Cyber Security Risk Management

Vector Showing IT Security From Online Threat Ppt PowerPoint Presentation File Layout PDF
Presenting vector showing it security from online threat ppt powerpoint presentation file layout pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vector showing it security from online threat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Coder Checking Business Internet Security Threats Ppt PowerPoint Presentation Gallery Model PDF
Persuade your audience using this coder checking business internet security threats ppt powerpoint presentation gallery model pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including coder checking business internet security threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Dashboard For Threat Tracking In Information Technology Security Ppt Portfolio Shapes PDF
This slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver and pitch your topic in the best possible manner with this dashboard for threat tracking in information technology security ppt portfolio shapes pdf. Use them to share invaluable insights on dashboard for threat tracking in information technology security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Email Security Encryption And Data Loss Prevention Table Of Content Slides PDF
Presenting email security encryption and data loss prevention table of content slides pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like project context, our services, action plan, investment, about us, case study, our team, client testimonials, terms and conditions. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Kpis And Metrics Ppt PowerPoint Presentation Gallery Outline PDF
Showcasing this set of slides titled internet security kpis and metrics ppt powerpoint presentation gallery outline pdf. The topics addressed in these templates are threat detection, risk and compliance, services compliance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Elements Of Internet Security Model Ppt PowerPoint Presentation Slides Mockup PDF
Pitch your topic with ease and precision using this major elements of internet security model ppt powerpoint presentation slides mockup pdf. This layout presents information on business strategy, enterprise risk and compliance, policy and procedures frameworks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
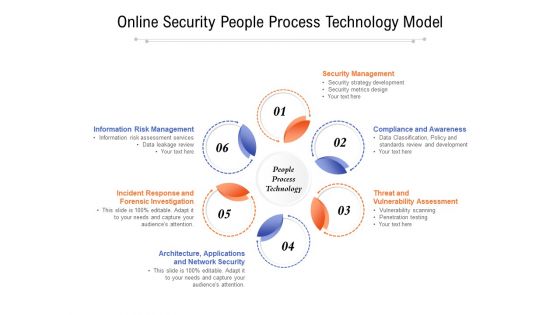
Online Security People Process Technology Model Ppt PowerPoint Presentation Slides Example Introduction PDF
Presenting online security people process technology model ppt powerpoint presentation slides example introduction pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including security management, compliance and awareness, threat and vulnerability assessment, architecture, applications, incident response and forensic investigation, information risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
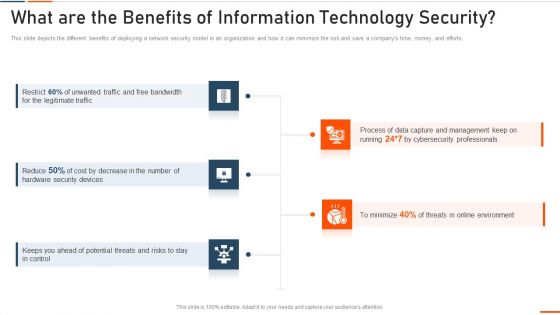
What Are The Benefits Of Information Technology Security Ppt Styles Model PDF
This slide depicts the different benefits of deploying a network security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting what are the benefits of information technology security ppt styles model pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like bandwidth, legitimate, security devices, potential . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cloud Based Email Security Market Industry Challenges Ppt Slides Structure PDF
Presenting this set of slides with name global cloud based email security market industry challenges ppt slides structure pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
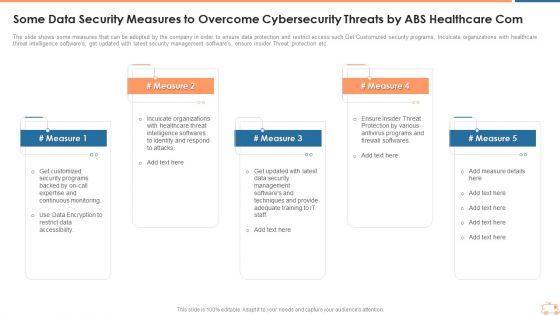
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
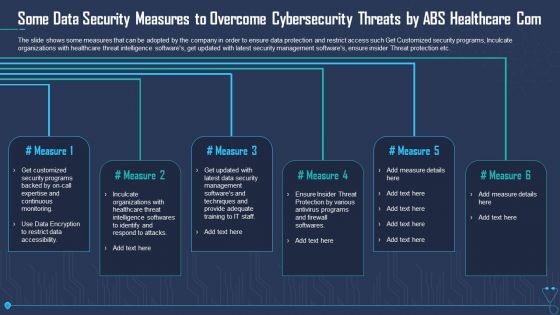
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does SD Wan Improve Security Wide Area Network Services Structure Pdf
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than How Does SD Wan Improve Security Wide Area Network Services Structure Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab How Does SD Wan Improve Security Wide Area Network Services Structure Pdf today and make your presentation stand out from the rest.
