . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Cybersecurity Challenges With Required Actions Mockup PDF
This is a major cybersecurity challenges with required actions mockup pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical actions needed, protecting privacy and sensitive data, protecting cyber critical infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Scorecard 30 60 90 Days Plan Topics PDF
This is a cybersecurity risk scorecard 30 60 90 days plan topics pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 8 essential information security risk scorecard for organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Minimize Administrative And Staff Privileges Ppt Layouts Grid PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting cybersecurity minimize administrative and staff privileges ppt layouts grid pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home