Authentication

API Management For Building Software Applications Features Of Our Application Programming Interface Ideas PDF
Presenting this set of slides with name api management for building software applications features of our application programming interface ideas pdf. This is a six stage process. The stages in this process are high performance, load balancing, security, rate limiting, authentication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
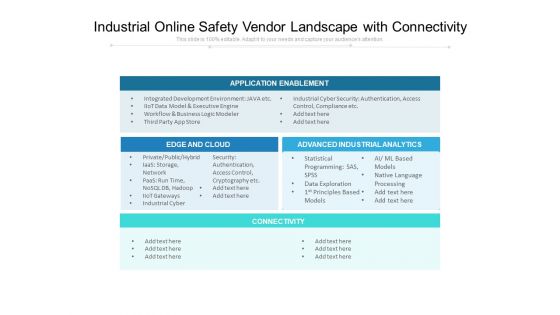
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Processing Cloud Services Icon Infographics PDF
Pitch your topic with ease and precision using this Data Processing Cloud Services Icon Infographics PDF. This layout presents information on Security Compliance, Monitor Visibility, Authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

IT Support And Monitoring Services Pricing IT Application And Managed Services Dashboard Rules PDF
Presenting this set of slides with name it support and monitoring services pricing it application and managed services dashboard rules pdf. The topics discussed in these slides are authentication, application whitelisting, operating systems, privileges. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
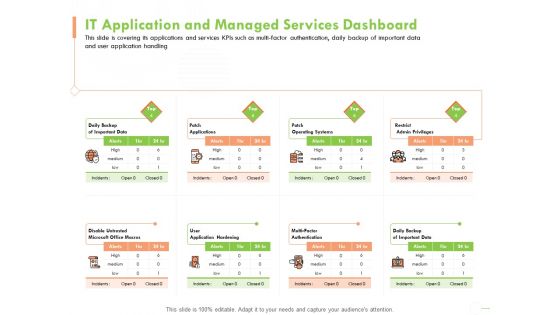
Welfare Work Value IT Application And Managed Services Dashboard Ppt Inspiration Styles PDF
Presenting this set of slides with name welfare work value it application and managed services dashboard ppt inspiration styles pdf. The topics discussed in these slides are application hardening, authentication, data, operating systems. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
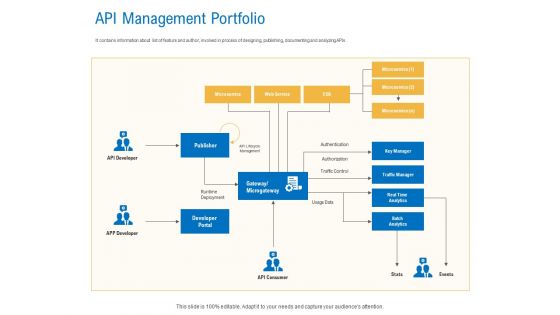
Digital Businesses Ecosystems API Management Portfolio Demonstration PDF
Deliver an awe inspiring pitch with this creative digital businesses ecosystems api management portfolio demonstration pdf bundle. Topics like service, analytics, microservice, authentication, traffic control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
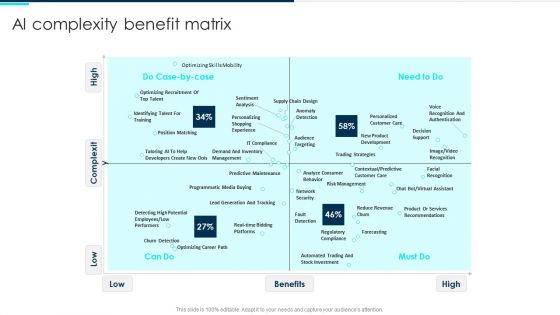
Ai Complexity Benefit Matrix Deploying Artificial Intelligence In Business Information PDF
Deliver an awe inspiring pitch with this creative Ai Complexity Benefit Matrix Deploying Artificial Intelligence In Business Information PDF bundle. Topics like Optimizing Recruitment, Recognition Authentication, Automated Trading can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Resource Optimization Plan For Implementing It Project Diagrams PDF
