Cyber Security Image
Icons Slide For Cyber Safety Incident Management Information PDF
Introducing our well designed icons slide for cyber safety incident management information pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Cyber Safety Incident Management Threat Management Action Plan Sample PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Safety Incident Management Workplace Employee Assistance Program Microsoft PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber safety incident management workplace employee assistance program microsoft pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
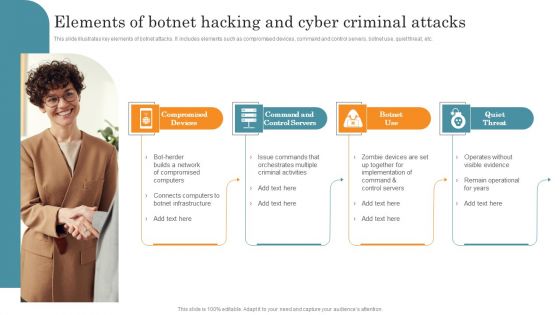
Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF
This slide illustrates key elements of botnet attacks. It includes elements such as compromised devices, command and control servers, botnet use, quiet threat, etc. Persuade your audience using this Elements Of Botnet Hacking And Cyber Criminal Attacks Brochure PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Compromised Devices, Command Control Servers, Botnet Use, Quiet Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
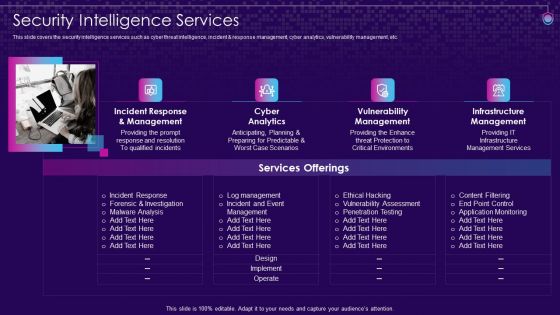
SIEM Services Security Intelligence Services Ppt Show Layouts PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem services security intelligence services ppt show layouts pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like management cyber, analytics vulnerability, management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
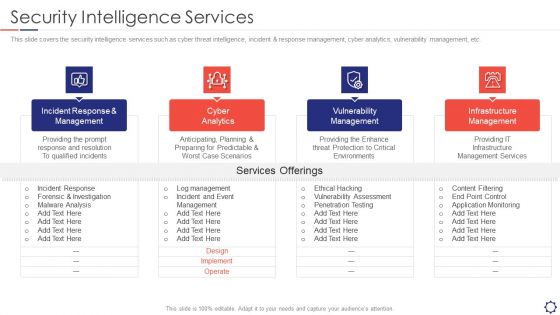
SIEM Security Intelligence Services Ppt Professional Format PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting siem security intelligence services ppt professional format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Exploitation IT Purpose Of Hackers Infographics PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a cyber exploitation it purpose of hackers infographics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like computer fraud, privacy breach, electronic money laundering, electronic funds transfer, denial of service attacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
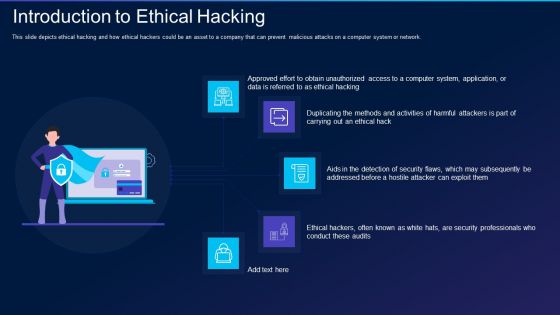
