Cybersecurity Icons
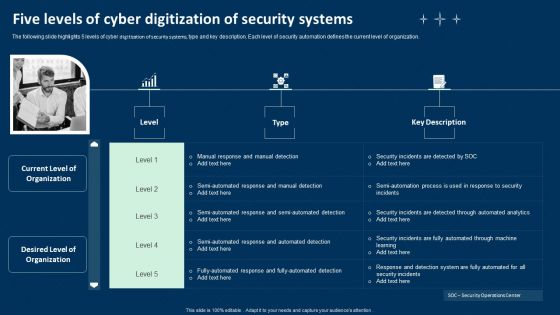
Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF
The following slide highlights 5 levels of cyber digitization of security systems, type and key description. Each level of security automation defines the current level of organization. Presenting Five Levels Of Cyber Digitization Of Security Systems Ppt Infographics Graphics Tutorials PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
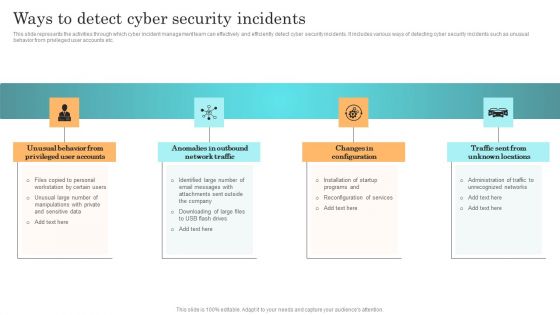
Incident Response Techniques Deployement Ways To Detect Cyber Security Incidents Infographics PDF

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
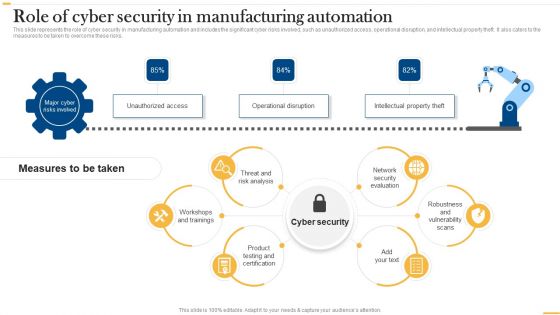
Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Are you searching for a Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF from Slidegeeks today.
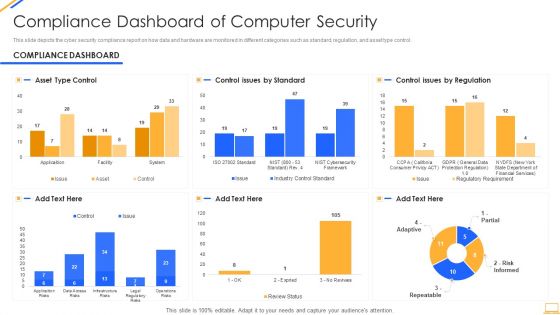
Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
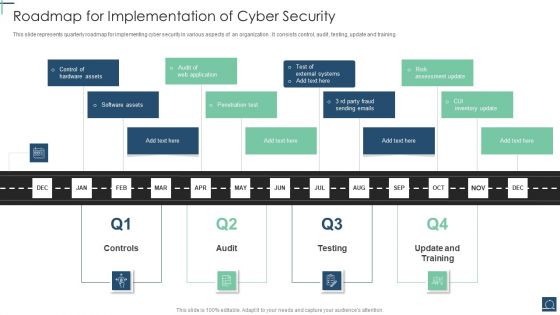
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
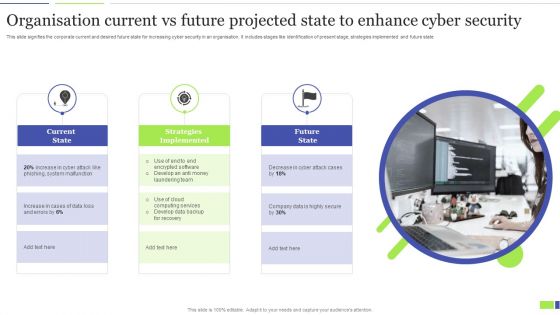
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
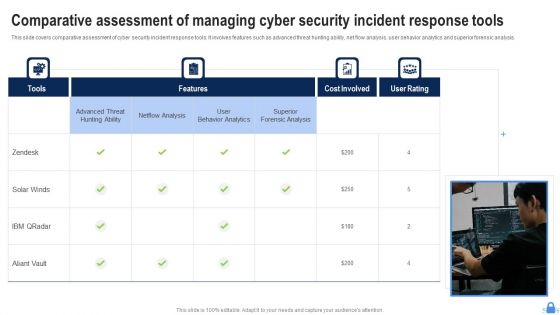
Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
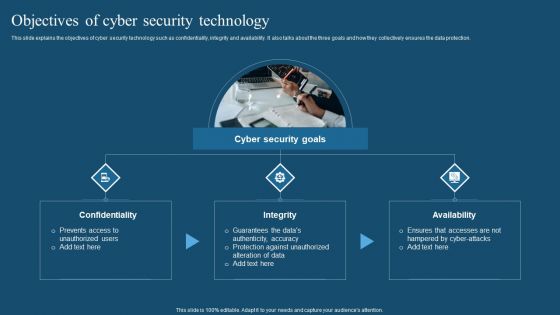
Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Three Lines Of Defense Border Model For Cyber Security Designs PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Presenting Three Lines Of Defense Border Model For Cyber Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security, Three Lines, Border Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Retrieve professionally designed Incident Response Techniques Deployement Impact Of Implementing Cyber Security Incident Management Formats PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
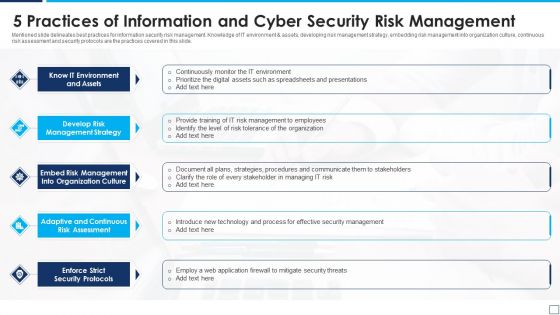
5 Practices Of Information And Cyber Security Risk Management Graphics PDF
