Cyber Attack

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
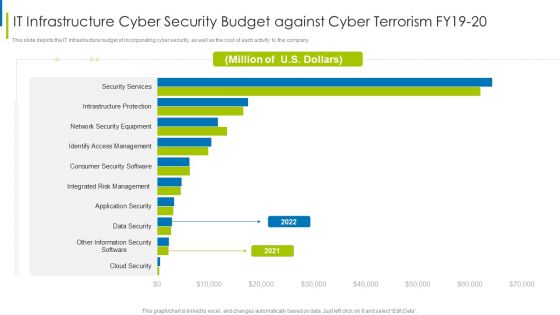
Cyber Terrorism Assault IT Infrastructure Cyber Security Budget Against Cyber Terrorism FY19 20 Themes PDF
This slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault it infrastructure cyber security budget against cyber terrorism fy19 20 themes pdf Use them to share invaluable insights on cloud security, integrated risk management, identify access management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism Template PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts.Presenting cyber terrorism assault roadmap to implement cyber security to mitigate cyber terrorism template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating personal accounts, awareness training, keep the hardware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Terrorism Assault Cyber Terrorism Faced By Companies In US Mockup PDF
This slide depicts the cyber terrorism attacks faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver and pitch your topic in the best possible manner with this cyber terrorism assault cyber terrorism faced by companies in us mockup pdf Use them to share invaluable insights on Consequences Of Cyber Attacks, Response Planning, Recovery Strategies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
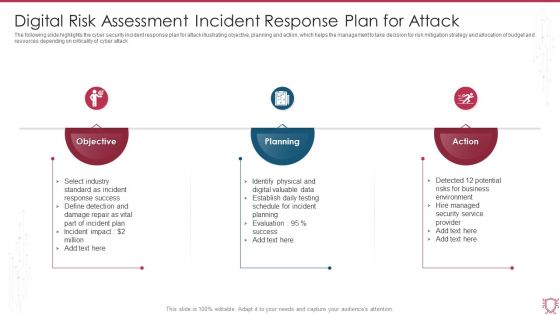
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Terrorism Assault Dashboard For Threat Tracking Of Cyber Terrorism Themes PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault dashboard for threat tracking of cyber terrorism themes pdf Use them to share invaluable insights on Massive Increase, Cyber Attacks Happened, Company Experienced and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF
This slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Persuade your audience using this IT Security Attack Vector Analysis For Effective Awareness Training Program Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Attack Vector, Examples, Objective Problem Identifier. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
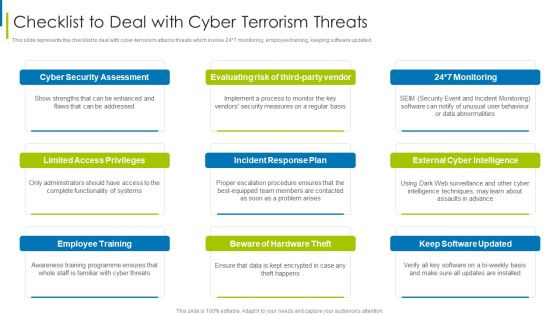
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Cyber Terrorism Faced By Various Industries Pictures PDF
This slide describes the cyber terrorism attacks various industries face, including health, finance, media, transportation and education.Deliver an awe inspiring pitch with this creative cyber terrorism assault cyber terrorism faced by various industries pictures pdf bundle. Topics like Cyber Terrorism Faced By Companies In US can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
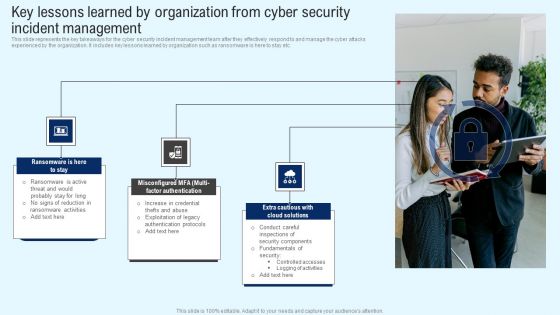
Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Present like a pro with Implementing Cyber Security Incident Key Lessons Learned By Organization From Cyber Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Terrorism Assault Malicious Code Malware Misused For Cyber Terrorism Pictures PDF
