Cyber Security Risk
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
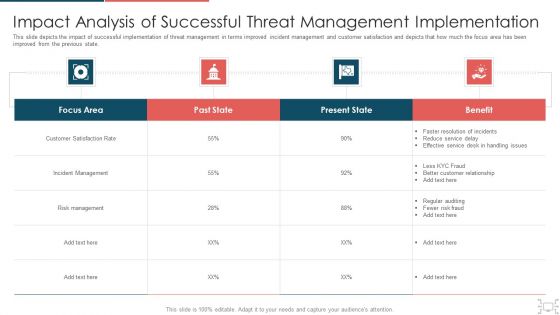
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
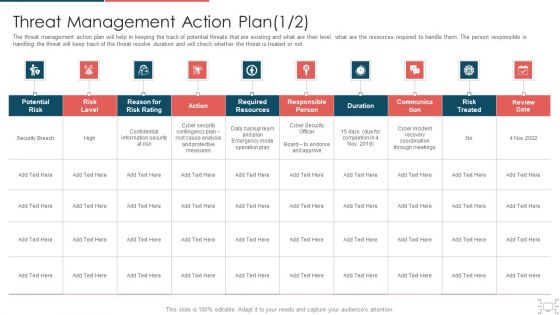
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Various Types Of Workplace Violence And Threats Inspiration PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber security administration in organization various types of workplace violence and threats inspiration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like physical, threatening, behavior, stalking, harassment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
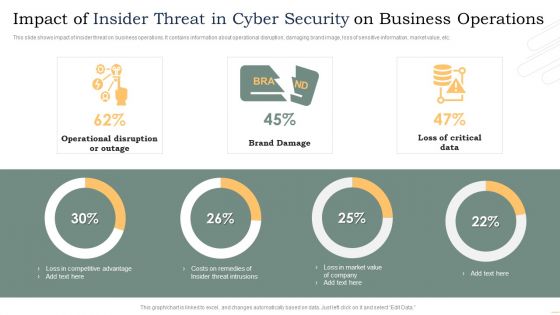
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
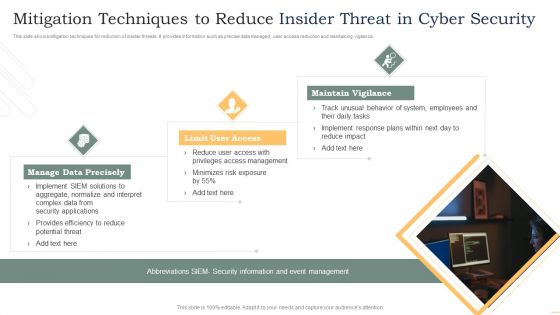
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
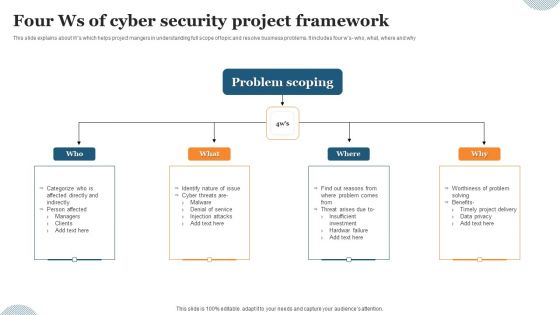
Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF
This slide explains about Ws which helps project mangers in understanding full scope of topic and resolve business problems. It includes four ws- who, what, where and why. Presenting Four Ws Of Cyber Security Project Framework Ppt Pictures Graphic Images PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Problem Scoping, Denial Service, Injection Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
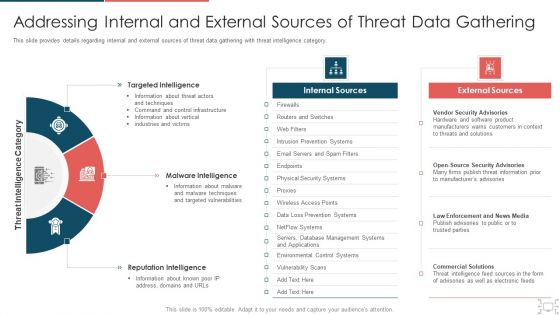
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
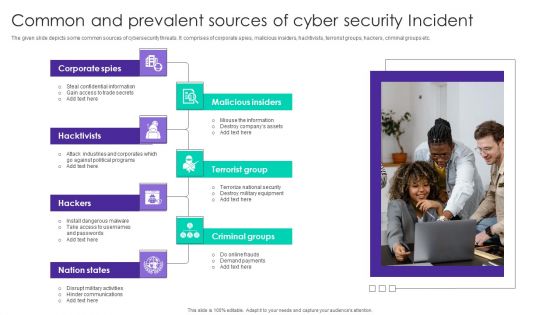
Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Risk Management And Incident Management Dashboard Icons PDF
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Insider Threat In Cyber Security Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the thirty slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Developing Cyber Security Threat Awareness Staff Training Program Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the seventy eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.