Mentioned slide delineates best practices for information security risk management. Knowledge of IT environment and assets, developing risk management strategy, embedding risk management into organization culture, continuous risk assessment and security protocols are the practices covered in this slide. Presenting 5 practices of information and cyber security risk management graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including know it environment and assets, develop risk management strategy, enforce strict security protocols. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cyber Exploitation IT Dashboard For Threat Tracking Topics PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative cyber exploitation it dashboard for threat tracking topics pdf bundle. Topics like dashboard for threat tracking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF
This slide shows best practices for detecting insider threats. It provides information such as heavy screening of new hires, apply user access management, conduct security awareness training, monitor employee behavior, etc. Presenting Key Initiatives To Detect Insider Threat In Cyber Security Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Screen Carefully, Secure Access, Conduct Training. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
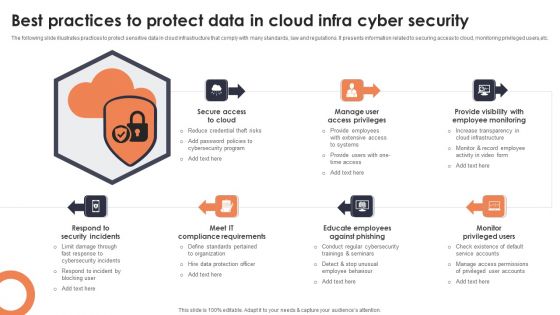
Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Desktop Security Management Elements Of Computer Security Operational Security Themes PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a desktop security management elements of computer security operational security themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, resources, require, security, plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
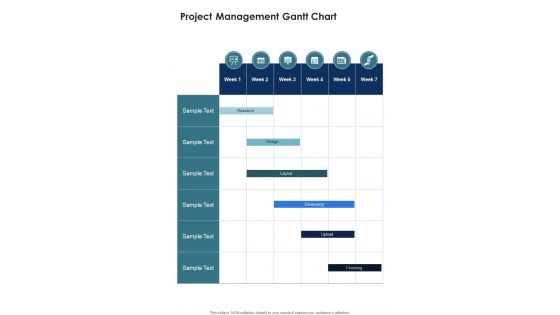
Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Project Management Gantt Chart Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.