Showcasing this set of slides titled Resource Optimization Plan For Implementing It Project Diagrams PDF. The topics addressed in these templates are Presentation Preparation, Implement Authentication, Database Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the application of digital wallets to enhance the security of e-commerce platforms. Key technologies are tokenization, biometric authentication, and two-factor authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Enhancing E Commerce Security With Digital Wallets In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Five Elements Of Cloud Services Security Brochure PDF
This slide includes elements of cloud computing security to assure network protection and efficient management. It contains five elements architecture, security, due diligence, authentication, monitor and visibility.Presenting Five Elements Of Cloud Services Security Brochure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Coverage, Intrusion Detection, Computing Regulations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF
This slide describes the enterprise cloud security solutions, including multi-factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost-benefits of hybrid cloud.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Enterprise Cloud Security Solutions Introduction PDF. Use them to share invaluable insights on Manage Accounts, Services Proactively, Processes Fingerprints and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
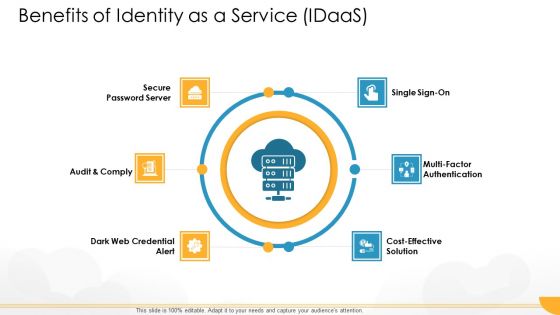
Technology Guide For Serverless Computing Benefits Of Identity As A Service Idaas Summary PDF
This is a technology guide for serverless computing benefits of identity as a service idaas summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like secure password server, audit and comply, cost effective solution, multi factor authentication, dark web credential alert. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
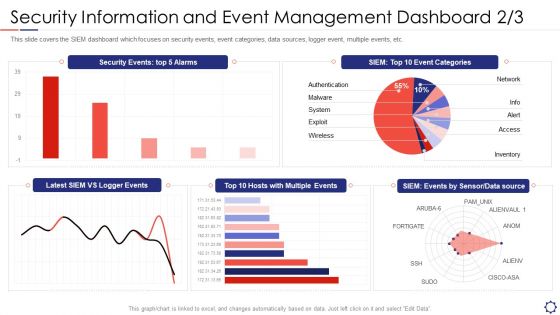
SIEM Security Information And Event Management Dashboard Exploit Slides PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver and pitch your topic in the best possible manner with this siem security information and event management dashboard exploit slides pdf. Use them to share invaluable insights on network, authentication, wireless, inventory, access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
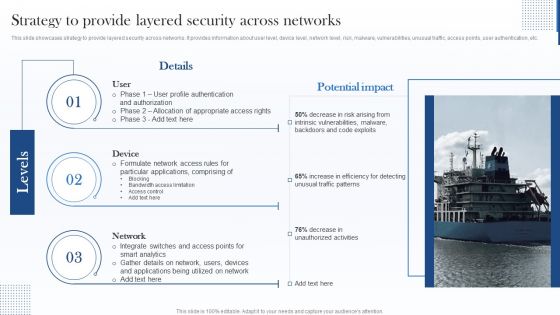
Strategy To Provide Layered Security Across Networks Microsoft PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an awe inspiring pitch with this creative Strategy To Provide Layered Security Across Networks Microsoft PDF bundle. Topics like Device, Network, Applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Music Streaming App Competitive Landscape For Major Music Streaming Players Existing Portrait PDF