This slide depicts the malicious code or malware misused for cyber terrorism attacks to hijack or access information from computers.Presenting cyber terrorism assault malicious code malware misused for cyber terrorism pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like broad spectrum, executed by changing, programmer by stopping In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
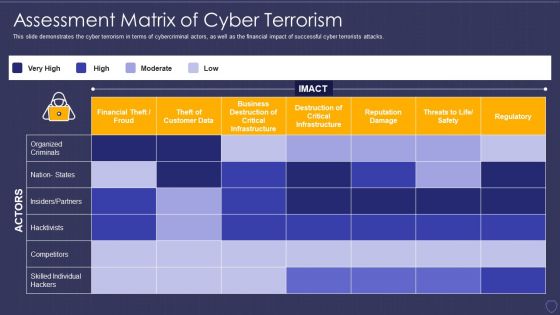
Global Cyber Terrorism Incidents On The Rise IT Assessment Matrix Of Cyber Terrorism Ideas PDF
This slide demonstrates the cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it assessment matrix of cyber terrorism ideas pdf bundle. Topics like financial theft or froud, reputation damage, regulatory, competitors, destruction of critical infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
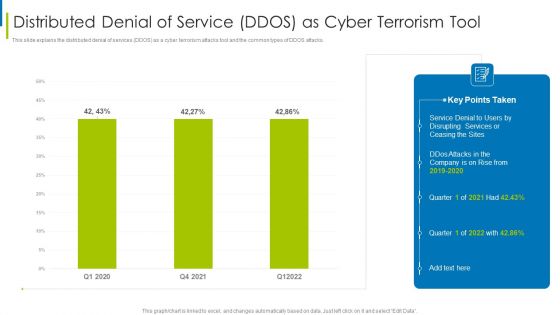
Cyber Terrorism Assault Distributed Denial Of Service DDOS As Cyber Terrorism Tool Slides PDF
This slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault distributed denial of service ddos as cyber terrorism tool slides pdf Use them to share invaluable insights on Make A Risk Assessment, Determine The Importance Of Assets, Make A Complete Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Three Major Forms Of Cyber Terrorism Brochure PDF
This slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack.This is a cyber terrorism assault three major forms of cyber terrorism brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privacy violation, networks damage and disruptions, distributed denial You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Risks And Incident Response Playbook Identifying The Origin And Type Of Cyber Incident Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Cyber Terrorism Assault Simple Advanced And Complex Types Of Cyber Terrorism Structure PDF
This slide explains the simple advanced and complex types of cyber terrorism attacks i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world.This is a cyber terrorism assault simple advanced and complex types of cyber terrorism structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like simple structured, advanced structured, complex coordinated You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Terrorism Assault Types Of Trojans Misused In Cyber Terrorism Background PDF
This slide describes the types of trojans misused in cyber terrorism attacks such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Presenting cyber terrorism assault types of trojans misused in cyber terrorism background pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like backdoor trojan, downloader trojan, rootkit trojans In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Incident Response Lifecycle Information PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Presenting this PowerPoint presentation, titled Cyber Security Incident Response Lifecycle Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Security Incident Response Lifecycle Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Security Incident Response Lifecycle Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
