Cyber Crime

Develop Corporate Cyber Security Risk Mitigation Plan Why Us For Organization Cyber Protection Services Sample PDF
Presenting develop corporate cyber security risk mitigation plan why us for organization cyber protection services sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like knowledge, system security, net development, it support services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
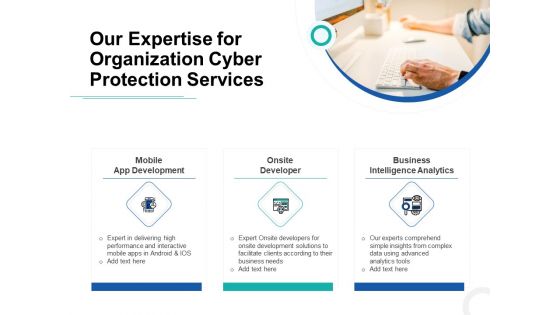
Develop Corporate Cyber Security Risk Mitigation Plan Our Expertise For Organization Cyber Protection Services Background PDF
Presenting develop corporate cyber security risk mitigation plan our expertise for organization cyber protection services background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mobile app development, onsite developer, business intelligence analytic. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
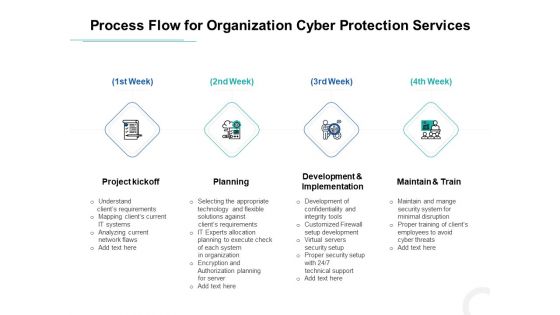
Develop Corporate Cyber Security Risk Mitigation Plan Process Flow For Organization Cyber Protection Services Background PDF
This is a develop corporate cyber security risk mitigation plan process flow for organization cyber protection services background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, maintain and train. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Timeframe For Organization Cyber Protection Services Structure PDF
This is a develop corporate cyber security risk mitigation plan timeframe for organization cyber protection services structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Addressing Indicators Associated To Insider Cyber Threats Themes PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing indicators associated to insider cyber threats themes pdf. Use them to share invaluable insights on unauthorized, privileged, measures, authentication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Contingency Plan For Cyber Threat Handling Brochure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an awe inspiring pitch with this creative cyber security administration in organization contingency plan for cyber threat handling brochure pdf bundle. Topics like contingency, implementation, components, documentation, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
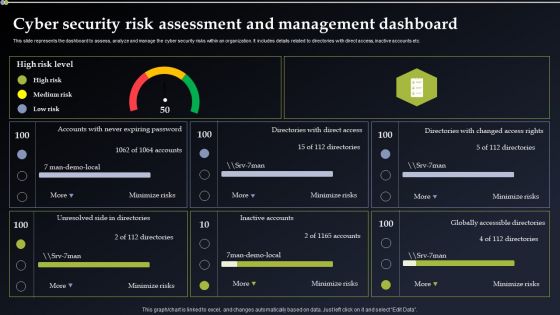
Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment Portrait PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Cyber Security Incident Communication Strategy Topics PDF

CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Welcome to our selection of the CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Matrix Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
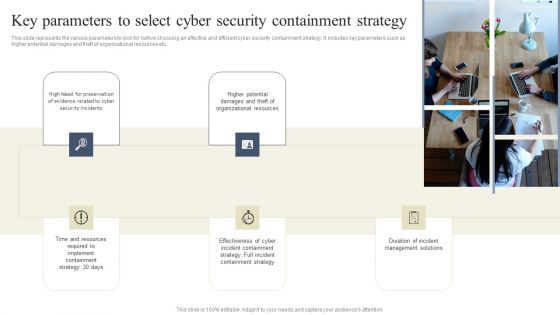
CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Take your projects to the next level with our ultimate collection of CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
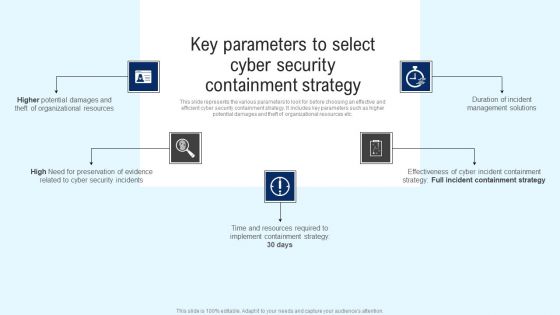
Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Key Parameters To Select Cyber Security Containment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
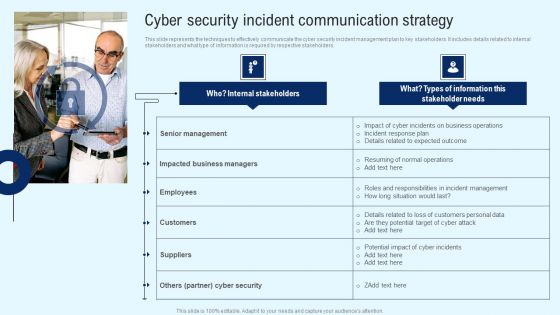
Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
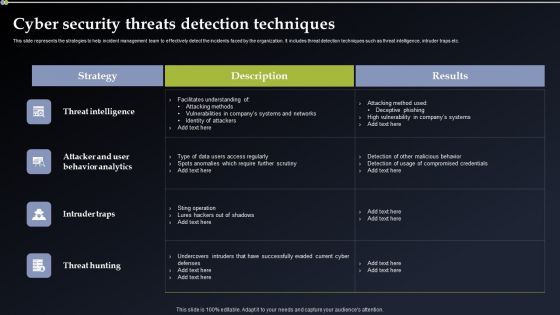
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.
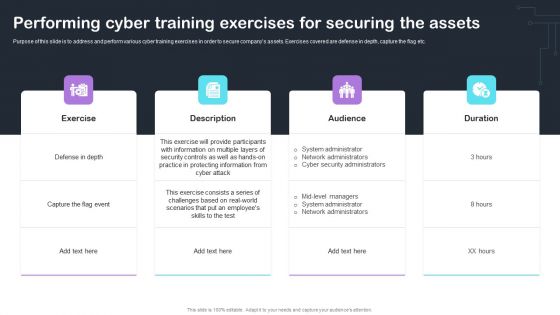
Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
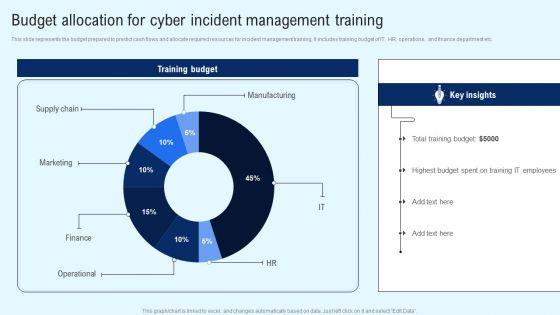
Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Find a pre designed and impeccable Implementing Cyber Security Incident Budget Allocation For Cyber Incident Portrait PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
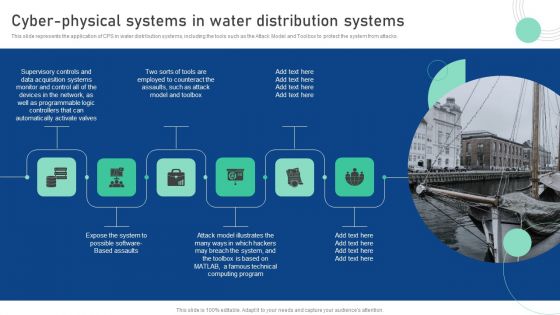
Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. This Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
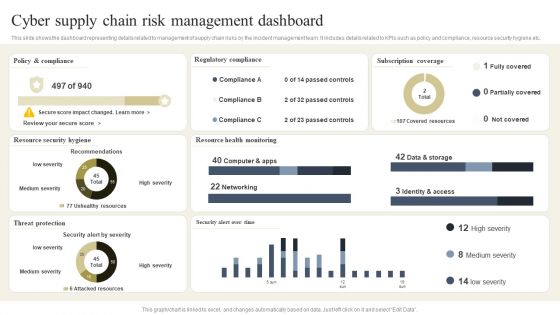
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
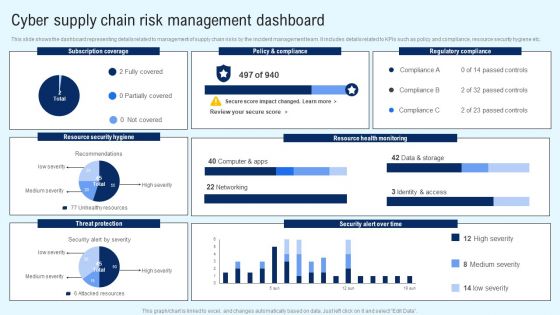
Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
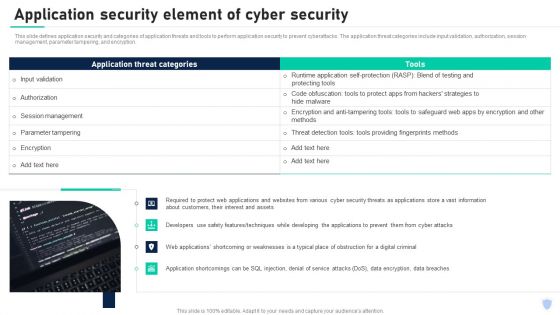
Cyber Security Components To Enhance Processes Application Security Element Of Cyber Security Infographics PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Boost your pitch with our creative Cyber Security Components To Enhance Processes Career Opportunities In Cybersecurity Profession Sample PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
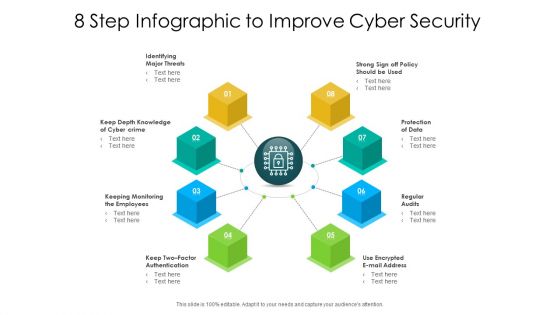
8 Step Infographic To Improve Cyber Security Ppt PowerPoint Presentation Layouts Themes PDF
Presenting 8 step infographic to improve cyber security ppt powerpoint presentation layouts themes pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including identifying major threats, keep depth knowledge of cyber crime, protection of data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF