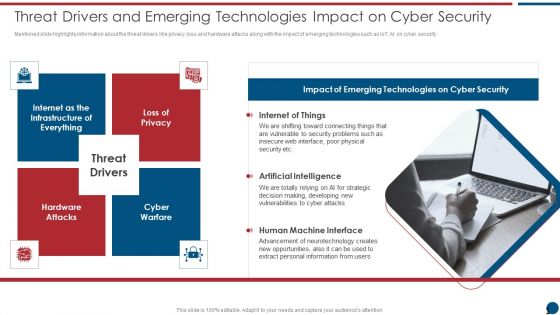
Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Management Template Presentation Background Images
This is a cyber management template presentation background images. This is a six stage process. The stages in this process are risk review, policy, audit, cyber security life cycle, implementation, administration.
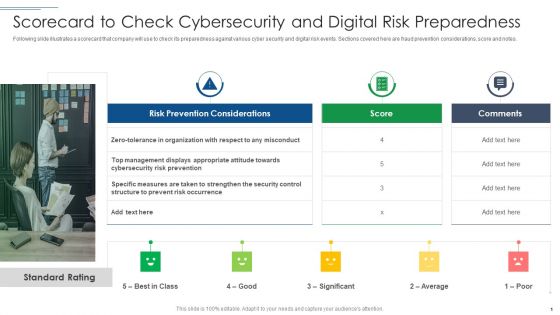
IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
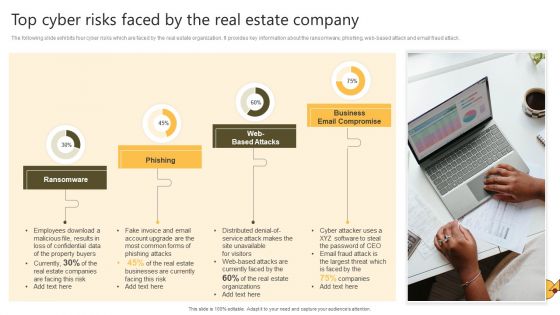
Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. The Successful Risk Administration Top Cyber Risks Faced By The Real Estate Company Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF
The following slide exhibits four cyber risks which are faced by the real estate organization. It provides key information about the ransomware, phishing, web-based attack and email fraud attack. Retrieve professionally designed Executing Risk Mitigation Top Cyber Risks Faced By The Real Estate Company Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Core Competencies Of Internet Security Threat Portrait Pdf
This slide showcase cyber security risk assessment with core competencies and constantly evolving digital infrastructure. It includes cyber transformation, financial operations, cloud computing and project management.Showcasing this set of slides titled Core Competencies Of Internet Security Threat Portrait Pdf The topics addressed in these templates are Cyber Transformation, Cloud Computing, Financial Operations All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Threat Compliance Dashboard With Risk And Standard Control Sample PDF
The following slide highlights the cyber security threat compliance dashboard with asset control. Standard control, regulation and risk control. Showcasing this set of slides titled cyber threat compliance dashboard with risk and standard control sample pdf. The topics addressed in these templates are asset control issue, standard control issue, regulation control issue. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