Cyber Exploitation IT Introduction To Ethical Hacking Introduction PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
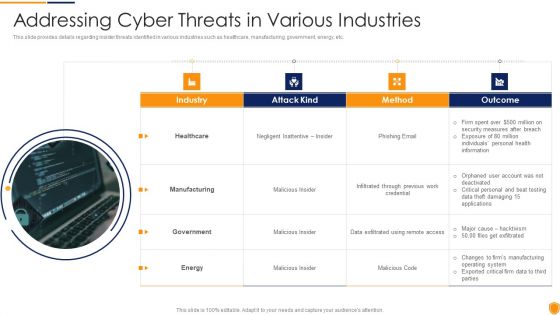
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Cyber Threats Portrait PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing cyber threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ukraine Cyberwarfare Hermetic Wiper Cyber Attack Against Ukraine Designs Pdf
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Eases Partition Master. This is a ukraine cyberwarfare hermetic wiper cyber attack against ukraine designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like script for detecting executables signed by the same certificate is accessible, virus reboots the infected system after corrupting the mbr, resulting in a boot failure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Roles And Responsibilities Pictures PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a cyber safety incident management roles and responsibilities pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, human resources responsibilities, internal investigations unit responsibilities, unit supervisor or manager responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
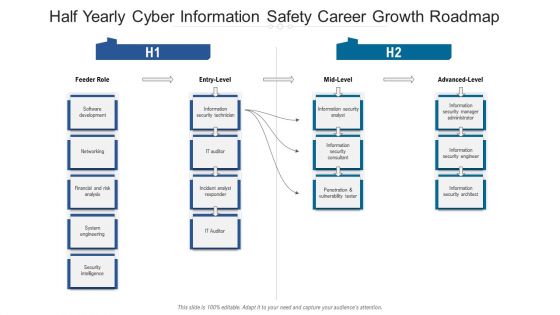
Half Yearly Cyber Information Safety Career Growth Roadmap Designs
Presenting the half yearly cyber information safety career growth roadmap designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
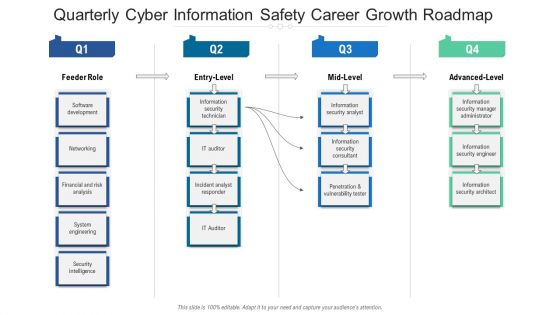
Quarterly Cyber Information Safety Career Growth Roadmap Elements
Presenting the quarterly cyber information safety career growth roadmap elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
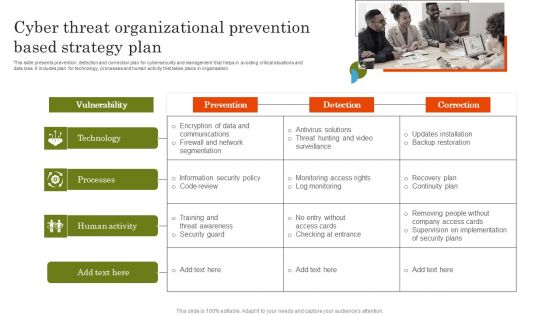
Cyber Threat Organizational Prevention Based Strategy Plan Template PDF
This slide presents prevention, detection and correction plan for cybersecurity and management that helps in avoiding critical situations and data loss. It includes plan for technology, processes and human activity that takes place in organisation. Introducing Cyber Threat Organizational Prevention Based Strategy Plan Template PDF. to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Processes, Human Activity, using this template. Grab it now to reap its full benefits.