This slide shows privileged access management for IAM model or organization. The purpose of this strategy is to highlight all phases for implementing IAM strategy against cyber crimes. It include phases such as pre work operations and monitoring Pitch your topic with ease and precision using this Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF. This layout presents information on Identify Requirements, Build Framework, Ensure Resilience. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
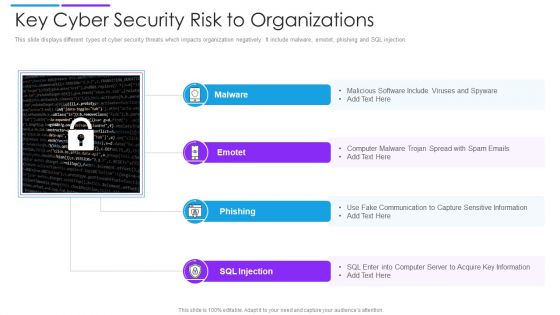
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Rsa Cyber Attack In Powerpoint And Google Slides Cpb
Introducing our well designed Rsa Cyber Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Rsa Cyber Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Direct Cyber Attack In Powerpoint And Google Slides Cpb
Introducing our well-designed Direct Cyber Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Direct Cyber Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
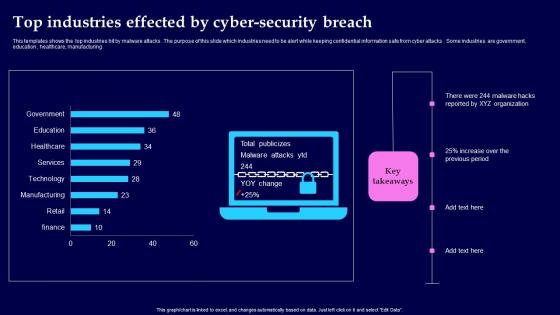
Top Industries Effected By Cyber Security Breach Background Pdf
This templates shows the top industries hit by malware attacks. The purpose of this slide which industries need to be alert while keeping confidential information safe from cyber attacks. Some industries are government, education, healthcare, manufacturing Showcasing this set of slides titled Top Industries Effected By Cyber Security Breach Background Pdf The topics addressed in these templates are Top Industries Effected, Cyber Security Breach All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Top Countries Effect By Cyber Security Breach Background Pdf
This templates shows the top countries impacted by malware attacks. The purpose of this slide which country is most effected by malware attack what precaution they should take to reduce the numbers of attacks in futures. it includes various countries such as sweden, japan , china, etc. Pitch your topic with ease and precision using this Top Countries Effect By Cyber Security Breach Background Pdf This layout presents information on Malware Attack, Countries Effect, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
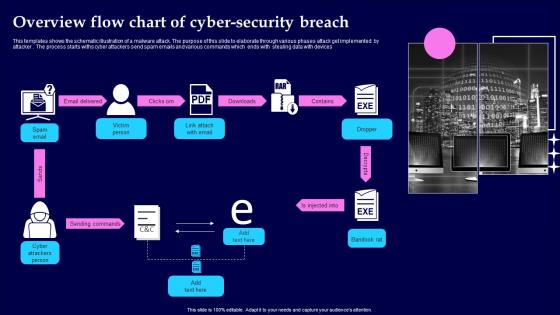
Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
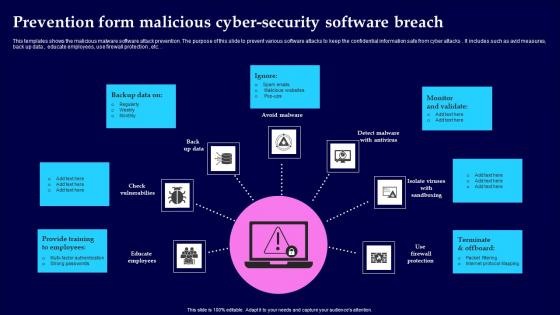
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
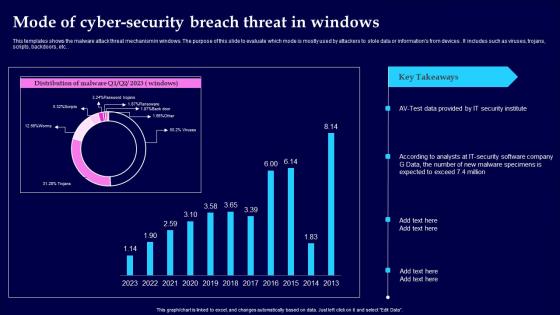
