Customer Problem

Opportunities And Threats For Penetrating In New Market Segments Value Proposition Analysis Price Structure PDF
How attractive is the value proposition via-a-vis competitors. Deliver an awe inspiring pitch with this creative opportunities and threats for penetrating in new market segments value proposition analysis price structure pdf bundle. Topics like product quality, packaging, ease of use, price, effectiveness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environmental Assessment STEP Analysis For Opportunity And Threat Evaluation Ppt Gallery Templates PDF
This slide shows STEP analysis to analyze likelihood, importance and influence of political, economic, social and technological factors on organizational activities Deliver an awe inspiring pitch with this creative environmental assessment step analysis for opportunity and threat evaluation ppt gallery templates pdf bundle. Topics like economic, technological, social can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

How To Intensify Project Threats Gantt Chart With Project Progress Bar Elements PDF
This slide provides the glimpse about the project progress bar graph in gantt chart form which covers the general release, open and closed beta and development. Deliver an awe inspiring pitch with this creative how to intensify project threats gantt chart with project progress bar elements pdf bundle. Topics like development, closed beta, open beta, general released. can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

How To Intensify Project Threats Delay And Over Run Cost In The Projects Topics PDF
This slide provides the glimpse about the delay and over run project costs graph wherein the number of projects has been monitored, along with delayed projects and cost overrun. Deliver an awe inspiring pitch with this creative how to intensify project threats delay and over run cost in the projects topics pdf bundle. Topics like monitored, delayed projects, cost overrun can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Budget For Effective Threat Management At Workplace Structure PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative cyber security administration in organization budget for effective threat management at workplace structure pdf bundle. Topics like incident management, onboarding, process, release can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Model Graphics PDF
This slide shows the details on tasks involved in allocate requirements stage of solution assessment and validation along with the categories of requirements. Deliver an awe inspiring pitch with this creative solution evaluation criteria assessment and threat impact matrix solution assessment and validation model graphics pdf bundle. Topics like allocate requirements categories, allocate requirements description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
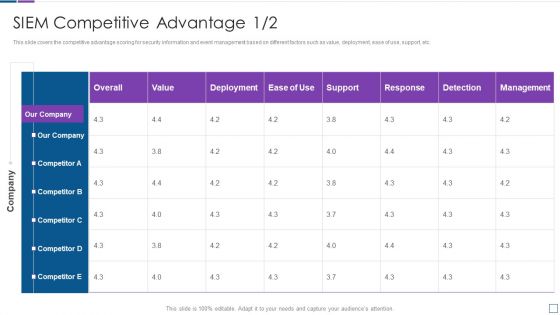
Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
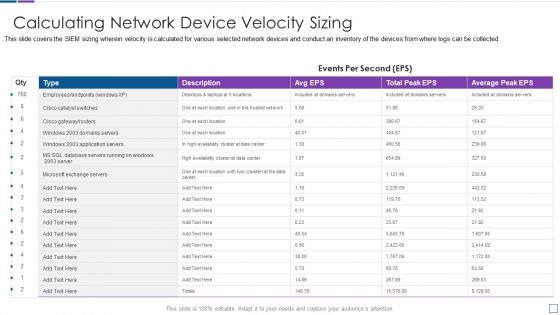
Real Time Assessment Of Security Threats Calculating Network Device Velocity Sizing Portrait PDF
This slide covers the SIEM sizing wherein velocity is calculated for various selected network devices and conduct an inventory of the devices from where logs can be collected. Deliver an awe inspiring pitch with this creative real time assessment of security threats calculating network device velocity sizing portrait pdf bundle. Topics like calculating network device velocity sizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
