Cyber Security Roadmap
Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF
Presenting Cybersecurity Training Workshop On Security Breach Trends Icon Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cybersecurity Training, Workshop On Security, Breach Trends Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Telecommunications Network Security Ppt PowerPoint Presentation Summary Microsoft Cpb
Presenting this set of slides with name telecommunications network security ppt powerpoint presentation summary microsoft cpb. This is a three stage process. The stages in this process are telecommunications network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
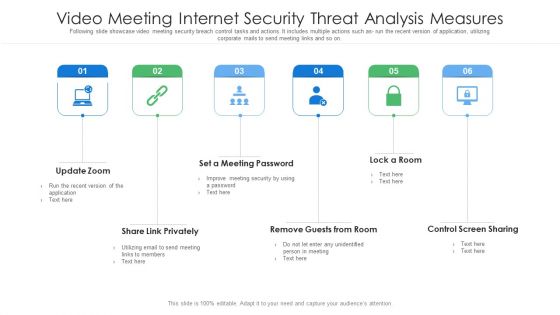
Video Meeting Internet Security Threat Analysis Measures Brochure PDF
Following slide showcase video meeting security breach control tasks and actions. It includes multiple actions such as- run the recent version of application, utilizing corporate mails to send meeting links and so on. Persuade your audience using this video meeting internet security threat analysis measures brochure pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including video meeting internet security threat analysis measures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
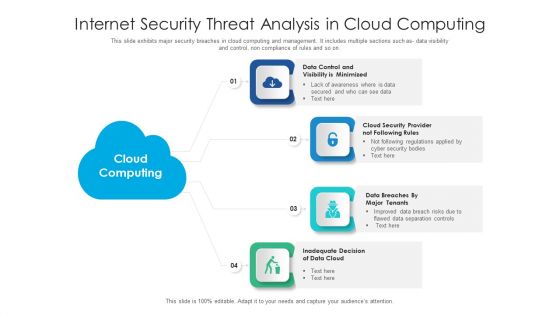
Internet Security Threat Analysis In Cloud Computing Information PDF
This slide exhibits major security breaches in cloud computing and management. It includes multiple sections such as- data visibility and control, non compliance of rules and so on. Presenting internet security threat analysis in cloud computing information pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including data cloud, cloud security, data control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
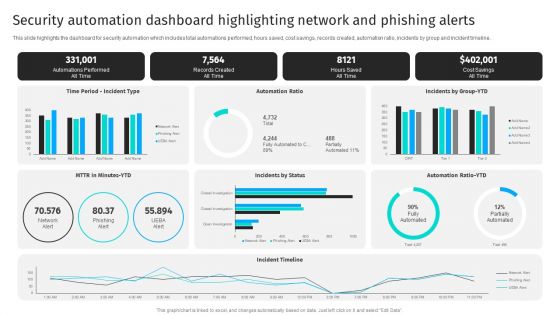
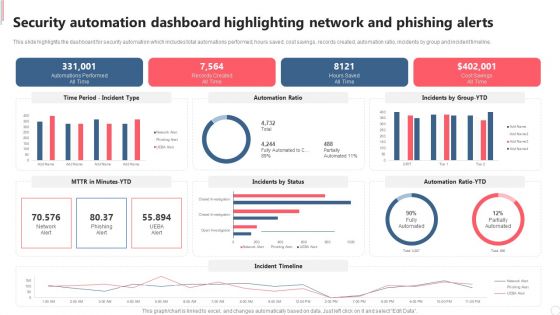
Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline.Get a simple yet stunning designed Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Automation Dashboard Highlighting Network And Phishing Alerts Professional PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.
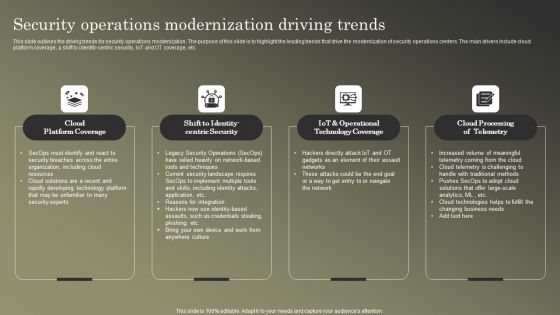
Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF
This slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Present like a pro with Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
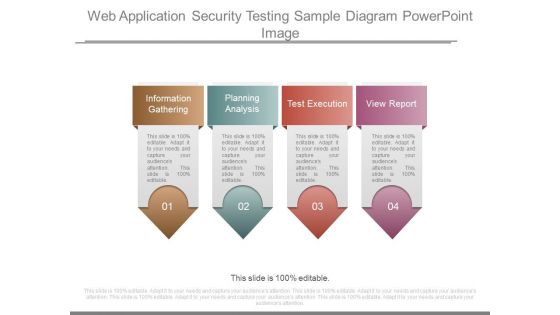
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.

Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Web Services Security Ppt PowerPoint Presentation Styles Gallery Cpb
Presenting this set of slides with name web services security ppt powerpoint presentation styles gallery cpb. This is an editable Powerpoint five stages graphic that deals with topics like web services security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices For Business To Increase Online Security Introduction PDF
This slide highlights best practices for business to increase digital safety which help prevent and mitigate inherent risk. It provides information about antivirus, software upgradation, suspicious emails, VPN and 2 factor authentication. Presenting Best Practices For Business To Increase Online Security Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Vulnerabilities, Factor Authentication, Avoid Suspicious Emails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Process To Manage Firms Sensitive Data Mockup PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Boost your pitch with our creative Information Security Process To Manage Firms Sensitive Data Mockup PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
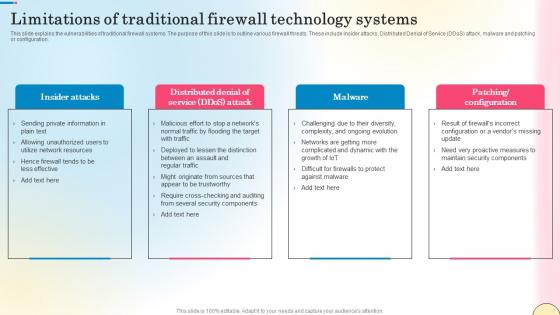
Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf
This slide explains the vulnerabilities of traditional firewall systems. The purpose of this slide is to outline various firewall threats. These include insider attacks, Distributed Denial of Service DDoS attack, malware and patching or configuration. Presenting this PowerPoint presentation, titled Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Limitations Of Traditional Firewall Technology Systems Network Security Pictures Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
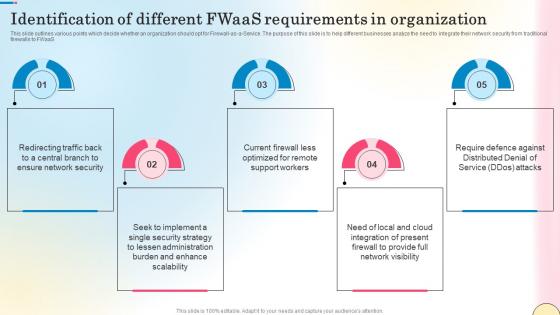
Identification Of Different Fwaas Requirements In Network Security Template Pdf
This slide outlines various points which decide whether an organization should opt for Firewall-as-a-Service. The purpose of this slide is to help different businesses analyze the need to integrate their network security from traditional firewalls to FWaaS. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Identification Of Different Fwaas Requirements In Network Security Template Pdf from Slidegeeks and deliver a wonderful presentation.