Mode Of Cyber Security Breach Threat In Windows Clipart Pdf
This templates shows the malware attack threat mechanism in windows. The purpose of this slide to evaluate which mode is mostly used by attackers to stole data or informations from devices. It includes such as viruses, trojans, scripts, backdoors, etc. Showcasing this set of slides titled Mode Of Cyber Security Breach Threat In Windows Clipart Pdf The topics addressed in these templates are Mode Of Cyber Security, Threat In Windows All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Maersk Cyber Attack In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Maersk Cyber Attack In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Maersk Cyber Attack that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf
This slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks. Pitch your topic with ease and precision using this Implementation Of Cyber Security Risk Management Strategic Agenda Pictures Pdf. This layout presents information on Steps, Action Taken, Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
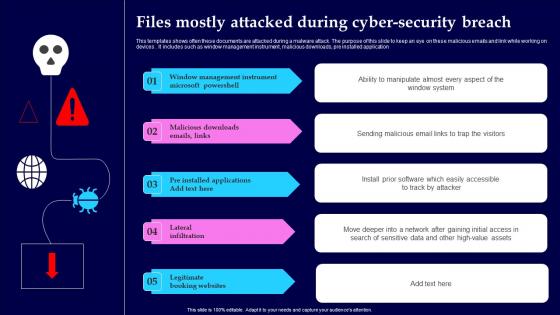
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Multiple Attack In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Multiple Attack In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Multiple Attack. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
Cyber Security Breach Icon To Prevent Threat Brochure Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon To Prevent Threat Brochure Pdf This layout presents information on Cyber Security Breach, Icon To Prevent Threat It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
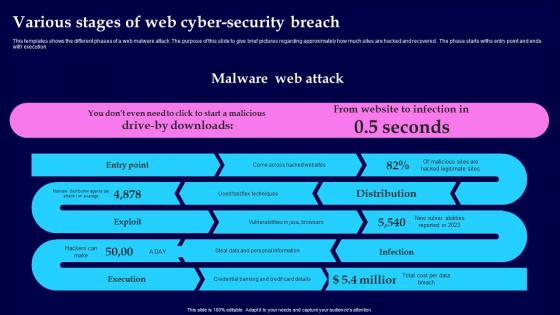
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
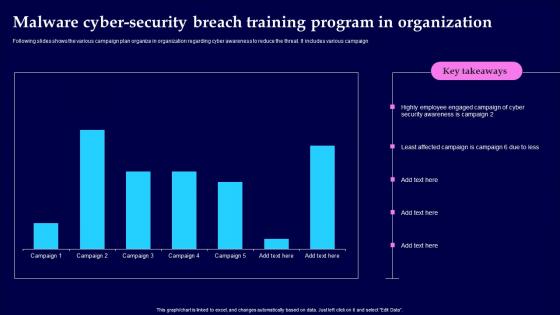
Malware Cyber Security Breach Training Program In Organization Designs Pdf
Following slides shows the various campaign plan organize in organization regarding cyber awareness to reduce the threat. It includes various campaign Pitch your topic with ease and precision using this Malware Cyber Security Breach Training Program In Organization Designs Pdf This layout presents information on Malware Cyber Security Breach, Training Program In Organization It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Checklist To Ensure Strong Authentication Icons Pdf