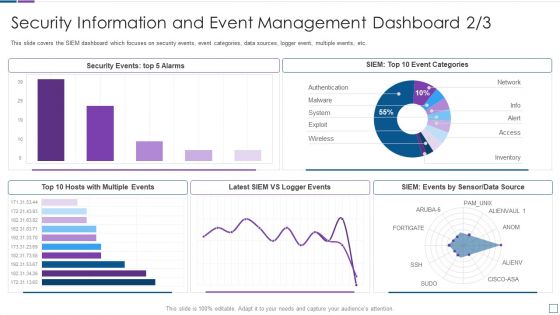
Real Time Assessment Of Security Threats Security Information And Event Management Dashboard Infographics PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative real time assessment of security threats security information and event management dashboard infographics pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
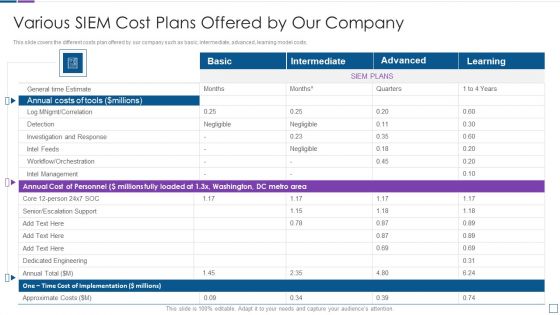
Real Time Assessment Of Security Threats Various SIEM Cost Plans Offered By Our Company Topics PDF
This slide covers the different costs plan offered by our company such as basic, intermediate, advanced, learning model costs. Deliver an awe inspiring pitch with this creative real time assessment of security threats various siem cost plans offered by our company topics pdf bundle. Topics like annual costs of tools, annual cost of personnel, one time cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Flow Diagram Of Incident Response Process Ppt Infographics Inspiration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative handling cyber threats digital era flow diagram of incident response process ppt infographics inspiration pdf bundle. Topics like preparatory, remediate eradicate, analyse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
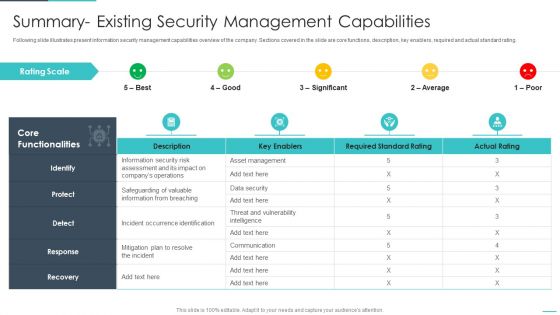
Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Checklist For Effectively Managing Asset Security Ppt Slides Example File PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative handling cyber threats digital era checklist for effectively managing asset security ppt slides example file pdf bundle. Topics like checklist for effectively managing asset security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Handling Cyber Threats Digital Era Introducing New Incidents Logging Process Ppt Slides Graphic Images PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver an awe inspiring pitch with this creative handling cyber threats digital era introducing new incidents logging process ppt slides graphic images pdf bundle. Topics like introducing new incidents logging process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
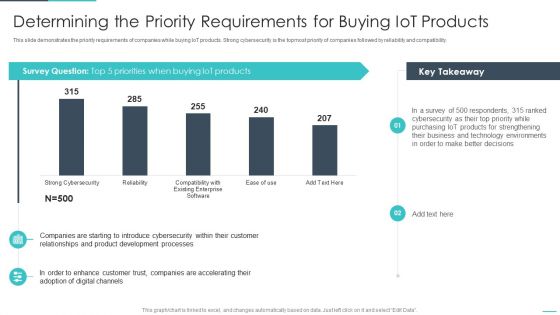
Handling Cyber Threats Digital Era Determining The Priority Requirements Ppt Outline Visual Aids PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative handling cyber threats digital era determining the priority requirements ppt outline visual aids pdf bundle. Topics like determining the priority requirements for buying iot products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Threat Management At Workplace Addressing Critical Business Functions Recovery Priorities Formats Pdf
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative threat management at workplace addressing critical business functions recovery priorities formats pdf bundle. Topics like priorities, department, maximum allowable downtime can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
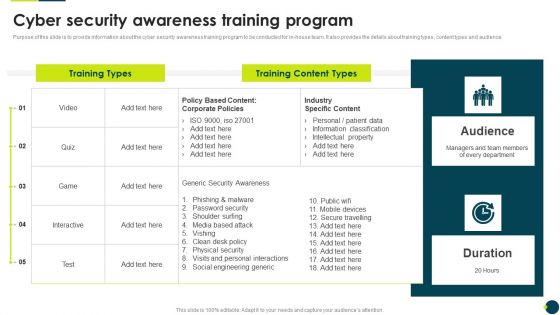
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
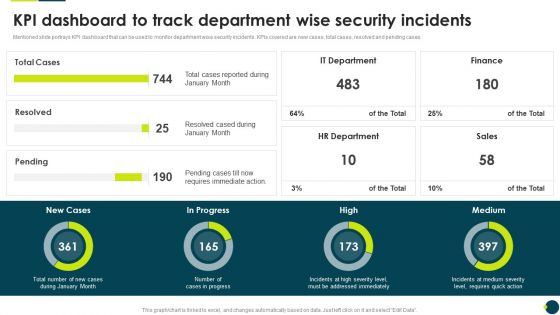
IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Clipart PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an awe inspiring pitch with this creative comparative assessment of various threat agents affecting overall project safety clipart pdf bundle. Topics like threat agents, attack on, data loss impact, resource requirement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Convenience Food Business Plan Porters Five Forces For Fast Food Restaurant Business Microsoft PDF