Risk Recognition Automation Security Intelligence Services Ppt Icon Infographics PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. This is a risk recognition automation security intelligence services ppt icon infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
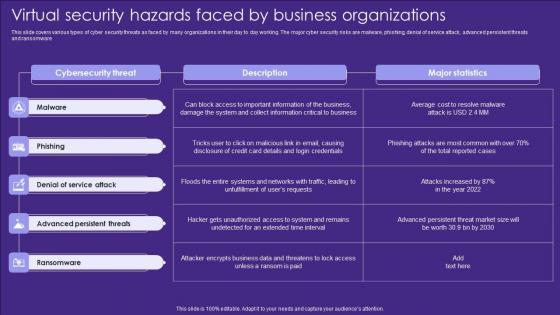
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
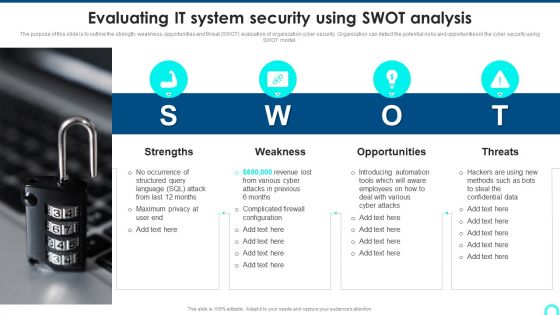
Evaluating IT System Security Using SWOT Analysis Portrait PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Presenting Evaluating IT System Security Using SWOT Analysis Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Strengths, Weakness, Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
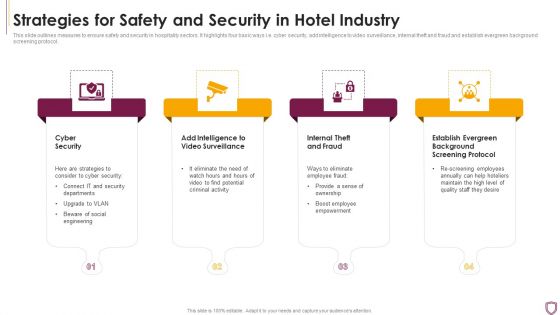
Strategies For Safety And Security In Hotel Industry Sample PDF
This slide outlines measures to ensure safety and security in hospitality sectors. It highlights four basic ways i.e. cyber security, add intelligence to video surveillance, internal theft and fraud and establish evergreen background screening protocol.Persuade your audience using this Strategies For Safety And Security In Hotel Industry Sample PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security, Internal Theft And Fraud, Establish Evergreen Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
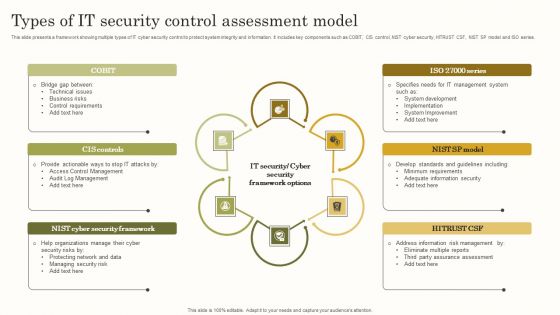
Types Of IT Security Control Assessment Model Clipart PDF
This slide presents a framework showing multiple types of IT cyber security control to protect system integrity and information. It includes key components such as COBIT, CIS control, NIST cyber security, HITRUST CSF, NIST SP model and ISO series. Persuade your audience using this Types Of IT Security Control Assessment Model Clipart PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Options, Framework, Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
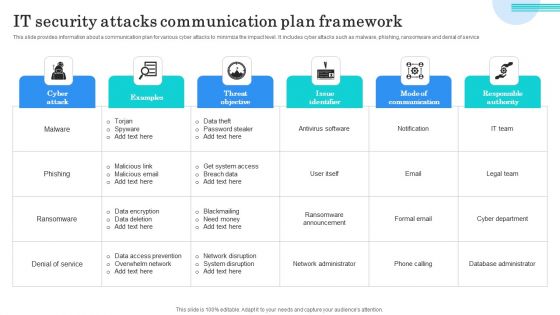
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
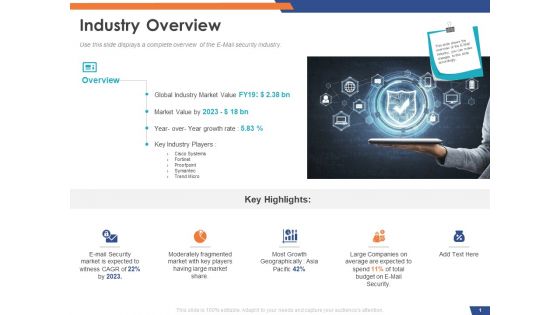
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
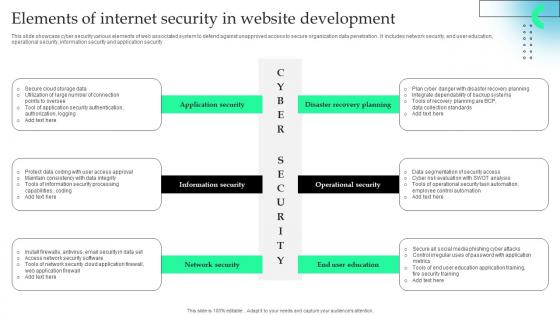
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
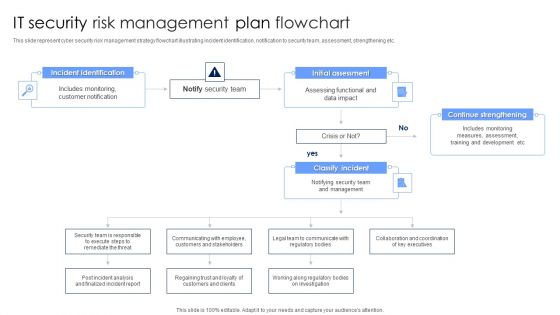
IT Security Risk Management Plan Flowchart Diagrams PDF
This slide represent cyber security risk management strategy flowchart illustrating incident identification, notification to security team, assessment, strengthening etc. Persuade your audience using this IT Security Risk Management Plan Flowchart Diagrams PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Incident Identification, Initial Assessment, Continue Strengthening. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management In IT Security Plan Rules PDF
