Cyber Security Risk Assess
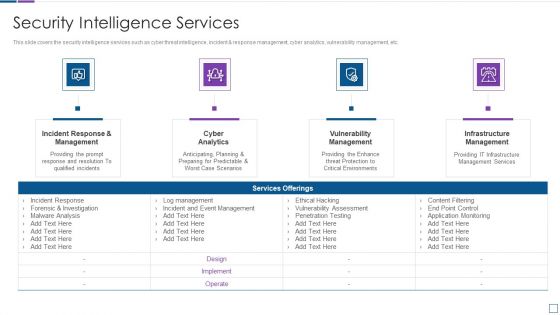
Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
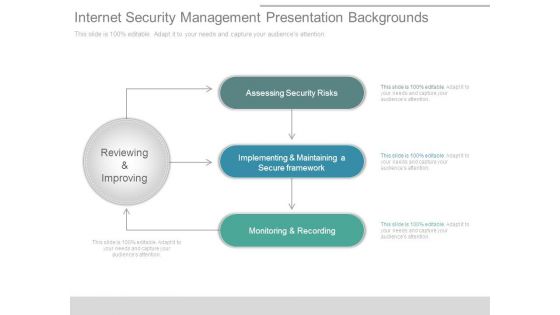
Internet Security Management Presentation Backgrounds
This is a internet security management presentation backgrounds. This is a three stage process. The stages in this process are assessing security risks, implementing and maintaining a secure framework, monitoring and recording, reviewing and improving.

Strategic Cyber Assessment And Assurance Model Microsoft PDF
The following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles. Showcasing this set of slides titled Strategic Cyber Assessment And Assurance Model Microsoft PDF. The topics addressed in these templates are Security Cases, System Security, Network And Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
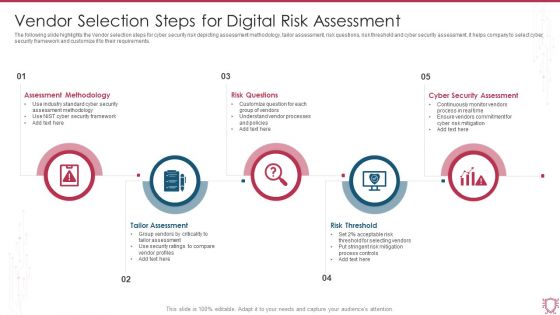
Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF
The following slide highlights the Vendor selection steps for cyber security risk depicting assessment methodology, tailor assessment, risk questions, risk threshold and cyber security assessment, it helps company to select cyber security framework and customize it to their requirements. Presenting Vendor Selection Steps For Digital Risk Assessment Ppt Visual Aids Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assessment Methodology, Risk QuestionsCyber Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
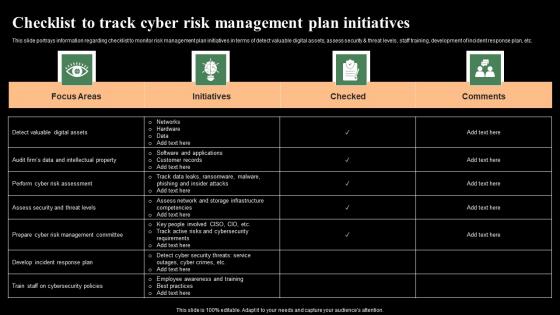
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
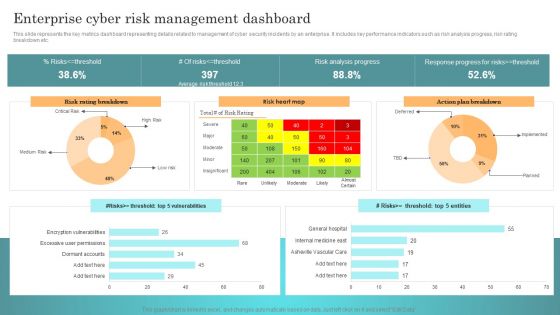
Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Find highly impressive Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For E Business And Cyber Risk Management Ppt Slides Layout PDF
Deliver an awe inspiring pitch with this creative table of contents for e business and cyber risk management ppt slides layout pdf bundle. Topics like global market, security, requirements, communication plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

E Business And Cyber Risk Management Table Of Contents Elements PDF
Deliver and pitch your topic in the best possible manner with this e business and cyber risk management table of contents elements pdf. Use them to share invaluable insights on global market, requirements, security, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management How Financial Risk Can Be Controlled Formats PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting cyber safety incident management how financial risk can be controlled formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber War Threats And Safeguard Assessment Matrix Summary PDF