Following slide shows the checklist for cyber security safety to ensure robust authentication which will assist in regular checking from preventing threat. It includes various parameter for cross checking the cyber security. Showcasing this set of slides titled Cyber Security Checklist To Ensure Strong Authentication Icons Pdf. The topics addressed in these templates are Cyber Security Checklist, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides
This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
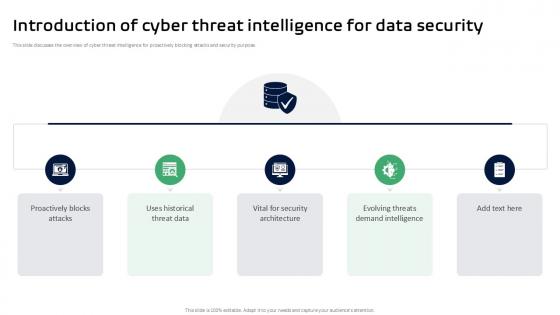
Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template
This slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Introduction Of Cyber Threat Intelligence For Threat Intelligence Ppt Template

Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Are you searching for a Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Managing Cyber Security In Manufacturing 30 Days Plan Diagrams PDF from Slidegeeks today.
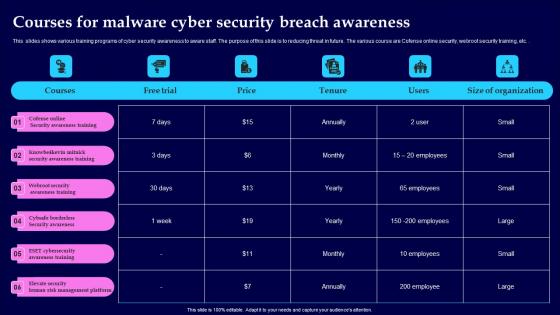
Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Data Science In Powerpoint And Google Slides Cpb
Introducing our well designed Cyber Security Data Science In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Cyber Security Data Science. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Training Roadmap In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Training Roadmap that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Protection Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Protection Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Spyware Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well designed Spyware Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Spyware Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
E Commerce Cyber Security In Powerpoint And Google Slides Cpb
Introducing our well-designed E Commerce Cyber Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like E Commerce Cyber Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Flaw Cyber Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Flaw Cyber Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
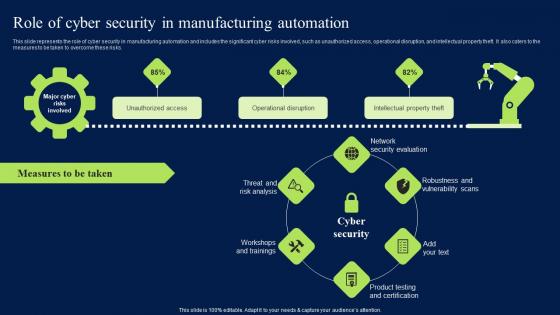
Role Of Cyber Security In Manufacturing Automation Clipart PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Role Of Cyber Security In Manufacturing Automation Clipart PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Cyber Security In Manufacturing Automation Clipart PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home