This slide represents risk management in cyber security strategy illustrating organizational leadership, information risk management, technical risk management etc. Pitch your topic with ease and precision using this Risk Management In IT Security Plan Rules PDF. This layout presents information on Security Architecture, Compliance Management, Technical Risk Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

6 Level IT Security Plan Maturity Model Slides PDF
This slide represent 6 level cyber security strategy maturity model illustrating levels such as initial, developing, defined, managed, optimization and unified. Pitch your topic with ease and precision using this 6 Level IT Security Plan Maturity Model Slides PDF. This layout presents information on Awareness, Organization Security, Metrics To Measure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Security For Remote Workplace Plan Checklist Introduction PDF
This slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Pitch your topic with ease and precision using this IT Security For Remote Workplace Plan Checklist Introduction PDF. This layout presents information on Security Measures, Employees, Team. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Framework For Building IT Security Transformation Program Pictures PDF
This slide covers the framework for developing security transformation program which focuses on training and awareness, cyber threat management, secure baseline and architecture, etc.Presenting Framework For Building IT Security Transformation Program Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Training Awareness, Threat Management, Secure Architecture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
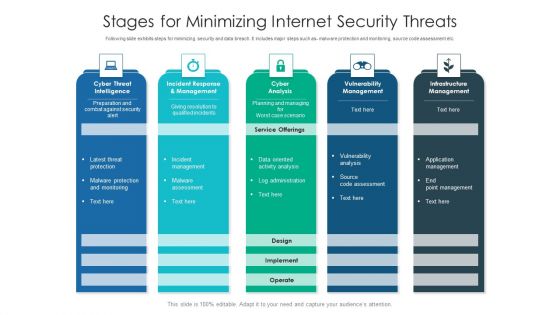
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
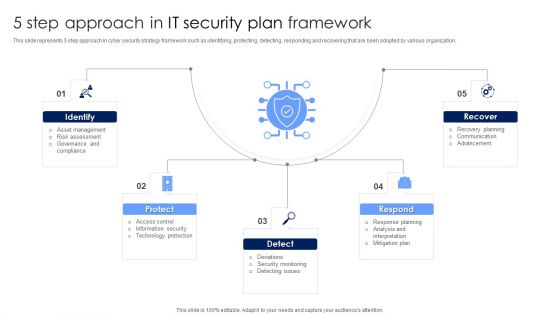
5 Step Approach In IT Security Plan Framework Designs PDF
This slide represents 5 step approach in cyber security strategy framework such as identifying, protecting, detecting, responding and recovering that are been adopted by various organization. Presenting 5 Step Approach In IT Security Plan Framework Designs PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Protect, Detect, Respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
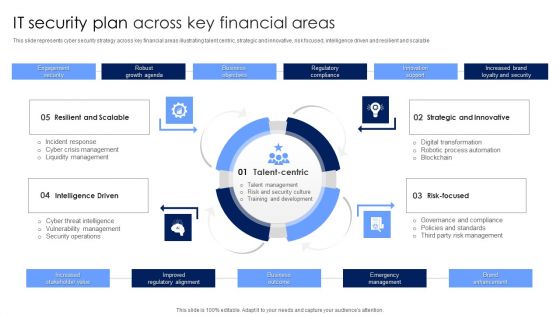
IT Security Plan Across Key Financial Areas Portrait PDF
This slide represents cyber security strategy across key financial areas illustrating talent centric, strategic and innovative, risk focused, intelligence driven and resilient and scalable. Presenting IT Security Plan Across Key Financial Areas Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Strategic And Innovative, Risk Focused, Intelligence Driven. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
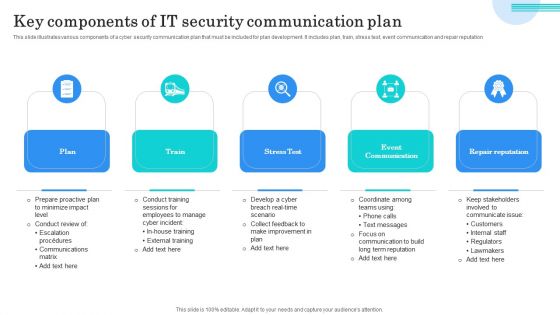
Key Components Of IT Security Communication Plan Mockup PDF