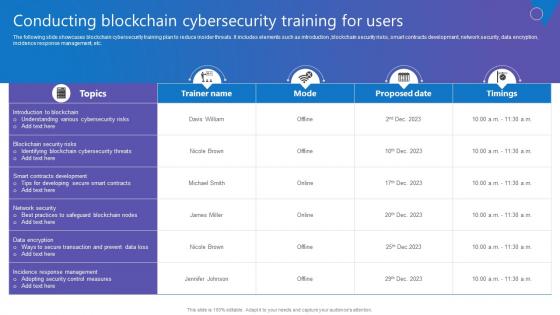
Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases blockchain cybersecurity training plan to reduce insider threats. It includes elements such as introduction ,blockchain security risks, smart contracts development, network security, data encryption, incidence response management, etc. Create an editable Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Conducting Blockchain Cybersecurity Comprehensive Guide To Blockchain Digital Security Summary Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
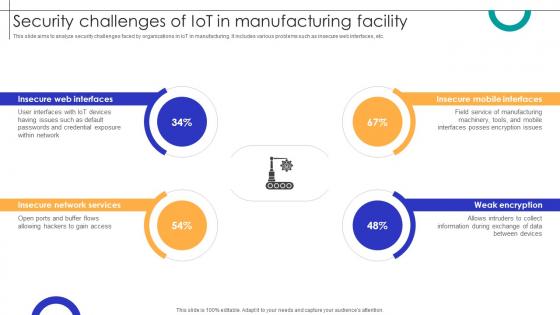
Security Challenges Of IOT In Manufacturing Facility Streamlining Production Ppt Example
This slide aims to analyze security challenges faced by organizations in IoT in manufacturing. It includes various problems such as insecure web interfaces, etc. Boost your pitch with our creative Security Challenges Of IOT In Manufacturing Facility Streamlining Production Ppt Example Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
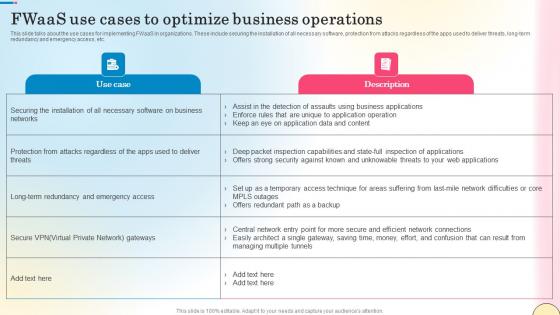
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Common Methods Used To Threaten IT Security IT Ppt Inspiration Rules PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten it security it ppt inspiration rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware, daniel of service, man in the middle, sql injection, phishing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V
This slide covers tips to enhance web wallet security for users. The purpose of this template is to provide recommendations to build strong security with practices such as regularly updating devices operating system, verifying the authenticity of websites, exercising caution when using public WIFI networks, using dedicated devices, etc. Get a simple yet stunning designed Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Mastering Blockchain Wallets Best Practices To Optimize Web Wallet Security BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cybersecurity Main Steps Of Operational Security Ppt Infographic Template Topics PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a cybersecurity main steps of operational security ppt infographic template topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine, potential, risks, technologies, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
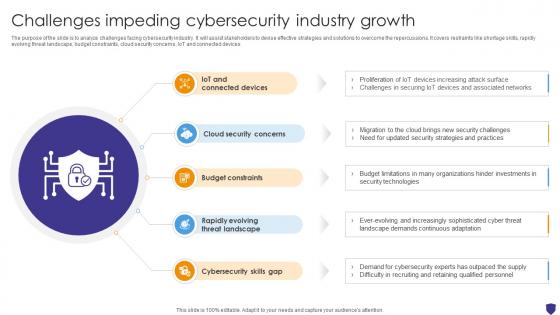
Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V