The purpose of this slide is to provide glimpse about the porters five forces model. This is a convenience food business plan porters five forces for fast food restaurant business microsoft pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like barriers entry, threat competition, bargaining power, clients, bargaining power company, intensity rivalry. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Plan For Fast Food Restaurant Porters Five Forces For Food Startup Business Brochure PDF
The purpose of this slide is to provide glimpse about the Porters Five Forces Model. Presenting business plan for fast food restaurant porters five forces for food startup business brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like barriers to entry, threat of competition, bargaining power of clients, bargaining power of company, intensity of rivalry. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Current Challenges Faced By B2B Marketers Ppt Summary Icon PDF
This slide covers the challenges faced by the B2B marketers along with the solutions to overcome such challenges.Deliver an awe-inspiring pitch with this creative current challenges faced by B2B marketers ppt summary icon pdf. bundle. Topics like challenges, solution, technology integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenges And Solutions In Vendor Management Ppt Gallery Format Ideas PDF
This slide shows the challenges that the company must face and the related solutions while dealing with vendors such as complex vendor ecosystem, contract management challenges, reputational risk, data storage challenges, vendor payment challenges etc. Deliver an awe-inspiring pitch with this creative challenges and solutions in vendor management ppt gallery format ideas pdf bundle. Topics like reputational risk, data storage, complex vendor ecosystem can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
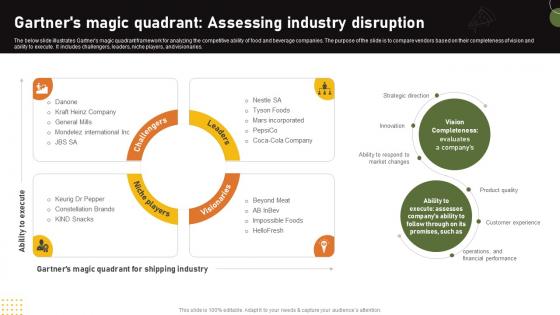
Food And Drink Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V
The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of food and beverage companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Food And Drink Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V can be your best option for delivering a presentation. Represent everything in detail using Food And Drink Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Based Email Security Market Report Issues Faced By Companies Services Ppt Pictures Slide Portrait PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Deliver an awe inspiring pitch with this creative cloud based email security market report issues faced by companies services ppt pictures slide portrait pdf bundle. Topics like issues faced by companies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
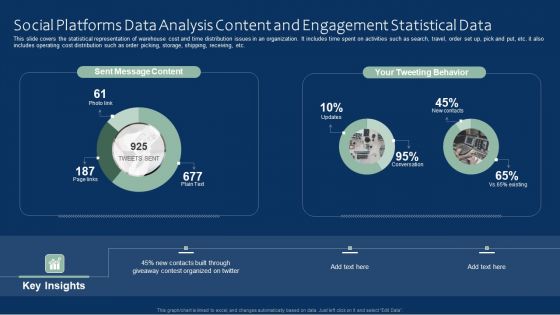
Social Platforms Data Analysis Content And Engagement Statistical Data Microsoft PDF
This slide covers the statistical representation of warehouse cost and time distribution issues in an organization. It includes time spent on activities such as search, travel, order set up, pick and put, etc. it also includes operating cost distribution such as order picking, storage, shipping, receiving, etc. Showcasing this set of slides titled Social Platforms Data Analysis Content And Engagement Statistical Data Microsoft PDF. The topics addressed in these templates are Social Platforms Data, Analysis Content, Engagement Statistical Data. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