This slide illustrates various components of a cyber security communication plan that must be included for plan development. It includes plan, train, stress test, event communication and repair reputation. Presenting Key Components Of IT Security Communication Plan Mockup PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Plan, Train, Stress Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Elements Of IT Security IT Ppt Pictures Inspiration PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a key elements of it security it ppt pictures inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, end user education, cloud security, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
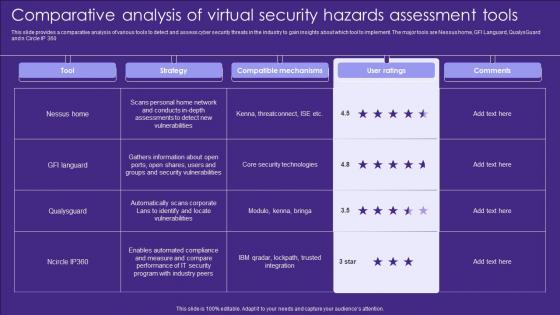
Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf
This slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Pitch your topic with ease and precision using this Comparative Analysis Of Virtual Security Hazards Assessment Tools Elements Pdf. This layout presents information on Strategy, Compatible Mechanisms, Ratings. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Employee Training To Control Virtual Security Hazards Designs Pdf
Following slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Pitch your topic with ease and precision using this Employee Training To Control Virtual Security Hazards Designs Pdf. This layout presents information on Internet Links, Email, Strong Passwords. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Major Target Areas Of Virtual Security Hazards Summary Pdf
The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion Pitch your topic with ease and precision using this Major Target Areas Of Virtual Security Hazards Summary Pdf. This layout presents information on Financial Resources, Public Opinion, Electronic Devices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Techniques Used By Virtual Security Hazards Actors Professional Pdf
Following template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Pitch your topic with ease and precision using this Techniques Used By Virtual Security Hazards Actors Professional Pdf. This layout presents information on Code Injection, Password Cracking, Middle. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Addressing The Various Security Incidents And Attacks Icons PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.Create an editable Addressing The Various Security Incidents And Attacks Icons PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Addressing The Various Security Incidents And Attacks Icons PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
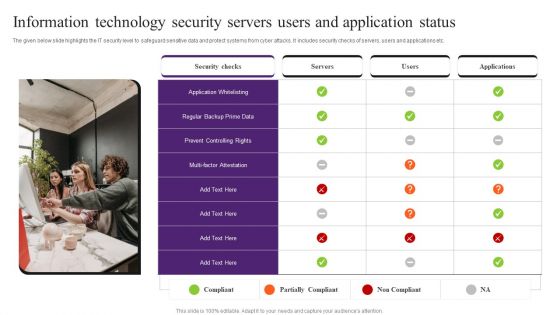
Information Technology Security Servers Users And Application Status Pictures PDF
The given below slide highlights the IT security level to safeguard sensitive data and protect systems from cyber attacks. It includes security checks of servers, users and applications etc. Presenting Information Technology Security Servers Users And Application Status Pictures PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Application Whitelisting, Security Checks, Information Technology Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Stages Of Creating Internet Security Threat Management Process Information PDF