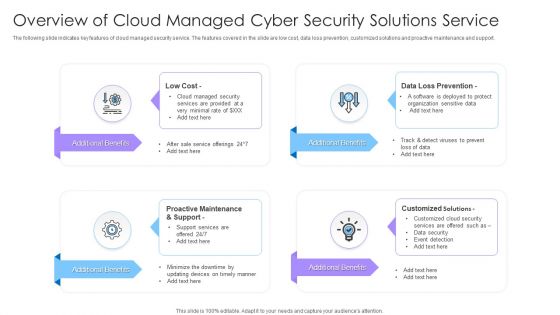
Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF
The following slide indicates key features of cloud managed security service. The features covered in the slide are low cost, data loss prevention, customized solutions and proactive maintenance and support. Presenting Overview Of Cloud Managed Cyber Security Solutions Service Ppt Portfolio Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Low Cost, Customized Solutions, Additional Benefits. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
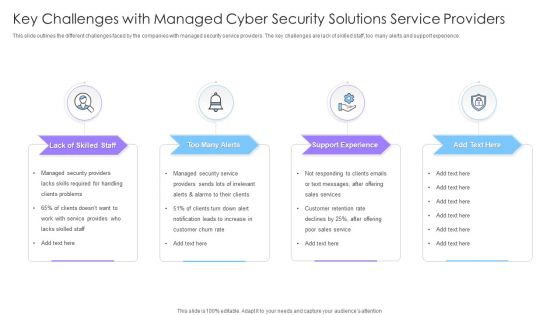
Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF
This slide outlines the different challenges faced by the companies with managed security service providers. The key challenges are lack of skilled staff, too many alerts and support experience. Presenting Key Challenges With Managed Cyber Security Solutions Service Providers Ppt Pictures Visual Aids PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Too Many Alerts, Support Experience, Lack Skilled Staff. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
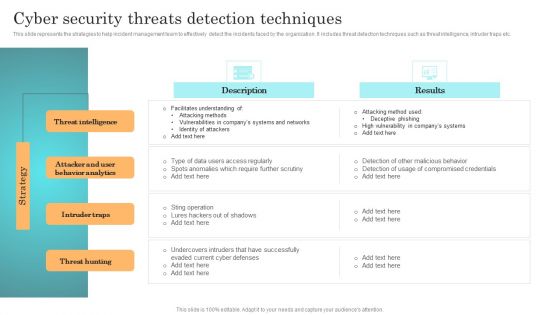
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

Query Slide Diagram For Designing A Secure Network Perimeter Diagrams PDF
Showcasing this set of slides titled query slide diagram for designing a secure network perimeter diagrams pdf. The topics addressed in these templates are query slide diagram for designing a secure network perimeter. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Computing Security Networking Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cloud computing security networking ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
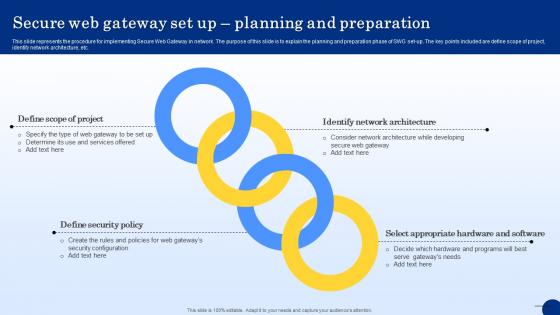
Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Get a simple yet stunning designed Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
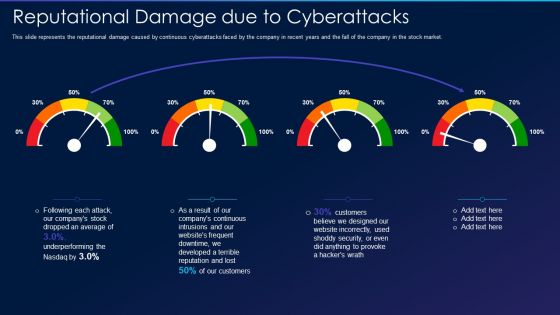
Cyber Exploitation IT Reputational Damage Due To Cyberattacks Professional PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an awe inspiring pitch with this creative cyber exploitation it reputational damage due to cyberattacks professional pdf bundle. Topics like continuous, developed, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
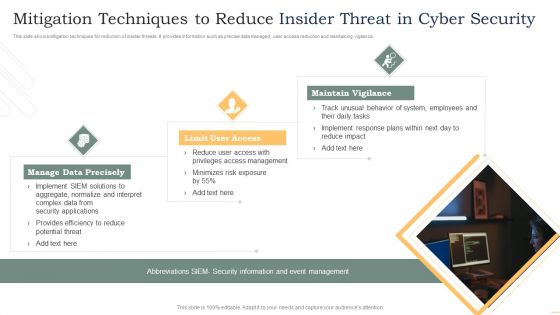
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
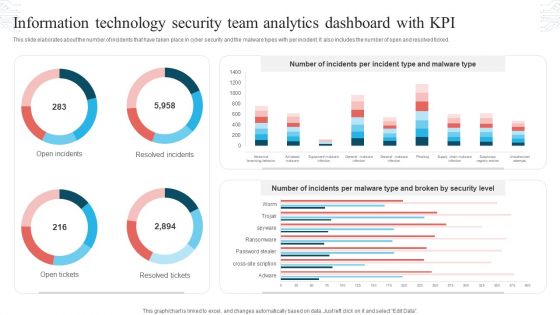
Information Technology Security Team Analytics Dashboard With KPI Themes PDF
This slide elaborates about the number of incidents that have taken place in cyber security and the malware types with per incident. It also includes the number of open and resolved ticked. Showcasing this set of slides titled Information Technology Security Team Analytics Dashboard With KPI Themes PDF. The topics addressed in these templates are Open Incidents, Resolved Incidents, Open Tickets, Resolved Tickets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Multiple Challenges Of Business Cyber Threat Prevention Sample PDF