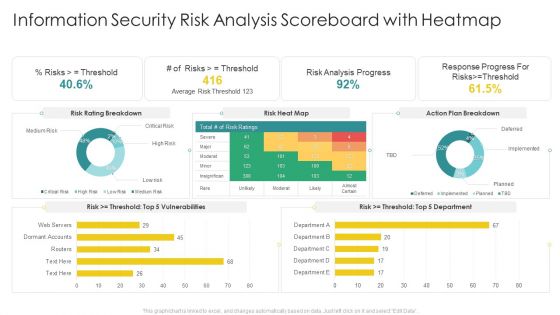
Cybersecurity Risk Scorecard Information Security Risk Analysis Scoreboard With Heatmap Elements PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity risk scorecard information security risk analysis scoreboard with heatmap elements pdf. Use them to share invaluable insights on information security risk analysis scoreboard with heatmap and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
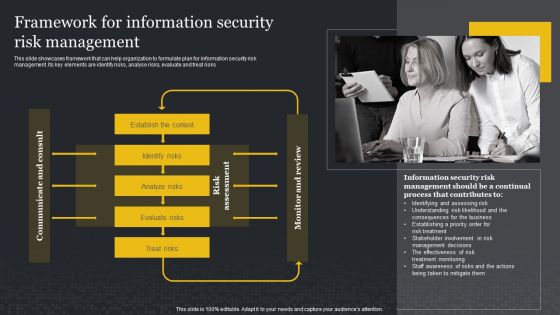
Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyse risks, evaluate and treat risks. Presenting this PowerPoint presentation, titled Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Framework For Information Security Risk Management Cybersecurity Risk Assessment Slides PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
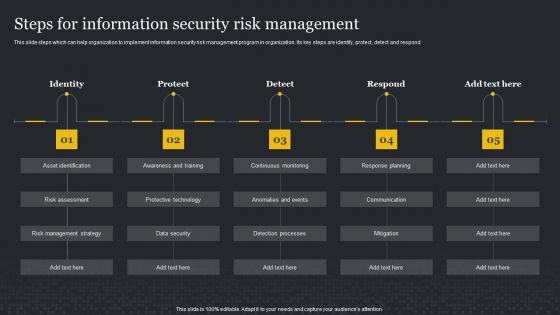
Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF bundle. Topics like Effects Of Damage, Vulnerability And Possible, Unauthorized Disclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
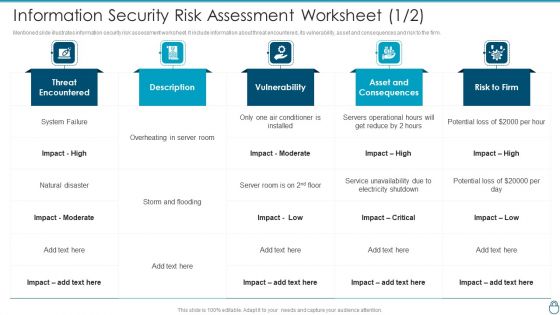
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
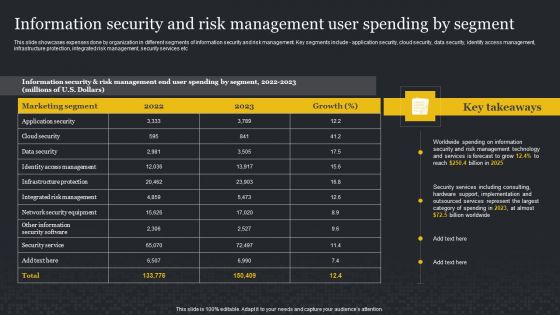
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
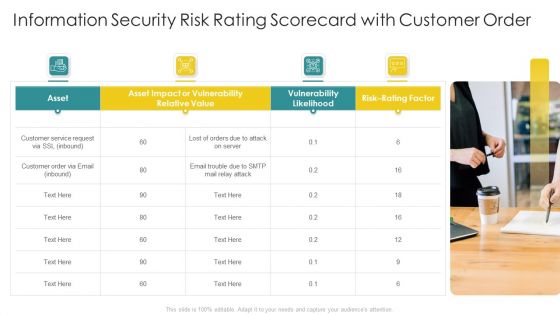
Cybersecurity Risk Scorecard Information Security Risk Rating Scorecard With Customer Order Slides PDF
This is a cybersecurity risk scorecard information security risk rating scorecard with customer order slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security risk rating scorecard with customer order. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Process For Information Security Risk Assessment Cybersecurity Risk Assessment Portrait PDF today and make your presentation stand out from the rest.

Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key component are risk management functions, required standard rating and actual standard rating. Explore a selection of the finest Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Estimated Impact Of Information Security Risk Management Plan Cybersecurity Risk Assessment Rules PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
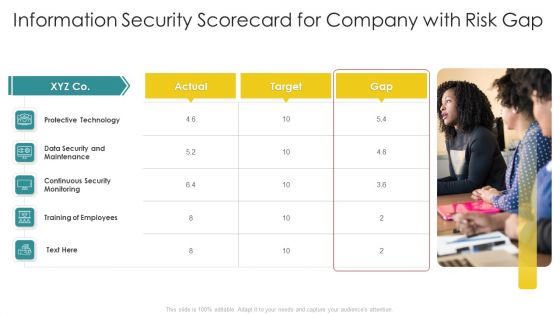
Cybersecurity Risk Scorecard Information Security Scorecard For Company With Risk Gap Professional PDF
Presenting cybersecurity risk scorecard information security scorecard for company with risk gap professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like protective technology, continuous security monitoring, training of employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Allocating Budget For Information Security Risk Management Programme Cybersecurity Risk Assessment Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline For Information Security Risk Management Training Cybersecurity Risk Assessment Pictures PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Risk Scorecard Company Information Security Risk Scorecard With Overall Rating Brochure PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity risk scorecard company information security risk scorecard with overall rating brochure pdf. Use them to share invaluable insights on safeguard, resiliency, reputation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
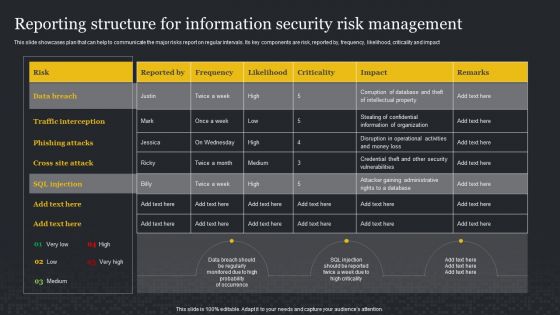
Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF can be your best option for delivering a presentation. Represent everything in detail using Reporting Structure For Information Security Risk Management Cybersecurity Risk Assessment Formats PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
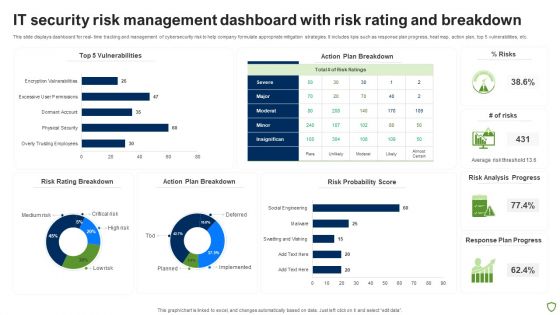
IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
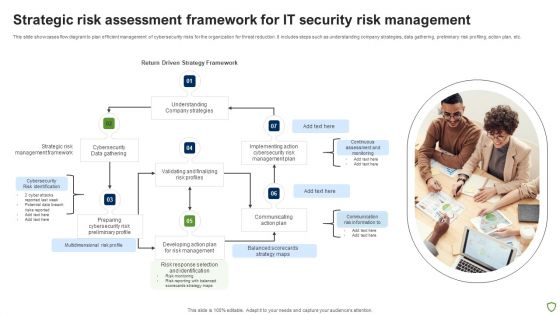
Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF
This slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting Strategic Risk Assessment Framework For IT Security Risk Management Ideas PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Strategic Risk, Cybersecurity, Management Framework, Data Gathering. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
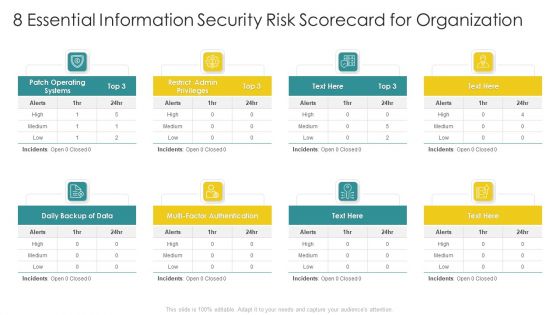
Cybersecurity Risk Scorecard 8 Essential Information Security Risk Scorecard For Organization Elements PDF
Presenting cybersecurity risk scorecard 8 essential information security risk scorecard for organization elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home