Authentication
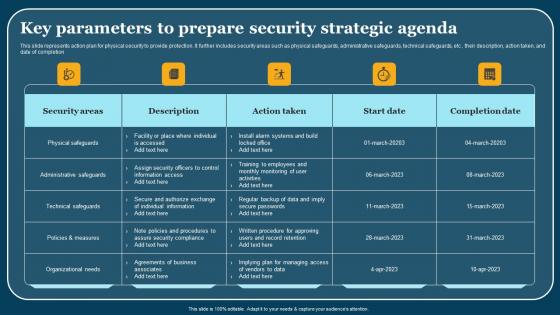
Key Parameters To Prepare Security Strategic Agenda Summary Pdf
This slide represents action plan for physical security to provide protection. It further includes security areas such as physical safeguards, administrative safeguards, technical safeguards, etc , their description, action taken, and date of completion. Pitch your topic with ease and precision using this Key Parameters To Prepare Security Strategic Agenda Summary Pdf. This layout presents information on Security Areas, Description, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Stock Photo Business Strategy Examples Protect Brain With Umbrella Stock Photo Best Photos
Bring A Cheer To Their Faces With Our stock photo business strategy examples protect brain with umbrella stock photo best photos. They Will Definitely Force A Smile. Our Environment Are An Enchanting Force. They Have An Array Of Attractive Assets.

Stock Photo Innovative Marketing Concepts Protect American Currency Stock Photo Photos
Create Foolproof Conditions With Our stock photo innovative marketing concepts protect american currency stock photo photos. Your Address Will Be Flawless. Make It Foolproof With Our Americana. They Cater For Any And Every Contingency.
Life Insurance Protection Symbol Vector Icon Ppt PowerPoint Presentation Gallery Visuals PDF
Persuade your audience using this life insurance protection symbol vector icon ppt powerpoint presentation gallery visuals pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including life insurance protection symbol vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Protection Shield On Document Vector Icon Ppt PowerPoint Presentation Icon Layouts PDF
Persuade your audience using this protection shield on document vector icon ppt powerpoint presentation icon layouts pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including protection shield on document vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Vector Showing Protection Shield With Web Browser Icon Ppt PowerPoint Presentation File Brochure PDF
Persuade your audience using this vector showing protection shield with web browser icon ppt powerpoint presentation file brochure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector showing protection shield with web browser icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Person Protecting Data By Using Network Access Control Ppt PowerPoint Presentation Gallery Infographics PDF
Persuade your audience using this person protecting data by using network access control ppt powerpoint presentation gallery infographics pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including person protecting data by using network access control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
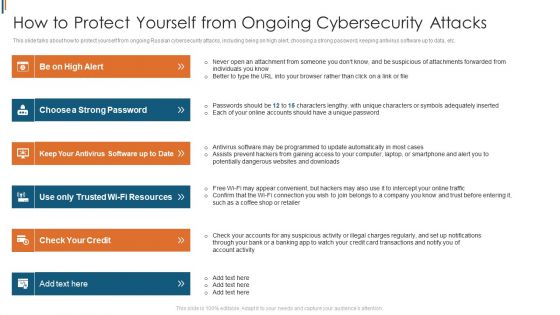
Ukraine Cyberwarfare How To Protect Yourself From Ongoing Cybersecurity Attacks Themes Pdf
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. This is a ukraine cyberwarfare how to protect yourself from ongoing cybersecurity attacks themes pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like choose a strong password, keep your antivirus software up to date, use only trusted wi fi resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack How To Protect Yourself From Ongoing Cybersecurity Attacks Download PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc.Presenting data wiper spyware attack how to protect yourself from ongoing cybersecurity attacks download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like choose a strong password, keep your antivirus, software up to date In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Path To Success For Cyber Security Risk Management Rules Pdf
The following slide provides a cyber risk management framework to help an organisation monitor and eliminate risk effectively. Key steps are identify, protect, detect, respond and recover. Pitch your topic with ease and precision using this Path To Success For Cyber Security Risk Management Rules Pdf. This layout presents information on Identity, Protect, Respond, Recover. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Dollar Under Umbrella Business Protection PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Dollar Under Umbrella Business Protection PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Finance PowerPoint Templates because Our PowerPoint Templates and Slides ensures Effective communication. They help you put across your views with precision and clarity. Present our Future PowerPoint Templates because You can safely bank on our PowerPoint Templates and Slides. They will provide a growth factor to your valuable thoughts. Download and present our Umbrellas PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink. Present our Money PowerPoint Templates because You can Raise a toast with our PowerPoint Templates and Slides. Spread good cheer amongst your audience.Use these PowerPoint slides for presentations relating to Dollar symbol under a umbrella, money, finance, security, future, umbrellas. The prominent colors used in the PowerPoint template are Green, Red, Black.