This slide caters details about competitive landscape of various competitors existing in music streaming market by comparing them on various parameters or features. Deliver an awe inspiring pitch with this creative music streaming app competitive landscape for major music streaming players existing portrait pdf bundle. Topics like login authentication, music categorization, curated music playlists can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Competitive Landscape For Major Music Streaming Players Existing Rules PDF
This slide caters details about competitive landscape of various competitors existing in music streaming market by comparing them on various parameters or features. Deliver and pitch your topic in the best possible manner with this competitive landscape for major music streaming players existing rules pdf. Use them to share invaluable insights on music categorization, registration and login authentication, social media integrations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
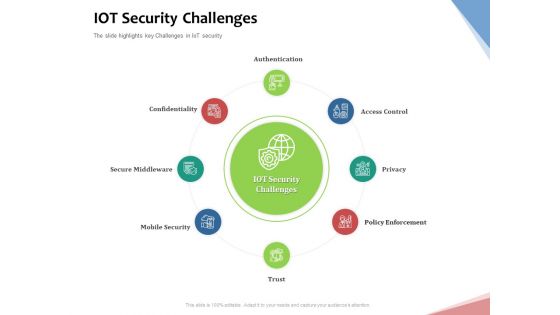
Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
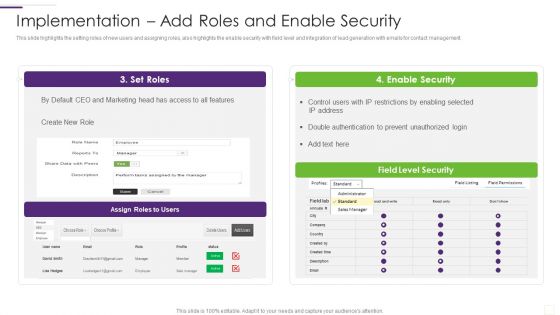
CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Implementation Strategy Implementation Add Roles And Enable Security Rules PDF bundle. Topics like Enable Security, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
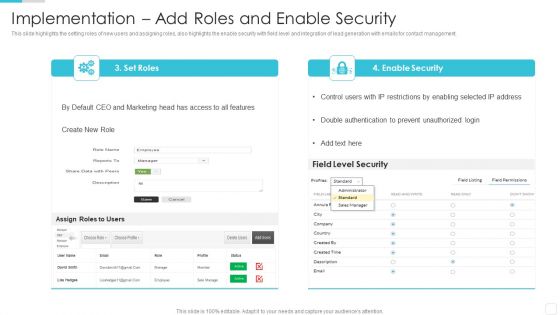
Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF bundle. Topics like Restrictions By Enabling, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Strategies To Mitigate Cyber Security Risks Dashboard Incident Tracking Ppt Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard incident tracking ppt model pdf. The topics discussed in these slides are application whitelisting, patch applications, patch operating systems, restrict admin privileges, disable untrusted microsoft office macros, user application hardening, multi factor authentication, daily backup important data. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
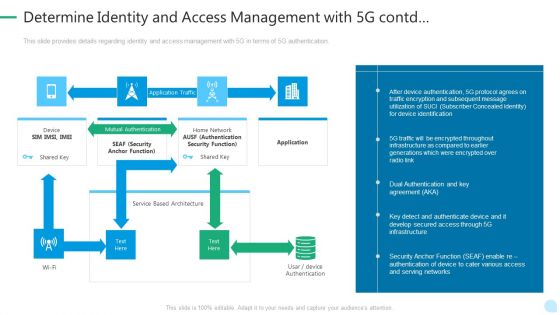
5G Network Technology Determine Identity And Access Management With 5G Contd Ppt Outline Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver an awe inspiring pitch with this creative 5g network technology determine identity and access management with 5g contd ppt outline background pdf bundle. Topics like security, develop, infrastructure, protocol can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Determine Identity And Access Management With 5G Contd Microsoft PDF Use them to share invaluable insights on Uthentication, Security Function, Based Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
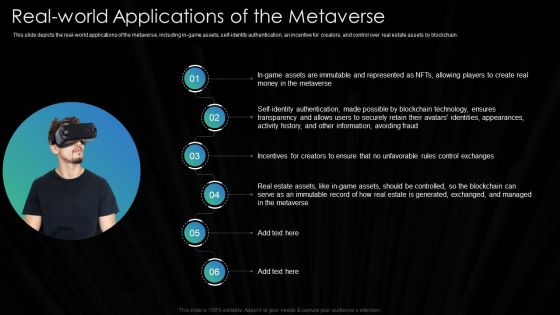
Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF
This slide depicts the real-world applications of the metaverse, including in-game assets, self-identity authentication, an incentive for creators, and control over real estate assets by blockchain. Deliver an awe inspiring pitch with this creative Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF bundle. Topics like Avoiding Fraud, Avatars Identities, Securely Retain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Identity And Access Management With 5G Contd Information PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Determine Identity And Access Management With 5G Contd Information PDF. Use them to share invaluable insights on Application Traffic, Security, Network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
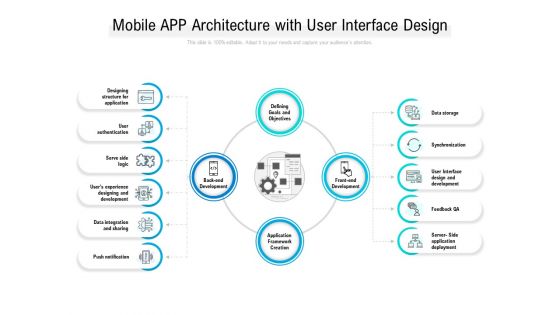
Mobile App Architecture With User Interface Design Ppt PowerPoint Presentation Pictures Examples
Presenting this set of slides with name mobile app architecture with user interface design ppt powerpoint presentation pictures examples. This is a four stage process. The stages in this process are data storage, synchronization, user interface design and development, feedback qa, server side application deployment, defining goals and objectives, push notification, data integration and sharing, users experience designing and development, user authentication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
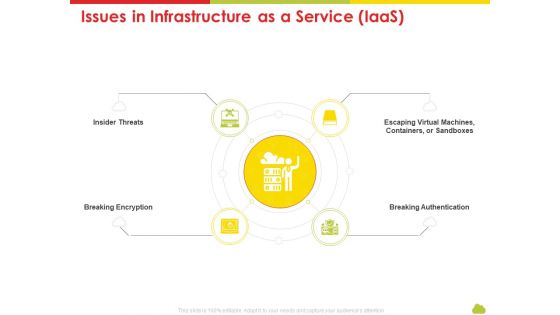
Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Issues In Infrastructure As A Service Iaas Ideas PDF
This is a mesh computing technology hybrid private public iaas paas saas workplan issues in infrastructure as a service iaas ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, escaping virtual machines, containers, or sandboxes, breaking authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Managed IT Services Pricing Model IT Application And Managed Services Dashboard Clipart PDF
This slide is covering its applications and services KPIs such as multi-factor authentication, daily backup of important data and user application handling. Deliver and pitch your topic in the best possible manner with this managed it services pricing model it application and managed services dashboard clipart pdf. Use them to share invaluable insights on application whitelisting, patch applications, patch operating systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
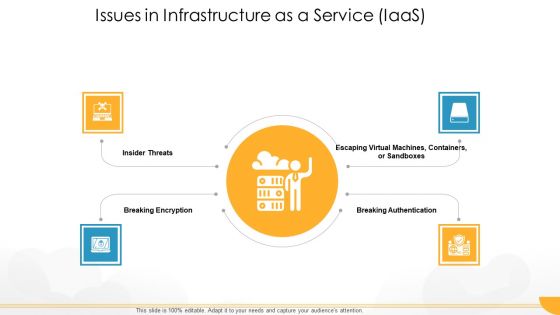
Technology Guide For Serverless Computing Issues In Infrastructure As A Service Iaas Diagrams PDF
This is a technology guide for serverless computing issues in infrastructure as a service iaas diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insider threats, breaking encryption, breaking authentication, virtual machines. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Important Attributes Of Mobile Operating With Webview Ppt PowerPoint Presentation Inspiration Icon PDF