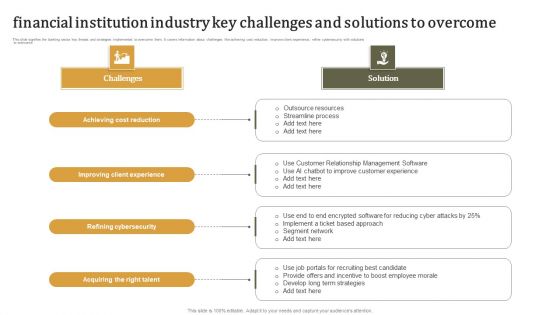
Financial Institution Industry Key Challenges And Solutions To Overcome Introduction PDF
This slide signifies the banking sector key threats and strategies implemented to overcome them. It covers information about challenges like achieving cost reduction, improve client experience, refine cybersecurity with solutions to overcome. Presenting Financial Institution Industry Key Challenges And Solutions To Overcome Introduction PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Financial Institution Industry, Key Challenges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
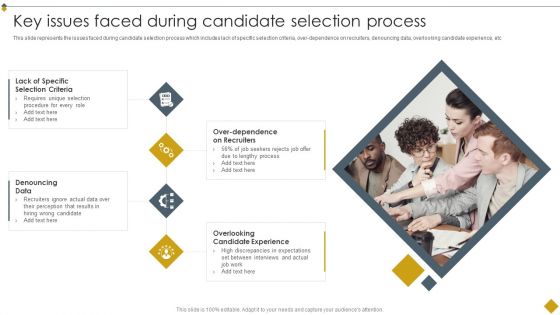
Techniques To Boost Selection Process Key Issues Faced During Candidate Selection Process Formats PDF
This slide represents the issues faced during candidate selection process which includes lack of specific selection criteria, over-dependence on recruiters, denouncing data, overlooking candidate experience, etc.Slidegeeks has constructed Techniques To Boost Selection Process Key Issues Faced During Candidate Selection Process Formats PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Instigating Efficient Value Process Vendor Risk Management Process Graphics PDF
Following slide shows vendor risk management process. It includes three stages namely vendor risk classification, assess vendor and manage issue. Deliver an awe inspiring pitch with this creative instigating efficient value process vendor risk management process graphics pdf bundle. Topics like inventory vendors, relationship, assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Vertical Communication Plan Implementation Challenges With Solutions Ideas PDF
Presenting Vertical Communication Plan Implementation Challenges With Solutions Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Message Delivery Icon, Vertical Communication Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Methodology Quality Risk Reduction Plan Sample PDF
This slide covers risk control and reduction plan including work area or objectives, action taken, indicators to measure, timeframe and responsible department. The Risk Based Methodology Quality Risk Reduction Plan Sample PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information And Technology Security Operations How Firm Handle Insider Threats Pictures PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a information and technology security operations how firm handle insider threats pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration How Firm Handle Insider Threats Structure PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a enhanced protection corporate event administration how firm handle insider threats structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration How Firm Handle Insider Threats Template PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security and process integration how firm handle insider threats template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Evolving BI Infrastructure How Firm Handle Various Insider Threats At Workplace Topics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a evolving bi infrastructure how firm handle various insider threats at workplace topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Intelligent Infrastructure How Firm Handle Various Insider Threats At Workplace Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Intelligent Infrastructure How Firm Handle Various Insider Threats At Workplace Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, IT Security And HR Coordination, Develop Threat Hunting Team, Implement User Behavioral Analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