This slide exhibits stages of developing security breach mitigation plan. It includes multiple steps such as- running a company centric assessment, cyber security incident assessment and so on. Presenting stages of creating internet security threat management process information pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including stages of creating internet security threat management process. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
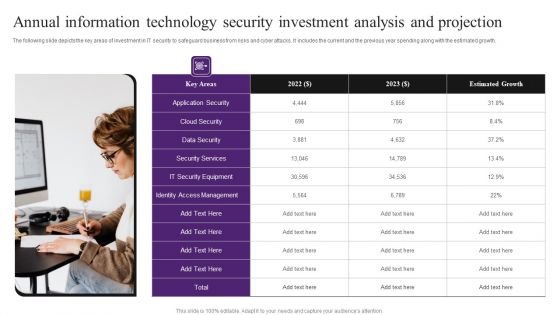
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Steps To Deploy People Centric Work Culture Security Background PDF
The following slide showcases steps to enforce human centric security system to empower employees in handling useful information. It includes elements such as establishing environment for people centric security PCS, promoting culture of cyber security, etc. Presenting Steps To Deploy People Centric Work Culture Security Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Converting Cybersecurity, Punishment System, Protection Practices. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.
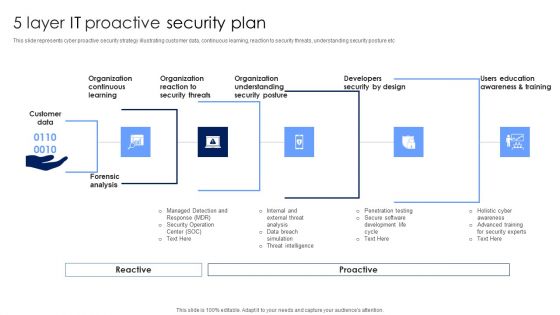
5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Latest Trends For Mobile Smart Phone Security Icons PDF
This slide shows current trends for securing mobile phone against potential cyber attacks and loss of sensitive data. It include trends such as rise in security automation, increasing threat modelling and SAST-DAST integration etc qPresenting Latest Trends For Mobile Smart Phone Security Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increasing Security, SAST DAST Integration, Increasing Threat Modelling. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
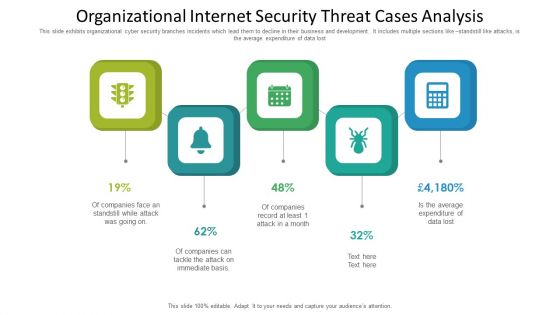
Organizational Internet Security Threat Cases Analysis Information PDF
This slide exhibits organizational cyber security branches incidents which lead them to decline in their business and development. It includes multiple sections like standstill like attacks, is the average expenditure of data lost. Presenting organizational internet security threat cases analysis information pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including organizational internet security threat cases analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Safety And Security Challenges In Hotel Industry Topics PDF
This slide covers four major threats in safety element of hotel industry. It include major risks associated in hotels i.e. security breach, physical crimes, individuality theft and cyber attack. Persuade your audience using this Four Safety And Security Challenges In Hotel Industry Topics PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Breach, Physical Crimes, Individuality Theft Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