Persuade your audience using this important attributes of mobile operating with webview ppt powerpoint presentation inspiration icon pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application planning, application backup, authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Blockchain Technology Framework IT Overview Of Blockchain Technology Professional PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Deliver and pitch your topic in the best possible manner with this blockchain technology framework it overview of blockchain technology professional pdf. Use them to share invaluable insights on overview of blockchain technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
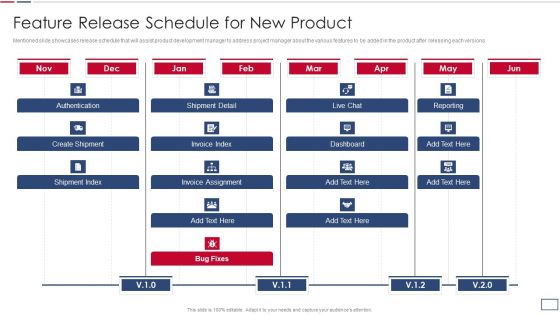
Software Developer Playbook Feature Release Schedule For New Product Slides PDF
Mentioned slide showcases release schedule that will assist product development manager to address project manager about the various features to be added in the product after releasing each versions. Deliver an awe inspiring pitch with this creative software developer playbook feature release schedule for new product slides pdf bundle. Topics like authentication, create shipment, shipment index, invoice assignment, dashboard, reporting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
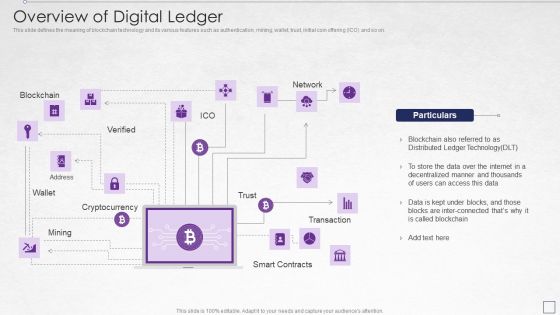
Digitized Record Book Technology Overview Of Digital Ledger Summary PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Deliver an awe inspiring pitch with this creative digitized record book technology overview of digital ledger summary pdf bundle. Topics like data, internet, technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
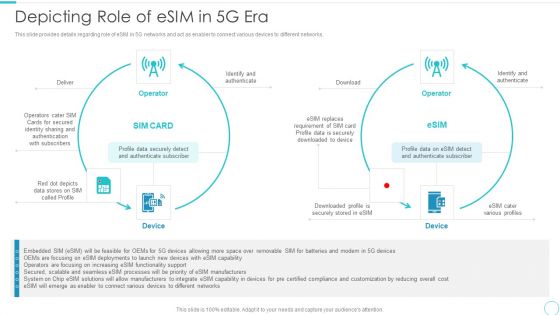
5G Evolution Architectural Technology Depicting Role Of Esim In 5G Era Graphics PDF
This slide provides details regarding role of eSIM in 5G networks and act as enabler to connect various devices to different networks. Deliver an awe inspiring pitch with this creative 5G Evolution Architectural Technology Depicting Role Of Esim In 5G Era Graphics PDF bundle. Topics like Authentication, Customization By Reducing, Certified Compliance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Feature Release Schedule For New Product Topics PDF
Mentioned slide showcases release schedule that will assist product development manager to address project manager about the various features to be added in the product after releasing each versions.Deliver an awe inspiring pitch with this creative Feature Release Schedule For New Product Topics PDF bundle. Topics like Authentication, Create Shipment, Invoice Assignment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
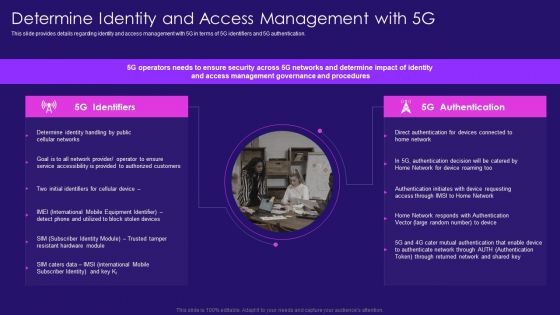