The purpose of the slide is to analyze challenges facing cybersecurity industry. It will assist stakeholders to devise effective strategies and solutions to overcome the repercussions. It covers restraints like shortage skills, rapidly evolving threat landscape, budget constraints, cloud security concerns, IoT and connected devices. Want to ace your presentation in front of a live audience Our Global Data Security Industry Report Challenges Impeding Cybersecurity Industry Growth IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
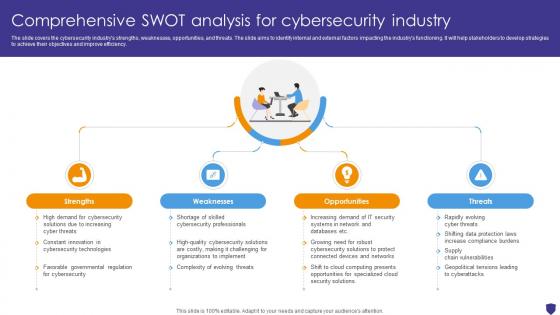
Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V
The slide covers the cybersecurity industrys strengths, weaknesses, opportunities, and threats. The slide aims to identify internal and external factors impacting the industrys functioning. It will help stakeholders to develop strategies to achieve their objectives and improve efficiency. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Global Data Security Industry Report Comprehensive Swot Analysis For Cybersecurity Industry IR SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
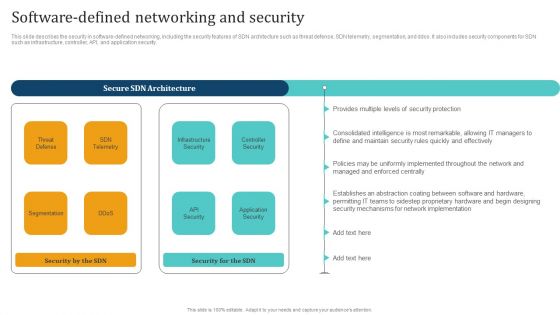
Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Threat Detection Online Security Computer Program Ppt PowerPoint Presentation Professional Icon PDF
Presenting this set of slides with name threat detection online security computer program ppt powerpoint presentation professional icon pdf. This is a three stage process. The stages in this process are threat detection online security computer program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Example Of Internet Of Things Security Problems Ppt Sample Ppt Files
This is a example of internet of things security problems ppt sample ppt files. This is a four stage process. The stages in this process are things, gateway, network, cloud.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Roles And Responsibilities For Managing Operational Risk Slides PDF
Following slide covers forecasting of operational risk events in FY21. Events covered are clients and business practices, erosion of multilateral trading rules, cyber attacks, internal and external frauds.This is a roles and responsibilities for managing operational risk slides pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk and audit committee, executive committee, investment oversight committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Security Realization Coaching Plan Problem Faced By The Organization Ppt Styles PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a workforce security realization coaching plan problem faced by the organization ppt styles pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, social engineering, financial impact, organization, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
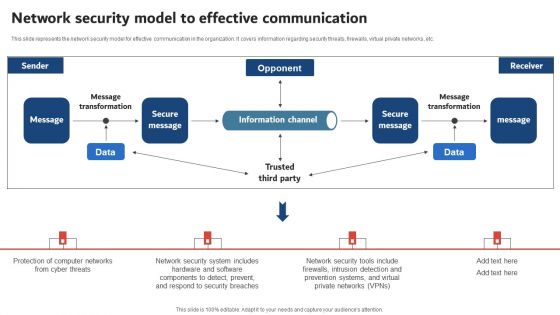
Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF
This slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Get a simple yet stunning designed Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Execution Of ICT Strategic Plan Network Security Model To Effective Communication Demonstration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Agenda Of Data Safety Initiatives For Effective IT Security Threats Administration Professional PDF
This is a agenda of data safety initiatives for effective it security threats administration professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security program keeping, threat drivers, cybersecurity attacks resulting, business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
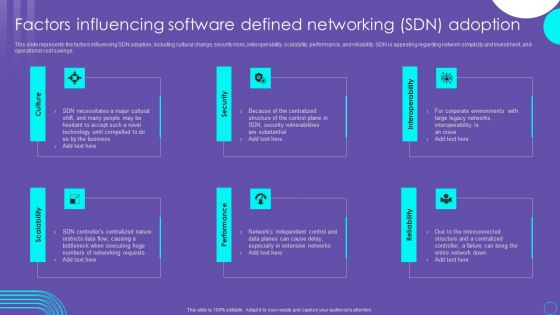
SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF
This slide represents the factors influencing SDN adoption, including cultural change, security risks, interoperability, scalability, performance, and reliability. SDN is appealing regarding network simplicity and investment, and operational cost savings. This modern and well arranged SDN Security Architecture Factors Influencing Software Defined Networking SDN Adoption Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
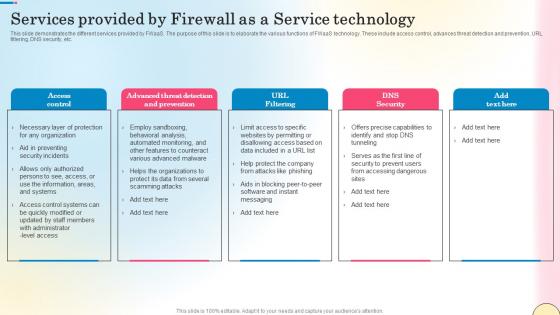
Services Provided By Firewall As A Service Technology Network Security Infographics Pdf
This slide demonstrates the different services provided by FWaaS. The purpose of this slide is to elaborate the various functions of FWaaS technology. These include access control, advances threat detection and prevention, URL filtering, DNS security, etc. There are so many reasons you need a Services Provided By Firewall As A Service Technology Network Security Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

IT Development Company Pitch Deck Problems Faced By Companies Security Introduction PDF
This is a it development company pitch deck problems faced by companies security introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poor network security, backup issues, software concerns, qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
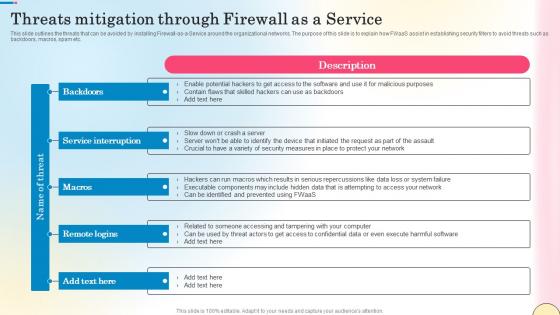
Threats Mitigation Through Firewall As A Service Network Security Guidelines Pdf
This slide outlines the threats that can be avoided by installing Firewall-as-a-Service around the organizational networks. The purpose of this slide is to explain how FWaaS assist in establishing security filters to avoid threats such as backdoors, macros, spam etc. Present like a pro with Threats Mitigation Through Firewall As A Service Network Security Guidelines Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.