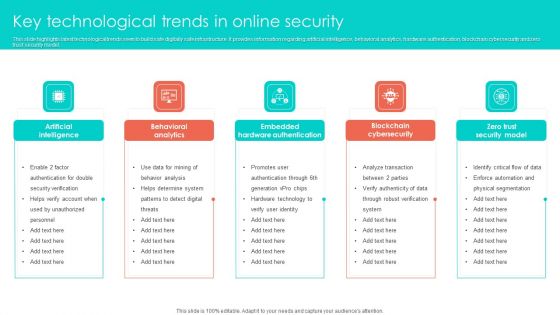
Key Technological Trends In Online Security Clipart PDF
This slide highlights latest technological trends seen to build safe digitally safe infrastructure. It provides information regarding artificial intelligence, behavioral analytics, hardware authentication, blockchain cybersecurity and zero trust security model. Persuade your audience using this Key Technological Trends In Online Security Clipart PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Behavioral Analytics, Artificial Intelligence, Embedded Hardware Authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
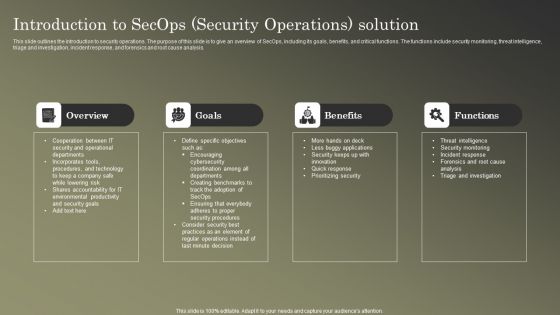
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cloud Network Security Threats And Solutions Infographics PDF
The slide showcases threats occurred due to data flowing between cloud service providers and organizations with their solutions. It includes lack of cloud security architecture and tactics, account hijacking , weak control plane , inadequate of identity, credentials, etc. Presenting Cloud Network Security Threats And Solutions Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats, Description, Solutions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF
This slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. The Cybersecurity Operations Cybersecops Security Operations Threat Management Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cybersecurity Security Framework In Cloud Computing Ppt Portfolio Grid PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a cybersecurity security framework in cloud computing ppt portfolio grid pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, identify, protect, detect, respond. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Checklist For Data Privacy Implementation Elements PDF
This slide represents the checklist for data privacy implementation, which includes ensuring that every employee in the firm is aware of data privacy, monitoring the network for odd behavior. Presenting this PowerPoint presentation, titled Information Security Checklist For Data Privacy Implementation Elements PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security Checklist For Data Privacy Implementation Elements PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security Checklist For Data Privacy Implementation Elements PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Extended Detection And Response For Endpoint Security Detection Clipart PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Extended Detection And Response For Endpoint Security Detection Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Extended Detection And Response For Endpoint Security Detection Clipart PDF today and make your presentation stand out from the rest.
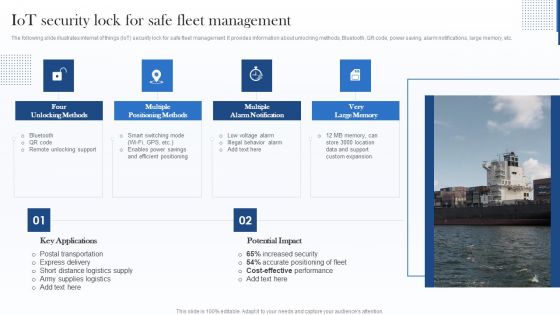