Determine Identity And Access Management With 5G Information PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. Deliver an awe inspiring pitch with this creative Determine Identity And Access Management With 5G Information PDF bundle. Topics like Determine Identity, Accessibility Provided, Identifiers Cellular can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cryptocurrency Ledger Overview Of Blockchain Technology Rules PDF
This slide defines the meaning of blockchain technology and its various features such as authentication, mining, wallet, trust, initial coin offering ICO and so on. Deliver and pitch your topic in the best possible manner with this Cryptocurrency Ledger Overview Of Blockchain Technology Rules PDF. Use them to share invaluable insights on Cryptocurrency, Technology, Network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
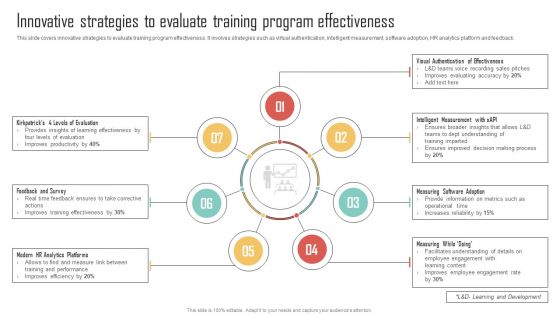
Innovative Strategies To Evaluate Training Enhancing Organization Productivity By Implementing Diagrams PDF
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. There are so many reasons you need a Innovative Strategies To Evaluate Training Enhancing Organization Productivity By Implementing Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Innovative Strategies To Evaluate Strategic Measures To Boost Employee Efficienc Background Pdf
This slide covers innovative strategies to evaluate training program effectiveness. It involves strategies such as virtual authentication, intelligent measurement, software adoption, HR analytics platform and feedback. There are so many reasons you need a Innovative Strategies To Evaluate Strategic Measures To Boost Employee Efficienc Background Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
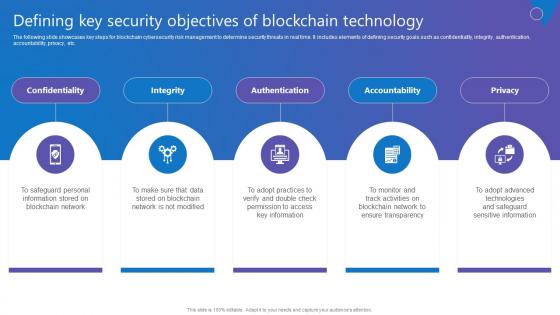
Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf
The following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Want to ace your presentation in front of a live audience Our Defining Key Security Objectives Comprehensive Guide To Blockchain Digital Security Rules Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example
This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Principles Of Security Testing Harnessing The World Of Ethical Ppt Example that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
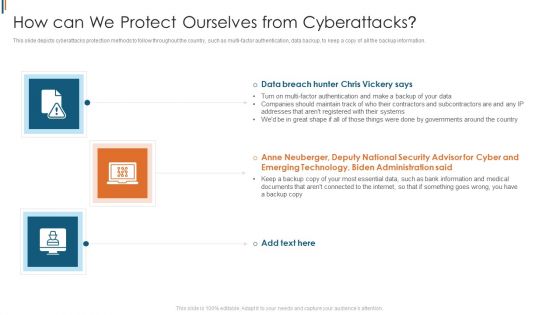
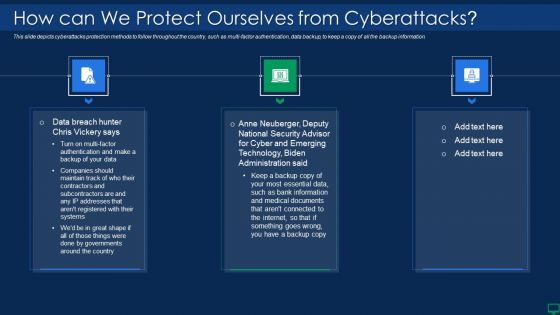
Ukraine Cyberwarfare How Can We Protect Ourselves From Cyberattacks Designs Pdf
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Presenting ukraine cyberwarfare how can we protect ourselves from cyberattacks designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like anne neuberger, deputy national security advisor for cyber and emerging technology, biden administration said. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
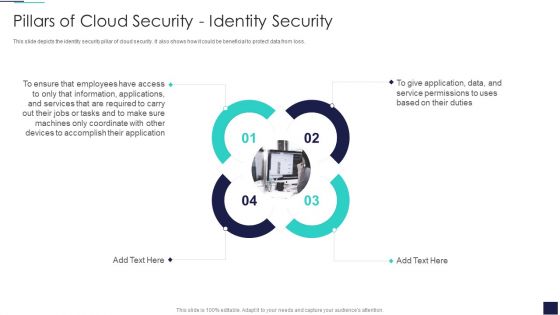
Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF
This slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss. This is a Cloud Information Security Pillars Of Cloud Security Identity Security Ppt Layouts Graphics Example PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advanced Authentication, Cloud Access, Eliminate Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Awareness Training Program Plan Ppt Show Tips PDF
This slide covers cybersecurity awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public wi-fi, phishing attacks, mobile device security and passwords and authentication. Showcasing this set of slides titled IT Security Awareness Training Program Plan Ppt Show Tips PDF. The topics addressed in these templates are Training Topic, Mode Of Training, Training Hours. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Main Features For Robust Application Security Testing Ppt Powerpoint Icons
This slide outlines the key characteristics of application security which include authentication, authorization, encryption, logging, etc. Are you searching for a Main Features For Robust Application Security Testing Ppt Powerpoint Icons that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Main Features For Robust Application Security Testing Ppt Powerpoint Icons from Slidegeeks today.
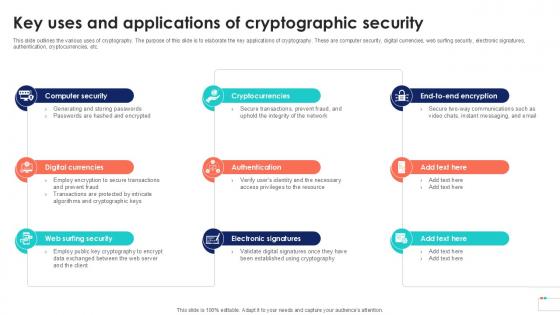
Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Structural Design Of Cloud Cryptography Cloud Data Security Using Cryptography Themes Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
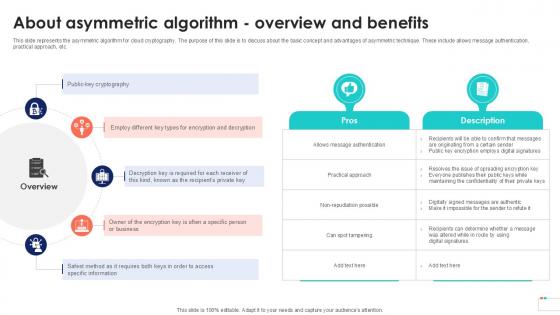
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample
The purpose of this slide is to illustrate the design of cryptography cloud framework. The main components included are cloud service communication, business cloud, identity authentication, consumer terminal, administrator, management platform, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Structural Design Of Cloud Cryptography Data Security In Cloud Computing Ppt Sample will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Russian Cyber Attacks On Ukraine IT How Can We Protect Ourselves Rules PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. This is a russian cyber attacks on ukraine it how can we protect ourselves rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internet, documents, information, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
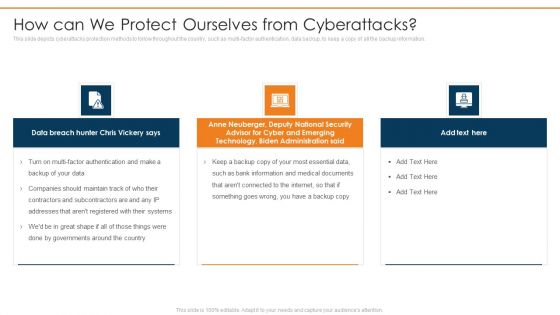
Data Wiper Spyware Attack How Can We Protect Ourselves From Cyberattacks Infographics PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information.This is a data wiper spyware attack how can we protect ourselves from cyberattacks infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like anne neuberger, advisor for cyber and emerging, technology, biden administration You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