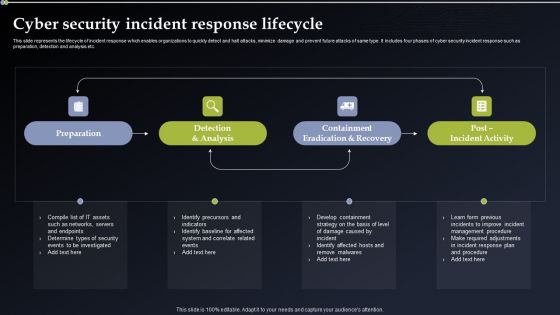
Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you searching for a Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Cyber Security Incident Response Administration Various Cyber Security Incidents Detected By IT Department Portrait PDF from Slidegeeks today.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Cyber Physical Systems In Water Distribution Systems Portrait PDF bundle. Topics like Network, Data Acquisition Systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impacts Of Cyber Security Data Compliance
Want to ace your presentation in front of a live audience Our Impacts Of Cyber Security Data Compliance can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
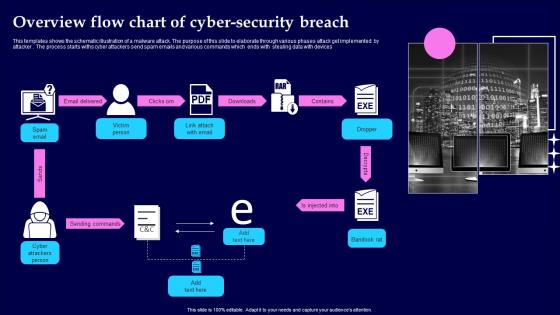
Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
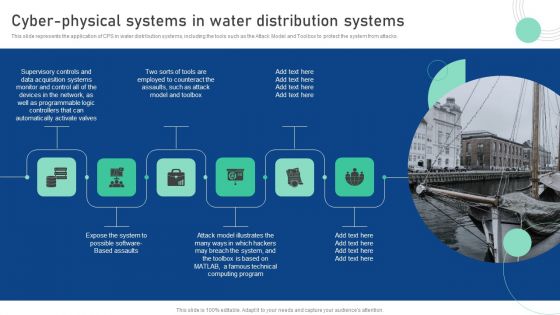
Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF
This slide represents the application of CPS in water distribution systems, including the tools such as the Attack Model and Toolbox to protect the system from attacks. This Cyber Physical System To Enhance Cyber Physical Systems In Water Distribution Summary PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Data Wiper Spyware Attack Information And Technology Army Of Ukraine Structure PDF
This slide represents the information and technology army of Ukraine, a Telegram group against Russia. In total, 308,000 users have joined this group to help Ukraine mitigate Russian cyber attacks.This is a data wiper spyware attack information and technology army of ukraine structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prevent misinformation, provide factual information, russian residents You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
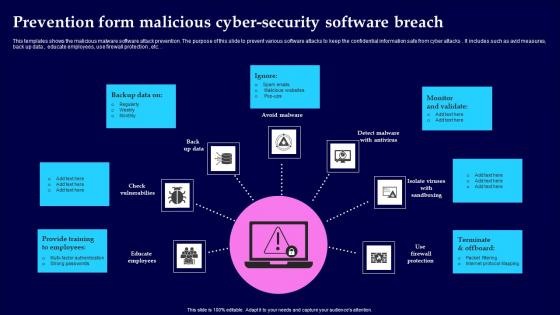
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
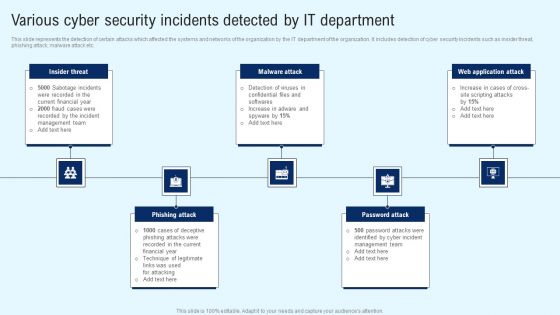
Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Various Cyber Security Incidents Detected Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
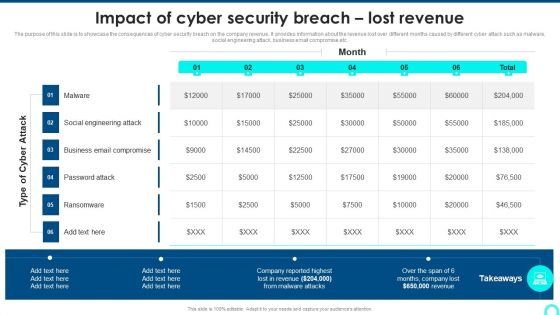
Impact Of Cyber Security Breach Lost Revenue Portrait PDF
The purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Deliver an awe inspiring pitch with this creative Impact Of Cyber Security Breach Lost Revenue Portrait PDF bundle. Topics like Social Engineering, Password Attack, Ransomware can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
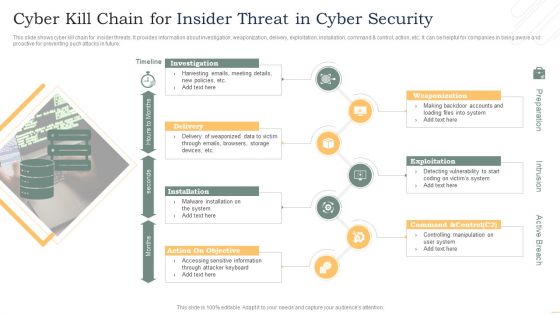
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Need For Cyber Security Awareness Training Professional PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Presenting Need For Cyber Security Awareness Training Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organization Different, Technological Defenses, Awareness Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Three Major Forms Of Cyber Terrorism Topics PDF
This slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Presenting global cyber terrorism incidents on the rise it three major forms of cyber terrorism topics pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like privacy violation, networks damage and disruptions, distributed denial of service attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Make sure to capture your audiences attention in your business displays with our gratis customizable CYBER Security Breache Response Strategy Cyber Security Incident Response Lifecycle Icons PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
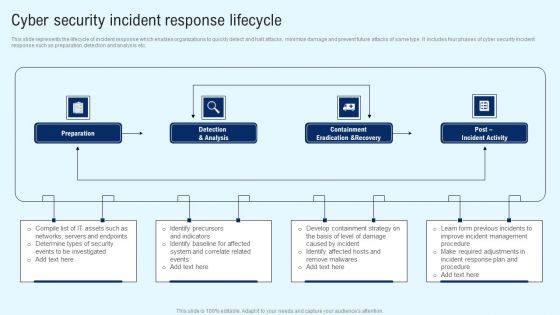
Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides
This slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Importance Of Cyber Threat Intelligence Program Threat Intelligence Ppt Slides. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Compliance System Standards Demonstration Pdf
This slide shows essential cyber security standards that are necessary to be followed for fulfilling requirements of standard compliance program. It include cyber security standards such as ISO 27001, HIPAA and PCI DSS etc. Showcasing this set of slides titled Cyber Security Compliance System Standards Demonstration Pdf. The topics addressed in these templates are International Organization, Health Insurance, Payment Card Industry. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Strategic Agenda Process Demonstration Pdf
This slide illustrates action plan process of cyber security. It further consists steps such as system hygiene, plan development, create risk profile, evaluate and measure, minimize risk, cyber insurance, etc. Showcasing this set of slides titled Cyber Security Strategic Agenda Process Demonstration Pdf. The topics addressed in these templates are System Hygiene, Plan Development, Evaluate And Measure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.
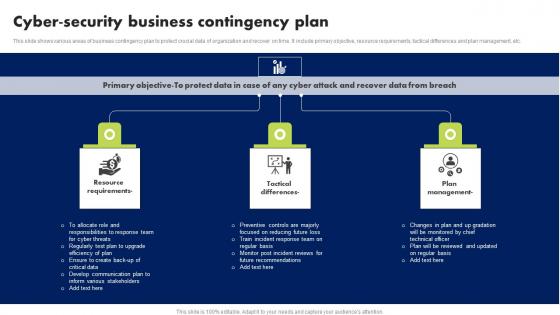
Cyber Security Business Contingency Plan Brochure Pdf
This slide shows various areas of business contingency plan to protect crucial data of organization and recover on time. It include primary objective, resource requirements, tactical differences and plan management, etc. Showcasing this set of slides titled Cyber Security Business Contingency Plan Brochure Pdf. The topics addressed in these templates are Resource Requirements, Tactical Differences, Plan Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
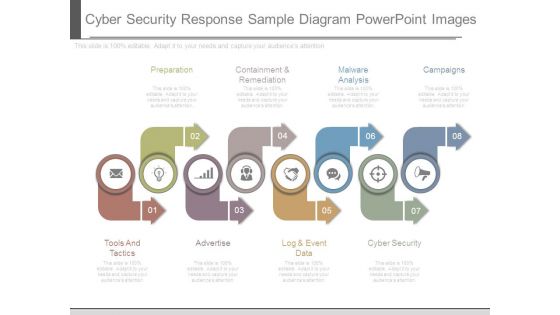
Cyber Security Response Sample Diagram Powerpoint Images
This is a cyber security response sample diagram powerpoint images. This is a eight stage process. The stages in this process are preparation, containment and remediation, malware analysis, campaigns, cyber security, log and event data, advertise, tools and tactics.