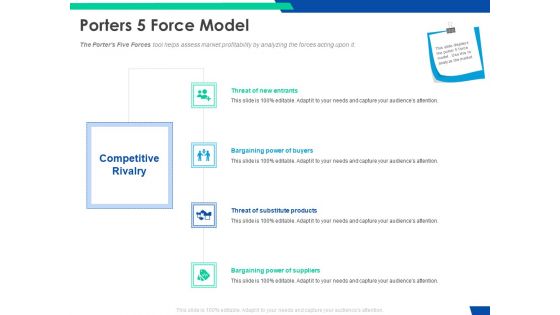
Email Security Market Research Report Porters 5 Force Model Designs PDF
Presenting this set of slides with name email security market research report porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
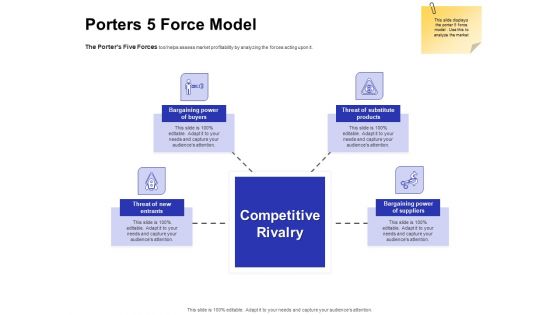
Global Cloud Based Email Security Market Porters 5 Force Model Designs PDF
Presenting this set of slides with name global cloud based email security market porters 5 force model designs pdf. This is a four stage process. The stages in this process are threat of substitute products, bargaining power of suppliers, bargaining power of buyers, threat of new entrants. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Multistep Process To Internet Security Threat Analysis Ppt PowerPoint Presentation Layouts Maker PDF
Presenting multistep process to internet security threat analysis ppt powerpoint presentation layouts maker pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identify, protect, detect, respond, recover. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf
This slide represents the dashboard to track the performance of Firewall-as-a-Service deployed by different organizations. The purpose of this slide is to showcase the overall performance of FWaaS by demonstrating statistics of monthly threat status, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Firewall As A Service Performance Tracking Dashboard Network Security Guidelines Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
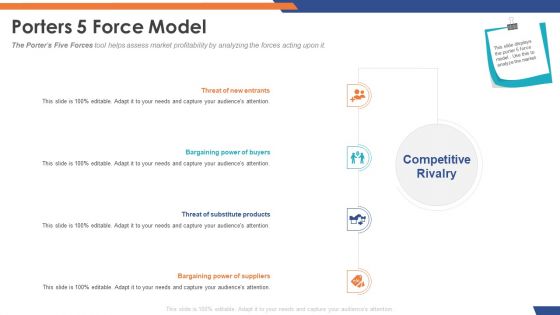
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Different Types Of Threats In IT Security Ppt PowerPoint Presentation Portfolio Model PDF
Persuade your audience using this different types of threats in it security ppt powerpoint presentation portfolio model pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including malware, botnets, virus, trojan, spam, phishing, malicious codes, web based attack. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf
This slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Want to ace your presentation in front of a live audience Our Zero Trust Exchange Overview And Benefits Zero Trust Network Security Introduction Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
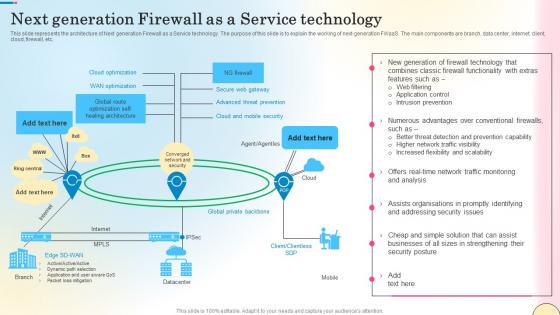
Next Generation Firewall As A Service Technology Network Security Mockup Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Do you know about Slidesgeeks Next Generation Firewall As A Service Technology Network Security Mockup Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf
This slide talks about the overview of firewall technology. The purpose of this slide is to illustrate the key uses of firewalls. These include protection against external and internal threats, conduct logging and auditing tasks, utilized by antivirus software, etc. Boost your pitch with our creative About Traditional Firewalls Overview And Key Uses Network Security Brochure Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Strategic Model For Risk Management System For A Blockchain Network Ppt PowerPoint Presentation Professional Example File PDF
Persuade your audience using this strategic model for risk management system for a blockchain network ppt powerpoint presentation professional example file pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Participants Onboarding Management, Encrypt Access Management, Develop Code Security Protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home