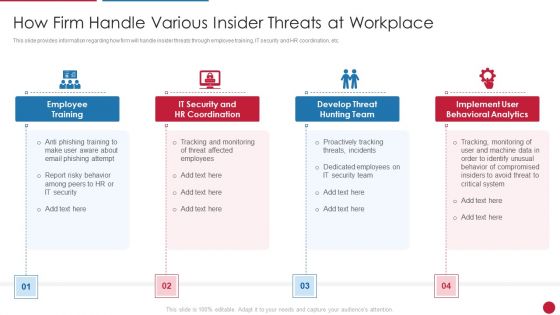
Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Develop Threat Hunting Team, Implement User Behavioral Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
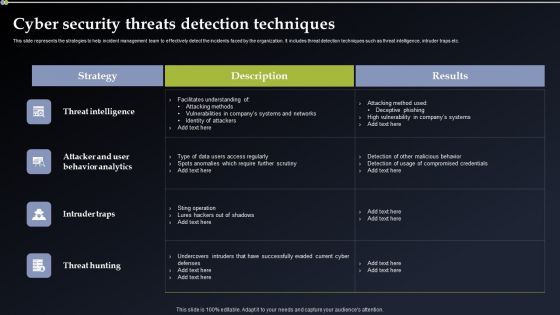
Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Want to ace your presentation in front of a live audience Our Deploying Cyber Security Incident Response Administration Cyber Security Threats Detection Techniques Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Four Supply Chain And Distribution Network Challenges Mockup PDF
This slide covers top supply chain challenges faced by manufactures and producers. It includes challenges such as increased costs, supply chain complexities, consumer demand drive and supply chain volatility. Showcasing this set of slides titled Four Supply Chain And Distribution Network Challenges Mockup PDF. The topics addressed in these templates are Factors, Solution, Challenges. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Challenges Faced While Software Product Promotion Strategy Topics PDF
Following slides depicts the various challenges faced by a software company while doing their product marketing which hinderers the growing revenue for an organization. The challenges are new clients, retaining existing clients, etc. Presenting Challenges Faced While Software Product Promotion Strategy Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Retaining Existing Clients, Improve Email Marketing, Time Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Project Initiation Ensuring Project Success By Overcoming Challenges Structure PDF
Mentioned slide portrays information about the focus areas on which company will work upon in order to overcome project challenges. Focus Areas covered are low workplace productivity, poor risk management and poor communication This is a information technology project initiation ensuring project success by overcoming challenges structure pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like low workplace productivity, poor risk management, poor communication, focus areas. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Handling Cyber Threats Digital Era Communication Plan For Cyber Breaches Ppt Icon Background Images PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era communication plan for cyber breaches ppt icon background images pdf. Use them to share invaluable insights on communication plan for cyber breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
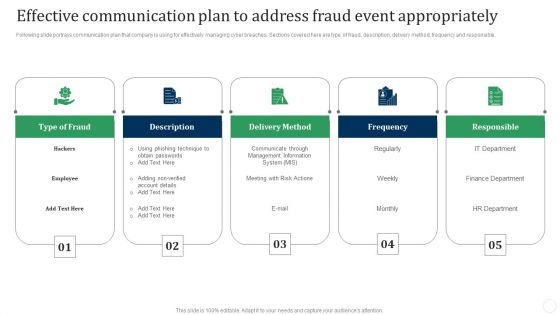
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Recognition Automation Next Evolution Of Siem Software Ppt Ideas Objects PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting risk recognition automation next evolution of siem software ppt ideas objects pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, threat intelligence, siem foundation, user entity and behavior analytics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