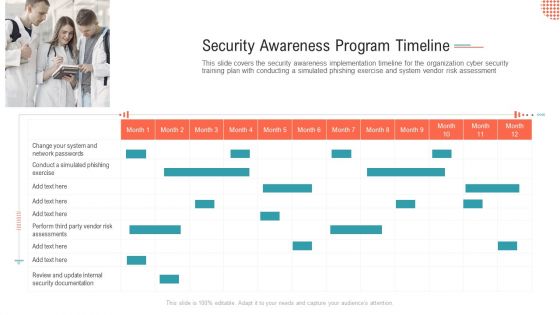
Security Awareness Program Timeline Ppt Outline Microsoft PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment.This is a security awareness program timeline ppt outline microsoft pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct a simulated phishing exercise, change your system and network passwords. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
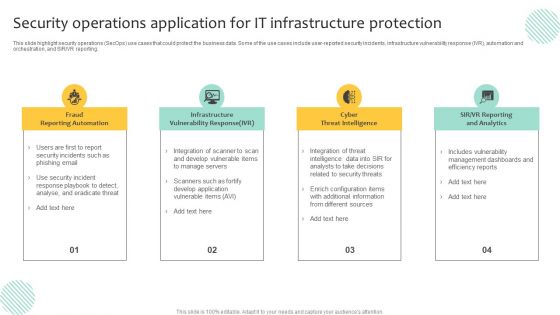
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
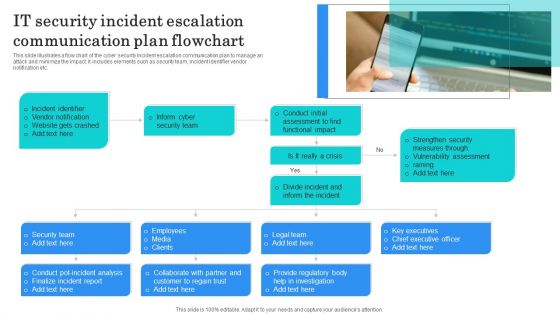
IT Security Incident Escalation Communication Plan Flowchart Structure PDF
This slide illustrates a flow chart of the cyber security incident escalation communication plan to manage an attack and minimize the impact. It includes elements such as security team, incident identifier vendor notification etc. Presenting IT Security Incident Escalation Communication Plan Flowchart Structure PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Incident Identifier, Vendor Notification, Website Gets Crashed. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
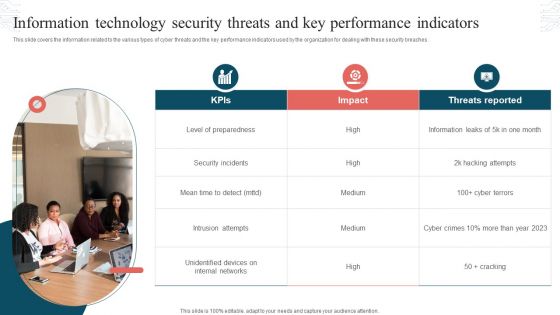
Information Technology Security Threats And Key Performance Indicators Formats PDF
This slide covers the information related to the various types of cyber threats and the key performance indicators used by the organization for dealing with these security breaches. Presenting Information Technology Security Threats And Key Performance Indicators Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Threats Reported, Security Incidents, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

The ROI Of Security Awareness Training Ppt Slides Background PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyberconscious workforce.This is a the roi of security awareness training ppt slides background pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs from routine security practices, costs from productivity loss. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
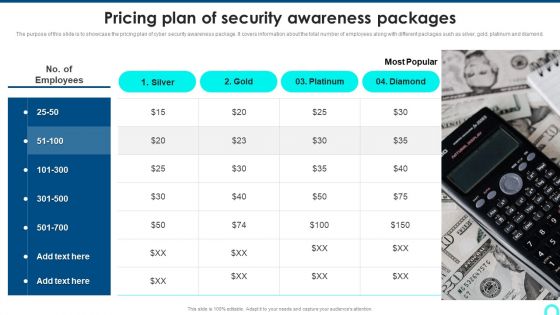
Pricing Plan Of Security Awareness Packages Elements PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. This is a Pricing Plan Of Security Awareness Packages Elements PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Pricing Plan, Security Awareness, Packages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Packages Offered By Third Party Clipart PDF
The purpose of this slide is to highlight cyber security awareness packages such as silver, gold, platinum and diamond which are offered by third party to the businesses. The package includes key features such as unlimited phishing security tests, automated awareness training campaign etc. This is a Security Awareness Packages Offered By Third Party Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unlimited Phishing, Automated Awareness, Industry Benchmarking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