This slide represents the assessment matrix for cyber terrorism threats and its functions and safeguards. It includes functions such as identify, protect, detect, respond and recover and threats such as phishing, ransomware, web app attacks and vendor and partner data loss.Showcasing this set of slides titled Cyber War Threats And Safeguard Assessment Matrix Summary PDF The topics addressed in these templates are Functions And Safeguards, Awareness Training, Forensics Investigation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
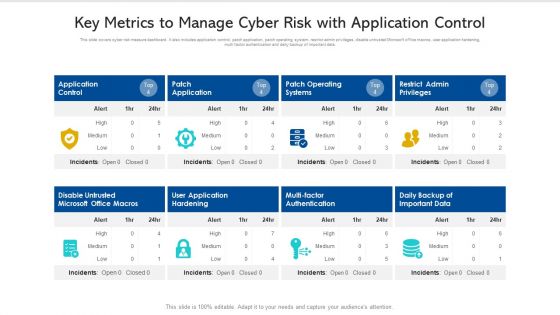
Key Metrics To Manage Cyber Risk With Application Control Ppt PowerPoint Presentation Pictures Slide PDF
This slide covers cyber risk measure dashboard. It also includes application control, patch application, patch operating system, restrict admin privileges, disable untrusted Microsoft office macros, user application hardening, multi factor authentication and daily backup of important data. Pitch your topic with ease and precision using this key metrics to manage cyber risk with application control ppt powerpoint presentation pictures slide pdf. This layout presents information on disable untrusted microsoft office macros, application control, patch operating systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Cybersecurity Assessment Matrix Of Cyber Risks Ppt Icon Graphics Pictures PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative cybersecurity assessment matrix of cyber risks ppt icon graphics pictures pdf bundle. Topics like assessment matrix of cyber risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
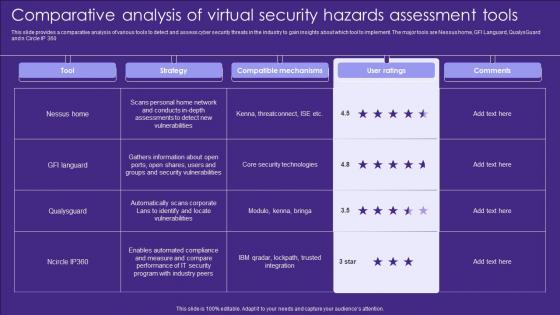
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V
The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V from Slidegeeks and deliver a wonderful presentation.

Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf
The following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Presenting this PowerPoint presentation, titled Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Analyzing Risk Probabilities Comprehensive Guide To Blockchain Digital Security Structure Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
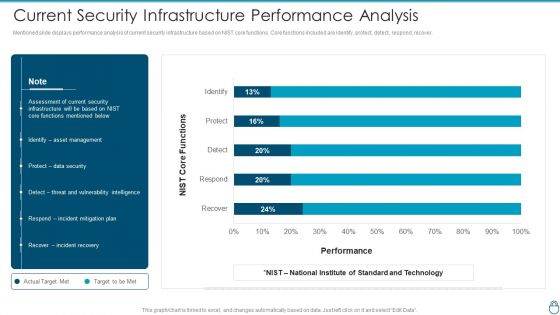
Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
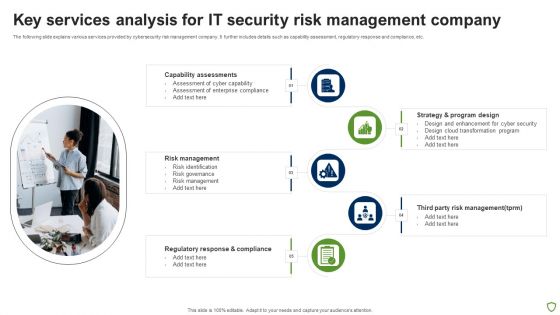
Key Services Analysis For IT Security Risk Management Company Mockup PDF
The following slide explains various services provided by cybersecurity risk management company. It further includes details such as capability assessment, regulatory response and compliance, etc. Presenting Key Services Analysis For IT Security Risk Management Company Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Capability Assessments, Risk Management, Regulatory Response And Compliance, Strategy And Program Design. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
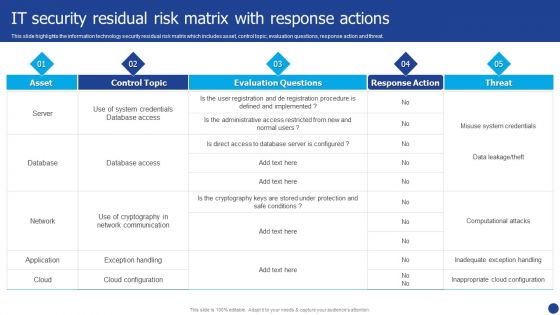
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.