The following slide represent the statistical data of various cyber safety challenges reported by business and organizations which helps to determine the most vulnerable one. Major areas are information security, business agility, automation, integration, etc. Showcasing this set of slides titled Multiple Challenges Of Business Cyber Threat Prevention Sample PDF. The topics addressed in these templates are Key Takeaways, Cyber Safety, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the thirty slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.
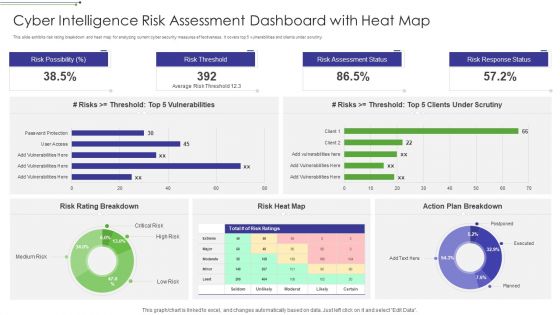
Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF
This slide depicts different points leading to failures to set up an effective security system. It includes the cost borne by company due to failures in log management, communication over unauthorized ports, asset inventory, failures of anti-malware software, etc.Showcasing this set of slides titled Cost Breakdown Multiple Points Incurred On Cyber Security System Of Failures Ppt PowerPoint Presentation Visual Aids Portfolio PDF. The topics addressed in these templates are Management Failures, Irregular Penetration, Expense Borne. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF
This slide highlights dashboard to identify and track security threats occurred in the company. The purpose of this template is to provide information to the management about severities of the incidents along with risk rating in form of heat map. Showcasing this set of slides titled Cyber Security Cases Action Plan Risk Tracking Dashboard For Response Ppt PowerPoint Presentation File Graphics Example PDF. The topics addressed in these templates are Risk Heat Map, Action Plan Breakdown, Risk Rating Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Arrow 5 Stages Diverging Process Diagram Circular Network PowerPoint Templates
We present our arrow 5 stages diverging process diagram Circular Network PowerPoint templates.Present our Arrows PowerPoint Templates because you can present your opinions in this field using our impressive templates. Present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download and present our Shapes PowerPoint Templates because they are Designed to attract the attention of your audience. Download our Process and Flows PowerPoint Templates because you are the star of your enlightened team. Use our Flow charts PowerPoint Templates because it helps to anticipate the doubts and questions in the minds of your colleagues and enlighten them with your inspired strategy to garner desired success.Use these PowerPoint slides for presentations relating to Arrow, green ,brochure, business, button, catalog, chart, circle, company, cross, design, diagram, direction, financial, glossy, goals,graph, green, junction, management, market, marketing, model, multicolored, multiple, navigation, network, options, orange, pie, plan, presentation, process, gray, sphere, statistics . The prominent colors used in the PowerPoint template are Green, Black, White. You can be sure our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Fantastic. Presenters tell us our catalog PowerPoint templates and PPT Slides are Gorgeous. We assure you our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are Cheerful. Customers tell us our catalog PowerPoint templates and PPT Slides are Versatile. Presenters tell us our arrow 5 stages diverging process diagram Circular Network PowerPoint templates are designed by professionals You can be sure our catalog PowerPoint templates and PPT Slides are Graceful.