Iot Security Lock For Safe Fleet Management Sample PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Presenting Iot Security Lock For Safe Fleet Management Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multiple Positioning Methods, Multiple Alarm Notification, Very Large Memory. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
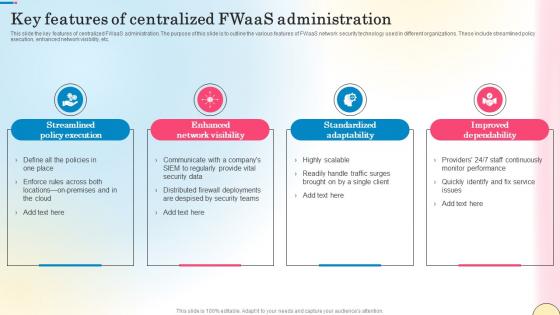
Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf
This slide the key features of centralized FWaaS administration. The purpose of this slide is to outline the various features of FWaaS network security technology used in different organizations. These include streamlined policy execution, enhanced network visibility, etc. Slidegeeks has constructed Key Features Of Centralized Fwaas Administration Network Security Introduction Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Extended Detection And Response For Endpoint Security Detection Themes PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Boost your pitch with our creative Extended Detection And Response For Endpoint Security Detection Themes PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
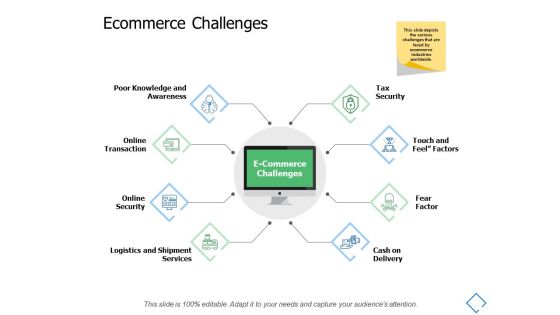
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Styles Gridlines
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation styles gridlines. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Icon Show
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation icon show. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Welcome to our selection of the Security Automation Dashboard Highlighting Network And Phishing Alerts Demonstration PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. This modern and well arranged Security Automation Dashboard Highlighting Network And Phishing Alerts Microsoft PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF
This slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. There are so many reasons you need a Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
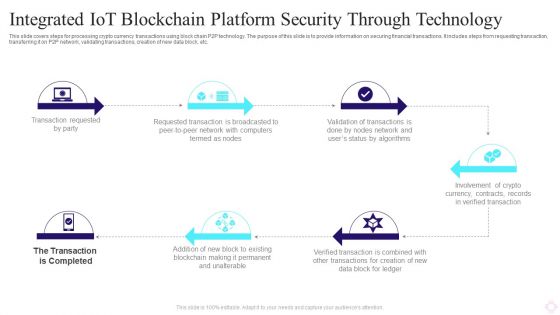
Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Framework Of IT Security Awareness Training Program Information PDF
This slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting Framework Of IT Security Awareness Training Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analyze, Plan, Deploy, Measure, Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
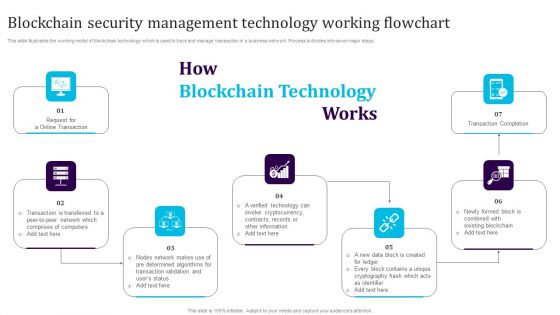
Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
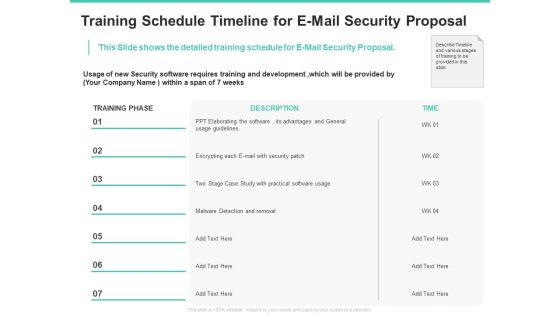
Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
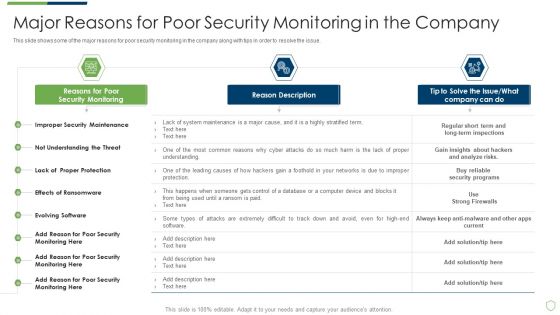
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
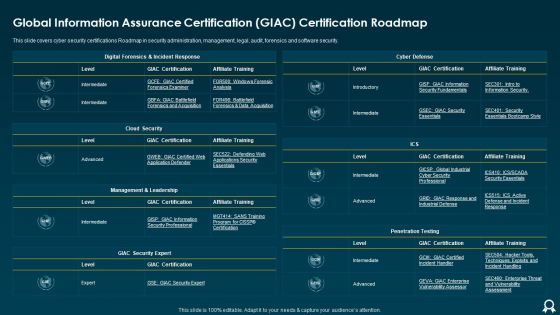
Global Information Assurance Certification GIAC Certification Roadmap Formats PDF