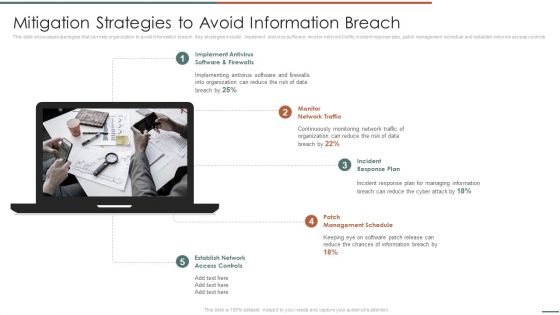
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
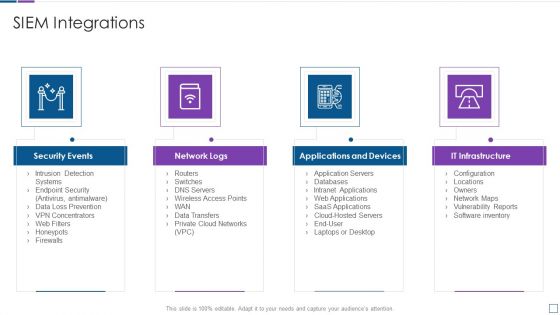
Real Time Assessment Of Security Threats SIEM Integrations Slides PDF
Presenting real time assessment of security threats siem integrations slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Real Time Assessment Of Security Threats Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of sixty five slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.

OP Risk Management Operational Risk Assessment Worksheet Microsoft PDF
This slide illustrates operational risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver an awe inspiring pitch with this creative op risk management operational risk assessment worksheet microsoft pdf bundle. Topics like client and business practices, cyber attack, internal fraud can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
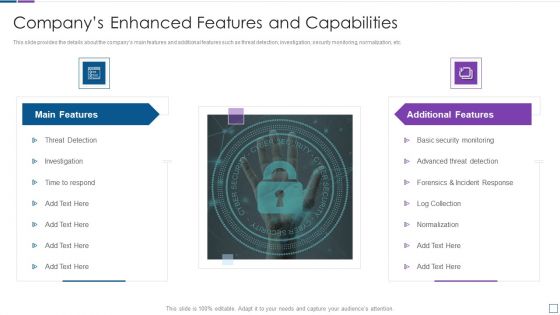
Real Time Assessment Of Security Threats Companys Enhanced Features And Capabilities Introduction PDF
This slide provides the details about the companys main features and additional features such as threat detection, investigation, security monitoring, normalization, etc. Presenting real time assessment of security threats companys enhanced features and capabilities introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like main features, additional features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Vulnerability Rating For Risk Identification Cybersecurity Risk Assessment Structure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
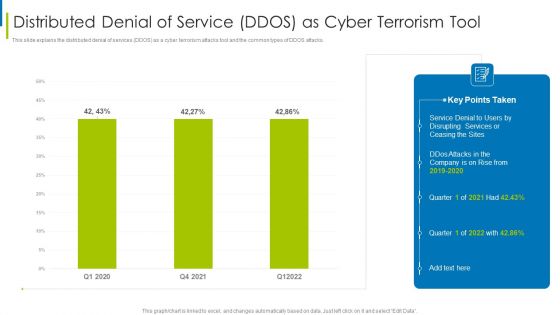
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
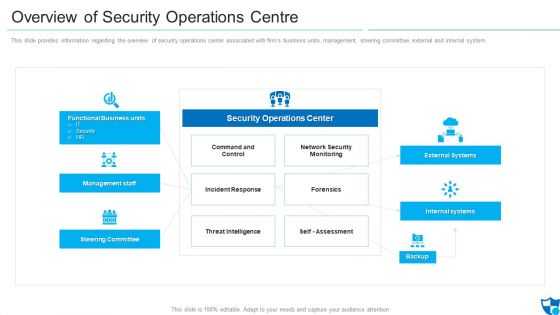
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
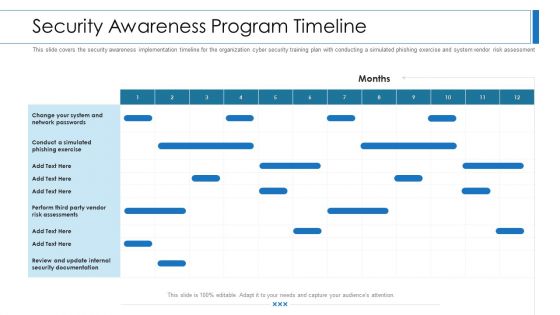
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Timeline For The Implementation Of Information Security Ppt PowerPoint Presentation Diagram Templates PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative info security timeline for the implementation of information security ppt powerpoint presentation diagram templates pdf bundle. Topics like perform third party, vendor risk assessments, review and update, internal security documentation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Slidegeeks is here to make your presentations a breeze with Organizing Security Awareness Evaluating IT System Security Using Swot Analysis Download PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