Piggy Bank Protect Money Finance PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Piggy Bank Protect Money Finance PowerPoint Templates PPT Backgrounds For Slides 0413.Download and present our Umbrellas PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Download our Money PowerPoint Templates because You aspire to touch the sky with glory. Let our PowerPoint Templates and Slides provide the fuel for your ascent. Present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download and present our Security PowerPoint Templates because It can Bubble and burst with your ideas. Download and present our Future PowerPoint Templates because Watching this your Audience will Grab their eyeballs, they wont even blink.Use these PowerPoint slides for presentations relating to Piggy with umbrella, security, money, finance, future, umbrellas. The prominent colors used in the PowerPoint template are Blue, Yellow, Black.
Case Study Intellectual Property Protection With Zero Trust Model Icons PDF
This slide represents the case study for implementing the ZTNA security model into a food and beverage organization to secure intellectual property, supply chain and manufacturing. The purpose of this slide is to highlight the key requirements, solutions and impact of ZTNA implementation on the business. Slidegeeks is here to make your presentations a breeze with Case Study Intellectual Property Protection With Zero Trust Model Icons PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Protection Of Currency Risks PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Protection Of Currency Risks PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Use our Success PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download and present our Finance PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Download our Money PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Use our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views.Use these PowerPoint slides for presentations relating to US Dollar symbol covered by a Protecting Umbrella, finance, money, security, success, umbrellas. The prominent colors used in the PowerPoint template are Blue, Red, Black.

Protect Your Savings Fom Market PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Protect Your Savings Fom Market PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Finance PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners. Download and present our Umbrellas PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let your ideas bloom. Create a bed of roses for your audience. Download and present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan.Use these PowerPoint slides for presentations relating to Financial piggy bank with umbrella protect, money, finance, umbrellas, security, services. The prominent colors used in the PowerPoint template are Red, Yellow, Blue.
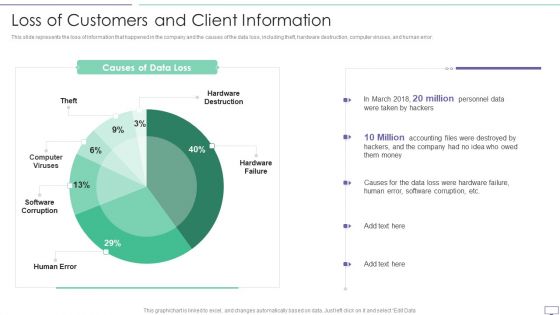
IT Security Hacker Loss Of Customers And Client Information Pictures PDF
This slide represents the loss of information that happened in the company and the causes of the data loss, including theft, hardware destruction, computer viruses, and human error.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Loss Due To Different Cyber Attacks Rules PDF. Use them to share invaluable insights on Hardware Destruction, Computer Viruses, Software Corruption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Protection Of Environment Is Very Important PowerPoint Templates Ppt Backgrounds For Slides 0513
When in doubt use our Protection Of Environment Is Very Important PowerPoint Templates PPT Backgrounds For Slides. The way ahead will become crystal clear. With our Umbrellas PowerPoint Templates you will be doubly sure. They possess that stamp of authority. Our Globe PowerPoint Templates do it in double quick time. Speed up the process in a tangible way.