This slide covers cyber security certifications Roadmap in security administration, management, legal, audit, forensics and software security. Deliver an awe inspiring pitch with this creative Global Information Assurance Certification GIAC Certification Roadmap Formats PDF bundle. Topics like Cloud Security, Cyber Defense, Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Best Practices For Tokenization In Data Security Securing Your Data Ppt Example
The purpose of this slide is to highlight the best approaches for tokenization. The practices include broadening data tokenization scope, regularly revise policies, effective cyber security, etc. There are so many reasons you need a Best Practices For Tokenization In Data Security Securing Your Data Ppt Example The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
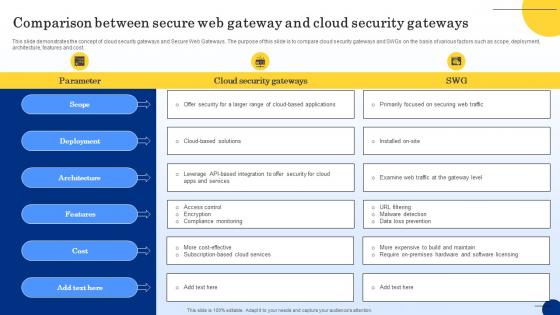
Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
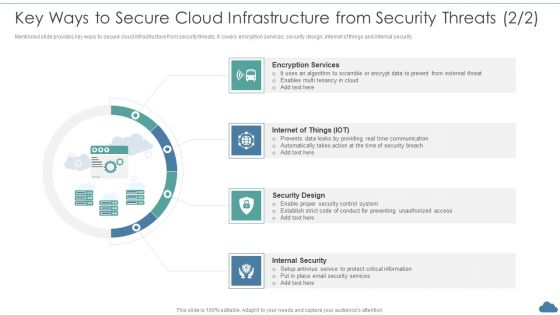
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
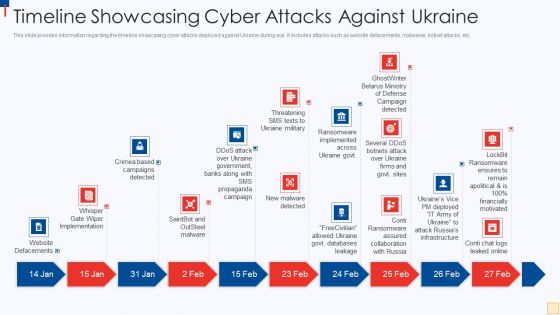
Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF
This slide provides information regarding the timeline showcasing cyber attacks deployed against Ukraine during war. It includes attacks such as website defacements, malwares, botnet attacks, etc. Presenting Ukraine Vs Russia Examining Timeline Showcasing Cyber Attacks Against Ukraine Ideas PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Website Defacements, Saintbot And Outsteel Malware, New Malware Detected, Threatening SMS Texts To Ukraine Military. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
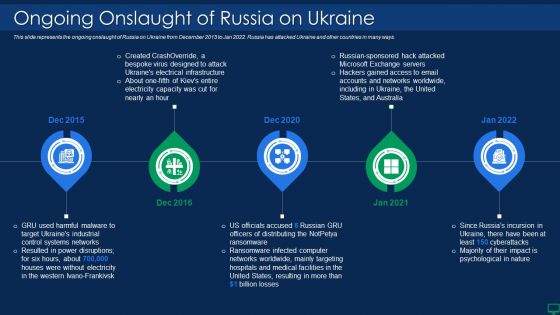
Russian Cyber Attacks On Ukraine IT Ongoing Onslaught Of Russia Structure PDF
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. This is a russian cyber attacks on ukraine it ongoing onslaught of russia structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, industrial, networks, email. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
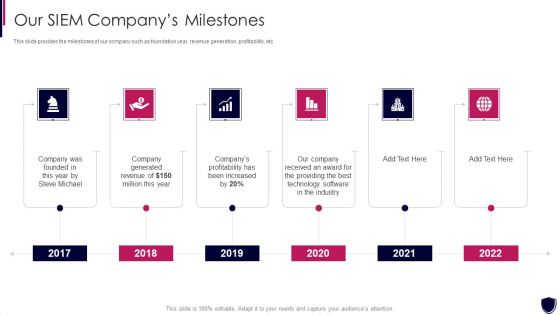
Enhancing Cyber Safety With Vulnerability Administration Our SIEM Companys Milestones Demonstration PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. This is a enhancing cyber safety with vulnerability administration our siem companys milestones demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our siem companys milestones. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
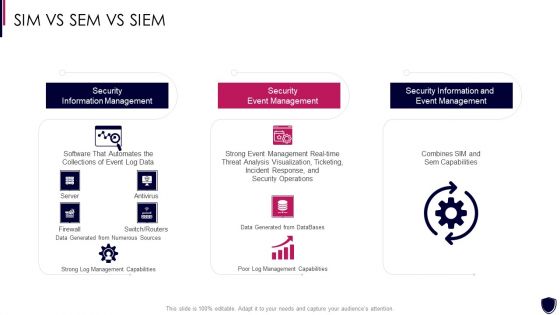
Enhancing Cyber Safety With Vulnerability Administration SIM Vs SEM Vs SIEM Brochure PDF
Presenting enhancing cyber safety with vulnerability administration sim vs sem vs siem brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security information management, security event management, security information and event management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
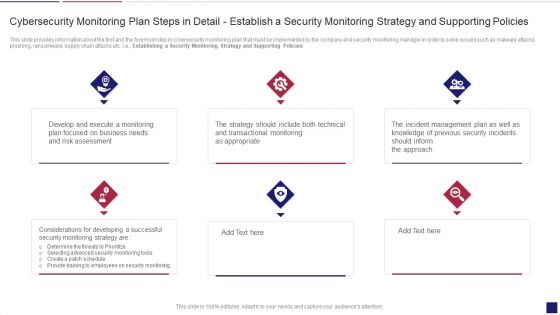