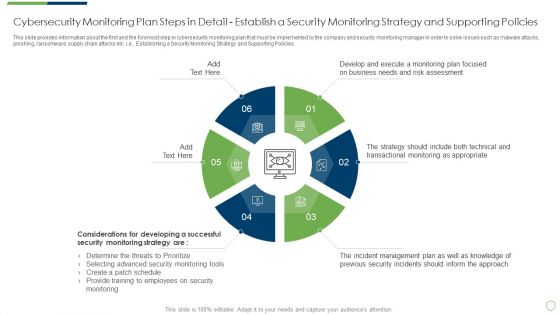
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of network security threats, helpful in identifying potential risks in IoT networked environments. It includes attacks such as man-in-middle attacks, RFIS spoofing, sinkhole attacks, and traffic analysis attacks. There are so many reasons you need a Building Trust With IoT Security Overview Of Network Security Attacks In IoT Environment IoT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
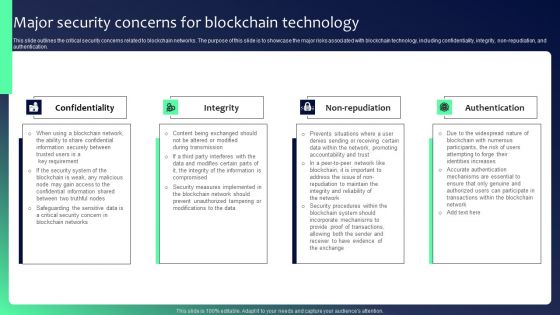
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
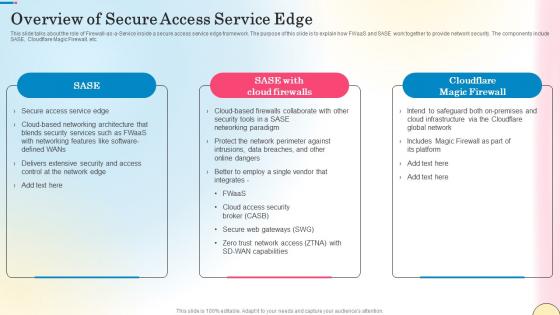
Overview Of Secure Access Service Edge Network Security Download Pdf
This slide outlines the various types of firewalls. The purpose of this slide is to elaborate the use of different firewalls. These include packet filtering, proxy service firewall, stateful inspection, next-generation firewall, threat focusses next-gen firewall, etc. Boost your pitch with our creative Overview Of Secure Access Service Edge Network Security Download Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
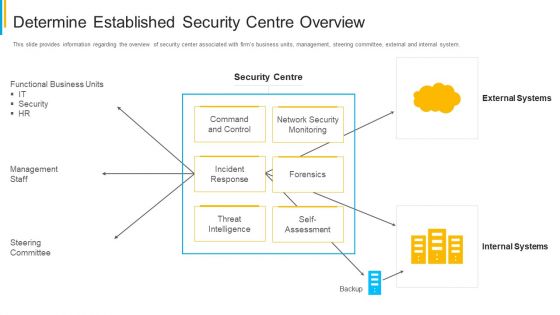
Project Security Administration IT Determine Established Security Centre Overview Infographics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this project security administration it determine established security centre overview infographics pdf. Use them to share invaluable insights on functional business units, management staff, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF
The following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Impact Analysis, Risk Assessment, Controls, Report, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF
Following slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Present like a pro with Cyber Risks And Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
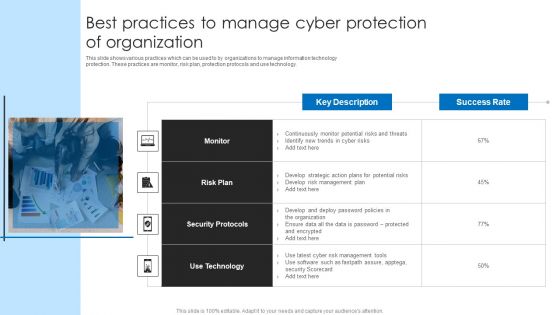
Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Threat Assessment For Cyber Attack Ppt PowerPoint Presentation File Sample PDF
Presenting this set of slides with name threat assessment for cyber attack ppt powerpoint presentation file sample pdf. This is a three stage process. The stages in this process are threat assessment for cyber attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Slidegeeks is here to make your presentations a breeze with Probability Assessment Matrix For Risk Management Cybersecurity Risk Assessment Professional PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
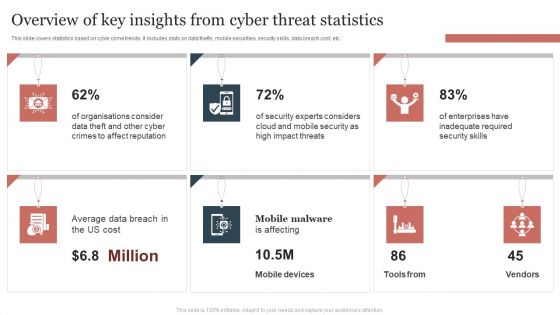
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

4 Steps For Developing IT Security Plan Professional PDF
This slide represents 4 steps for developing cyber security strategy such as understanding cyber threats, assessing cyber security maturity, determining steps to improve cyber security program and documentation. Presenting 4 Steps For Developing IT Security Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Documenting Cyber Security Plan, Assessing Cyber Security Maturity, Organizations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
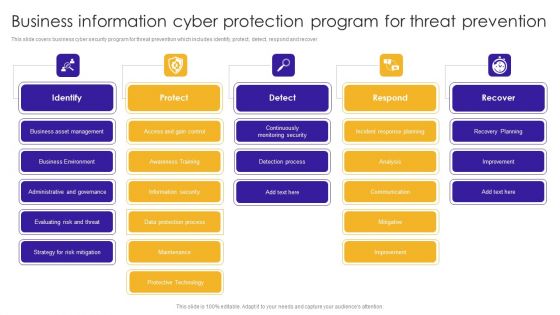
Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Country Wise Security Strategies For Digital Terrorism Professional PDF
This slide shows various strategies adopted by different countries to eliminate threat of cyber attacks. It include various risk area covered such as Hostile cyber attacks, International Cyber Attacks etc. Presenting Country Wise Security Strategies For Digital Terrorism Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including National Strategy, Cyber Security, International Cyber. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template

Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF
The following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Persuade your audience using this Digital Risk Assessment Management Approach With Priority And Control Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Priority, Mitigation, Controls, Automation, Governance, Risk Culture. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
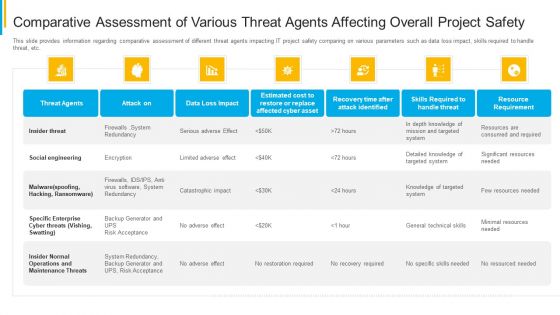
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home