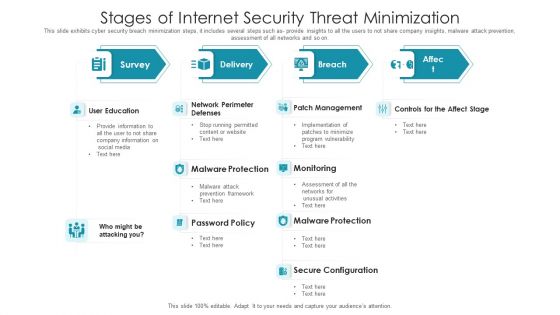
Stages Of Internet Security Threat Minimization Summary PDF
This slide exhibits cyber security breach minimization steps, it includes several steps such as- provide insights to all the users to not share company insights, malware attack prevention, assessment of all networks and so on. Pitch your topic with ease and precision using this stages of internet security threat minimization summary pdf. This layout presents information on patch management, monitoring, malware protection, secure configuration, user education. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
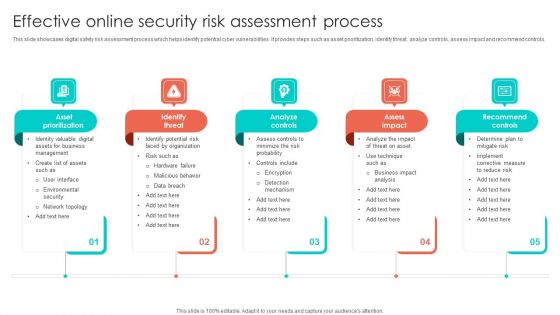
Effective Online Security Risk Assessment Process Inspiration PDF
This slide showcases digital safety risk assessment process which helps identify potential cyber vulnerabilities. It provides steps such as asset prioritization, identify threat, analyze controls, assess impact and recommend controls. Persuade your audience using this Effective Online Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Card Data Security, Cross Border Transactions, Payment Methods. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Defense Plan Maturity Evaluation Information PDF
This slide represents cyber security defense strategy maturity evaluation mode illustrating culture and organization, governance, visibility and controls, focused defense and intelligence operations. Persuade your audience using this IT Security Defense Plan Maturity Evaluation Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization, Focused Defense, Intelligence Operations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices To Develop IT Security Communication Plan Diagrams PDF
This slide illustrates various best practices for developing an effective Cyber security communication plan. It includes best practices such as make plan flexible, provide visibility to audience and keep relevant and engaging content. Presenting Best Practices To Develop IT Security Communication Plan Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Make Plan Flexible, Provide Visibility Audience, Keep Relevant Engaging. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
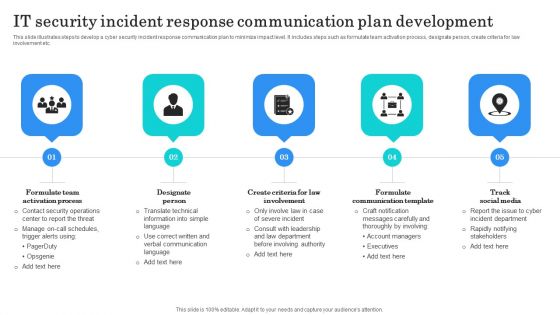
IT Security Incident Response Communication Plan Development Background PDF
This slide illustrates steps to develop a cyber security incident response communication plan to minimize impact level. It includes steps such as formulate team activation process, designate person, create criteria for law involvement etc. Presenting IT Security Incident Response Communication Plan Development Background PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Formulate Team Activation, Designate Person, Formulate Communication Template. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home