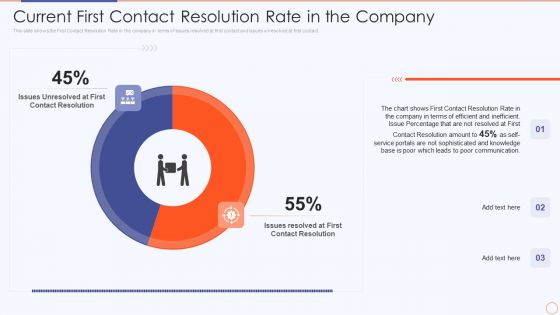
Streamlining HR Service Delivery To Ensure Organizational Transformation Current First Contact Resolution Background PDF
This slide shows the First Contact Resolution Rate in the company in terms of issues resolved at first contact and issues unresolved at first contact. Deliver an awe inspiring pitch with this creative streamlining hr service delivery to ensure organizational transformation current first contact resolution background pdf bundle. Topics like current first contact resolution rate in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
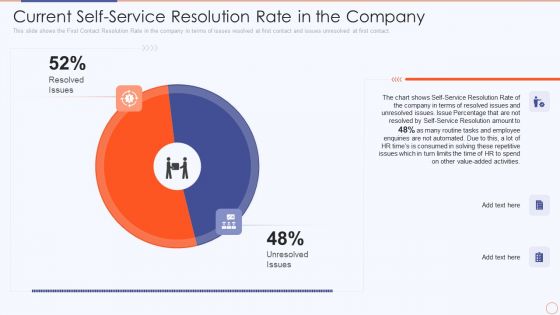
Streamlining HR Service Delivery To Ensure Organizational Transformation Current Self Service Resolution Formats PDF
This slide shows the First Contact Resolution Rate in the company in terms of issues resolved at first contact and issues unresolved at first contact. Deliver an awe inspiring pitch with this creative streamlining hr service delivery to ensure organizational transformation current self service resolution formats pdf bundle. Topics like current self service resolution rate in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digital Transformation Of Consumer Barriers Related To Digital Effectiveness In Banking Elements PDF
This slide shows the barriers which effects the digital effectiveness in banking company which includes Cultural challenges, technical challenges, lack of innovation, lack of IT Infrastructure, etc. Deliver an awe inspiring pitch with this creative Digital Transformation Of Consumer Barriers Related To Digital Effectiveness In Banking Elements PDF bundle. Topics like Digital Effectiveness, Lack Innovation, Technical Challenges can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Major Risk And Their Mitigation Strategies Ppt Icon Styles PDF
This slide shows the various risks Changes in Consumer Preferences, High Competition, Growing concerns about health, etc. and their mitigation strategies. Deliver an awe inspiring pitch with this creative major risk and their mitigation strategies ppt icon styles pdf bundle. Topics like growing concerns about health, consumer preferences, risk mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
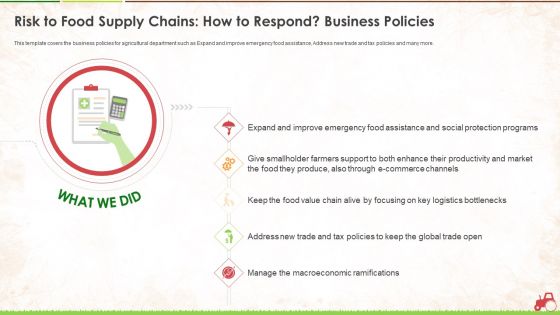
Risk To Food Supply Chains How To Respond Business Policies Ppt Outline Background PDF
This template covers the business policies for agricultural department such as Expand and improve emergency food assistance, Address new trade and tax policies and many more. This is a risk to food supply chains how to respond business policies ppt outline background pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk to food supply chains how to respond business policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
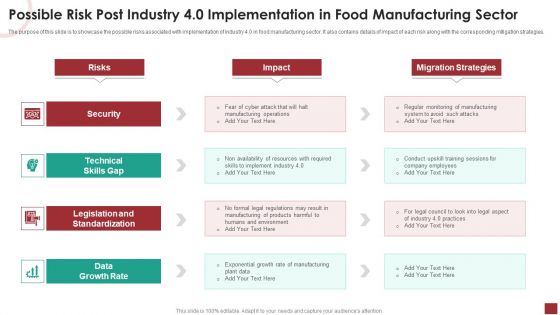
Possible Risk Post Industry 4 0 Implementation In Food Manufacturing Sector Designs PDF
The purpose of this slide is to showcase the possible risks associated with implementation of industry 4.0 in food manufacturing sector. It also contains details of impact of each risk along with the corresponding mitigation strategies.Presenting Possible Risk Post Industry 4 0 Implementation In Food Manufacturing Sector Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Legislation And Standardization, Technical Skills, Data Growth Rate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home