Desktop Security Management Elements Of Computer Security Cloud Security Diagrams PDF
This slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a desktop security management elements of computer security cloud security diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like applications, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
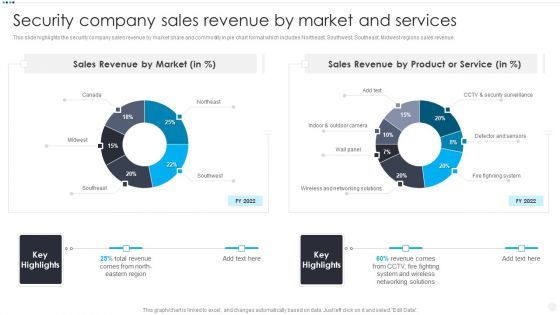
Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF
This slide highlights the security company sales revenue by market share and commodity in pie chart format which includes Northeast, Southwest, Southeast, Midwest regions sales revenue. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Sales Revenue By Market Themes PDF bundle. Topics like Sales Revenue Market, Sales Revenue Product, Wireless And Networking can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Of Data And Networks In Concurrent Computing Ppt File Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. This is a security of data and networks in concurrent computing ppt file themes pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computing, transit, storage, system, protection, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
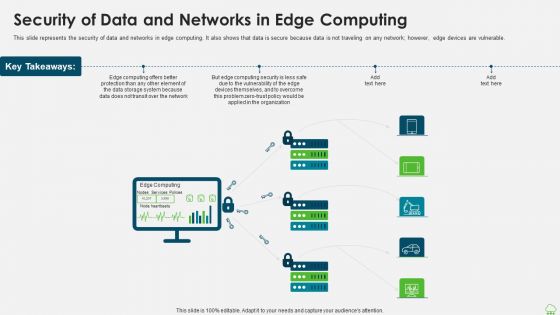
Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
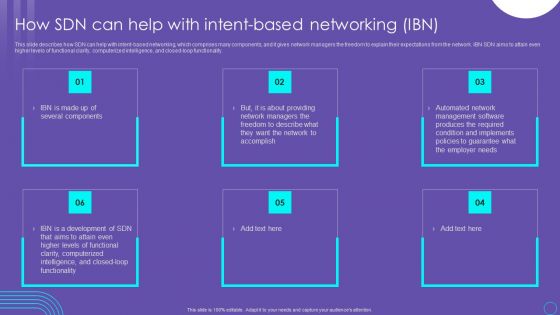
SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF
This slide covers the strategies to overcome network complexities and increase reliability, Enhanced user experience, increasing efficiency and high security. Deliver an awe inspiring pitch with this creative Strategies For Every Phase Of The Cloud Journey To Remove Network Complexity Download PDF bundle. Topics like Productivity, Simplifying Security, Environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Supply Chain Risk Management Dashboard Structure PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Supply Chain Risk Management Dashboard Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Web Security Testing Approach Diagram Powerpoint Show
This is a web security testing approach diagram powerpoint show. This is a six stage process. The stages in this process are penetration testing, virus, war dialing, password cracking, log view, networking scanning.