Cyber Management Template Presentation Background Images
This is a cyber management template presentation background images. This is a six stage process. The stages in this process are risk review, policy, audit, cyber security life cycle, implementation, administration.

Cyber Crime Investigation Process Stages Pictures PDF
The slide carries a investigation workflow stages for tracking and solving cyber crime issues. Various steps included are background checks, gather information, run digital forensics and track the information Persuade your audience using this Cyber Crime Investigation Process Stages Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Background Checks, Gather Information, Run Digital Forensics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Security Ppt PowerPoint Presentation Styles Inspiration
This is a cyber security ppt powerpoint presentation styles inspiration. This is a three stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
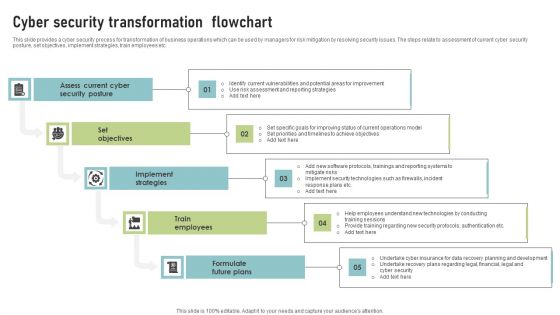
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.

Cyber Security Ppt PowerPoint Presentation Layouts Brochure
This is a cyber security ppt powerpoint presentation layouts brochure. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing.
Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
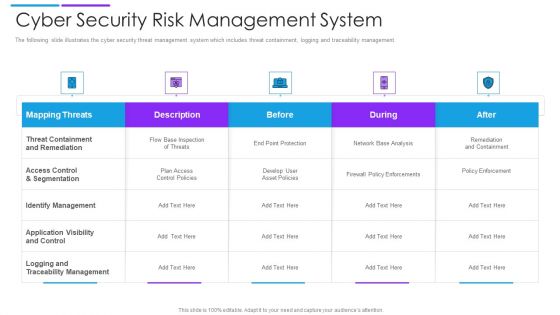
Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
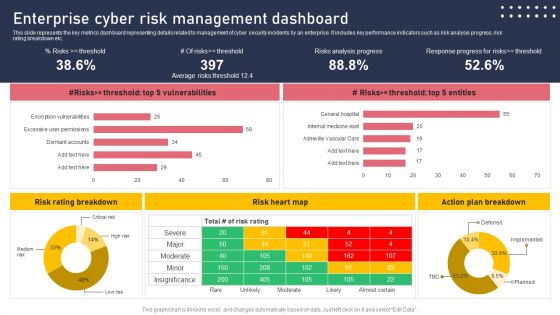
Enterprise Cyber Risk Management Dashboard Sample PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. There are so many reasons you need a Enterprise Cyber Risk Management Dashboard Sample PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Cyber Terrorism Assault Professional PDF
This is a agenda for cyber terrorism assault professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Cyber Security Management Model Graphics PDF
This slide showcases a framework for cyber security risk governance and management model to align business and IT objectives. It includes key components such as analysis, design, specification, implementation, testing, production, operations, etc. Presenting Business Cyber Security Management Model Graphics PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Security Guidelines, Security Organization, Cybersecurity Governance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Incident Communication Strategy Information PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Communication Strategy Information PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Communication Strategy Information PDF.

 Home
Home