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Policies Inspiration PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Presenting continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring policies inspiration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Market Trends Sample PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. Presenting continuous development evaluation plan eliminate cyber attacks current market trends sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like increasing digitization of sensitive data, general data protection laws, data breach notification laws. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
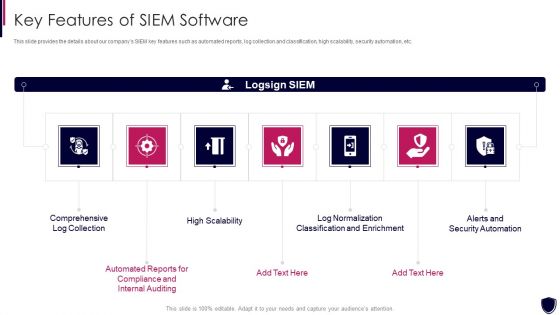
Enhancing Cyber Safety With Vulnerability Administration Key Features Of SIEM Software Ideas PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. This is a enhancing cyber safety with vulnerability administration key features of siem software ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comprehensive log collection, alerts and security automation, log normalization classification and enrichment, high scalability, internal auditing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Timeline To Implement Firewall As A Service Technology Network Security Template Pdf
This slide represents the timeline to implement Firewall as a Service technology. The main components include Analyse FWaaS objectives and needs, Select most suitable FWaaS providers and solutions, implement and test the FWaaS service, etc. Slidegeeks is here to make your presentations a breeze with Timeline To Implement Firewall As A Service Technology Network Security Template Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf
This slide represents the steps taken by cyber security incident management teams of varied enterprises in order to minimize its impact on business operations. It includes steps such as hire skilled individuals etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Statistical Data Supporting Steps Taken To Enhance Cyber Ppt Powerpoint Presentation File Outline Pdf from Slidegeeks and deliver a wonderful presentation.
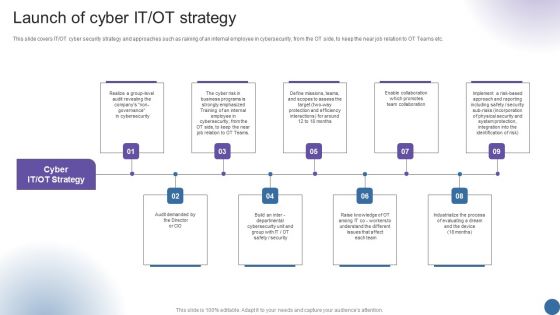
Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Launch Of Cyber IT OT Strategy Managing Organizational Transformation Sample PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategy, Launch Of Cyber, Business Programs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Cyber Safety Tips Protection Against Cyberattacks Ppt Styles Gallery PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a cybersecurity cyber safety tips protection against cyberattacks ppt styles gallery pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
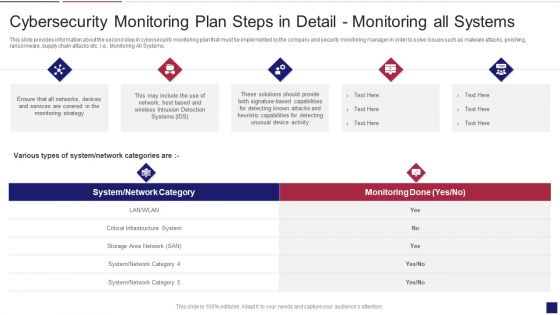
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Systems Graphics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring All Systems. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring systems graphics pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home