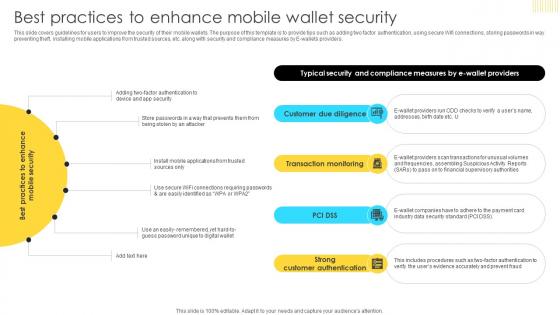
Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V
This slide covers guidelines for users to improve the security of their mobile wallets. The purpose of this template is to provide tips such as adding two factor authentication, using secure Wifi connections, storing passwords in way preventing theft, installing mobile applications from trusted sources, etc. along with security and compliance measures by E-wallets providers. There are so many reasons you need a Mastering Blockchain Wallets Best Practices To Enhance Mobile Wallet Security BCT SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
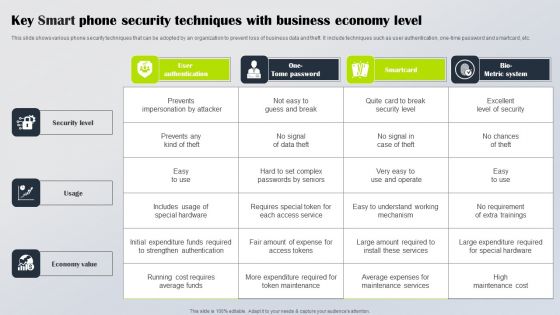
Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
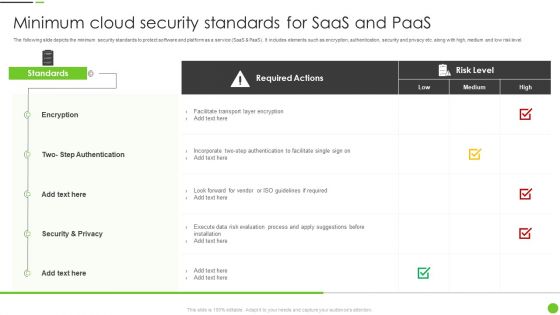
Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF
The following slide depicts the minimum security standards to protect software and platform as a service SaaS and PaaS. It includes elements such as encryption, authentication, security and privacy etc. along with high, medium and low risk level. Pitch your topic with ease and precision using this Minimum Cloud Security Standards For Saas And Paas Ppt PowerPoint Presentation Gallery Skills PDF. This layout presents information on Required Actions, Encryption, Security And Privacy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF
This slide shows framework which can be used by organizations to develop cloud security for data protection. It includes authentication, access control, user behavior analytics, logging an reporting, etc. Persuade your audience using this Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF. This PPT design covers Eight stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Framework, To Ensure Data Safety . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Securing Data Over Google Cloud Google Cloud Computing System Professional PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock.Presenting Securing Data Over Google Cloud Google Cloud Computing System Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Management, Protect Information, Compute Engine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phishing Attacks Awareness Training Program Plan Inspiration PDF
This slide covers phishing awareness training program plan to enhance effectiveness. It involves training topics such as cloud security, public Wi-Fi, removable media, mobile device security and passwords and authentication. Persuade your audience using this Phishing Attacks Awareness Training Program Plan Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Security, Mobile Device Security, Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home