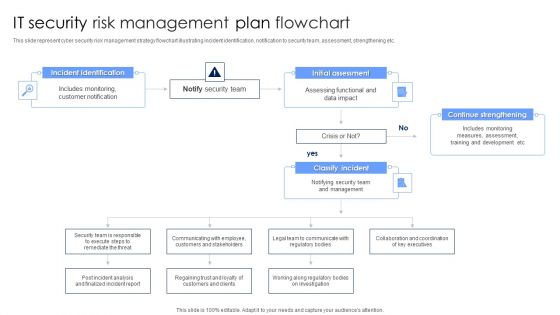
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SDN Security Architecture Why Is An Software Defined Network Used Themes PDF
This slide depicts why the software defined network is used, including the increase in sales, excellent customer service, reduction in expenses, and less hardware is used, making room for more space and less power consumption. Present like a pro with SDN Security Architecture Why Is An Software Defined Network Used Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Business Diagram Server Virtulization Thin Client Storage And Database Ppt Slide
This image slide displays network of servers. This image slide has been designed with graphic of server workstation with concepts of server virtualization storage and thin client. This image slide will enhance the quality of your presentations.

Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
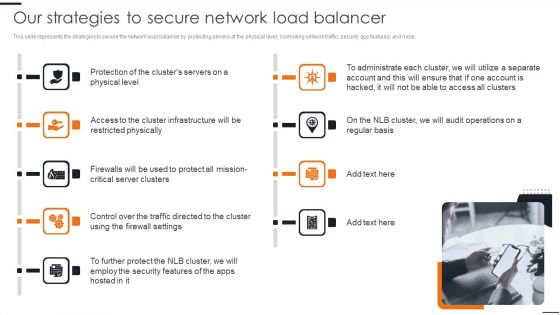
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Retrieve professionally designed Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
PowerPoint Theme Flow Diverging Arrow Process Diagram Ppt Cycle Spoke Network Slides
We present our powerpoint theme flow diverging arrow process diagram ppt Cycle Spoke Network Slides.Use our Process and Flows PowerPoint Templates because it helps you to display your ideas and thoughts. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Shapes PowerPoint Templates because this is a wonderful graphics to see the smiles of happiness spread as your audience realizes the value of your words. Use our Success PowerPoint Templates because different people with differing ideas and priorities perform together to score. Download our Flow Charts PowerPoint Templates because different personalities, different abilities but formidable together.Use these PowerPoint slides for presentations relating to Arrows, Business, Central, Centralized, Chart, Circle, Circular, Circulation, Concept, Conceptual, Illustration, Organization, Pointing, Process, Radial, Resource, Strategy, Template, Graphic, Group, Illustration, Process, Progress. The prominent colors used in the PowerPoint template are Red, Gray, White. People tell us our powerpoint theme flow diverging arrow process diagram ppt Cycle Spoke Network Slides are incredible easy to use. Professionals tell us our Concept PowerPoint templates and PPT Slides are Second to none. Customers tell us our powerpoint theme flow diverging arrow process diagram ppt Cycle Spoke Network Slides are Wistful. Use our Chart PowerPoint templates and PPT Slides are Spiffy. We assure you our powerpoint theme flow diverging arrow process diagram ppt Cycle Spoke Network Slides are Cheerful. Professionals tell us our Central PowerPoint templates and PPT Slides are Efficient.
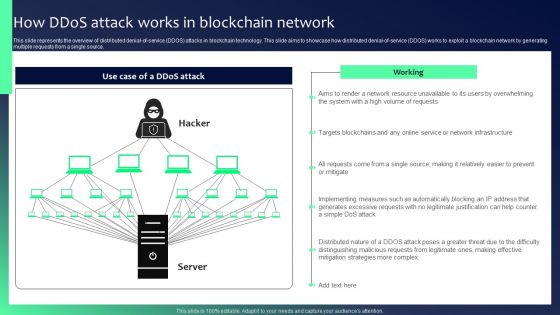
Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF
This slide represents the overview of distributed denial-of-service DDOS attacks in blockchain technology. This slide aims to showcase how distributed denial-of-service DDOS works to exploit a blockchain network by generating multiple requests from a single source. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Blockchain Security Solutions Deployment How Ddos Attack Works In Blockchain Network Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home