Security Methodology Diagram Powerpoint Topics
This is a security methodology diagram powerpoint topics. This is a six stage process. The stages in this process are device protection, data separation, security operation, security organization, leak protection, sharing protection.

Protect Your Saving Business And Investment PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Protect Your Saving Business And Investment PowerPoint Templates PPT Backgrounds For Slides 0413.Download our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides are focused like a searchlight beam. They highlight your ideas for your target audience. Use our Success PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download our Business PowerPoint Templates because You should Bet on your luck with our PowerPoint Templates and Slides. Be assured that you will hit the jackpot. Use our Security PowerPoint Templates because You should Press the right buttons with our PowerPoint Templates and Slides. They will take your ideas down the perfect channel. Download and present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will let your ideas bloom. Create a bed of roses for your audience.Use these PowerPoint slides for presentations relating to Umbrella covering a piggy bank, security, success, business, umbrellas, money. The prominent colors used in the PowerPoint template are Yellow, Black, White.
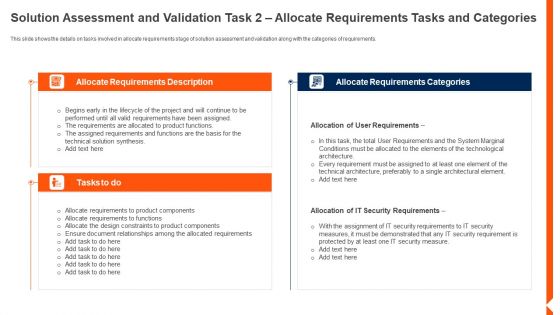
Solution Monitoring Verification Solution Assessment And Validation Requirements Tasks Designs PDF
This slide shows the details on tasks involved in allocate requirements stage of solution assessment and validation along with the categories of requirements. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation requirements tasks designs pdf. Use them to share invaluable insights on requirements, functions, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
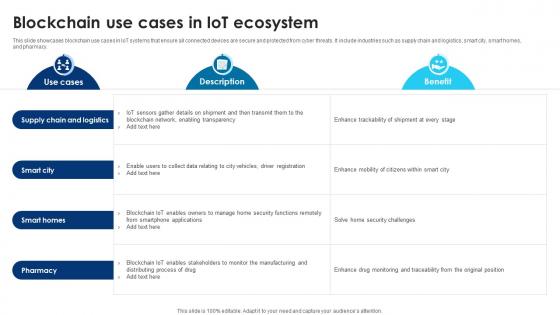
Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V
This slide showcases blockchain use cases in IoT systems that ensure all connected devices are secure and protected from cyber threats. It include industries such as supply chain and logistics, smart city, smart homes, and pharmacy. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Building Trust With IoT Security Blockchain Use Cases In IoT Ecosystem IoT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
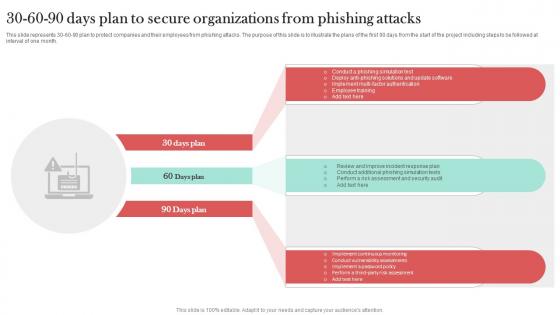
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Ensuring Organizational Safety Using AML Transaction Transaction Identity Verification Download PDF
This slide showcases transaction identity verification tool process flow. It provides details about verifiable credentials, binding physical to digital identities, secured by bank-grade level protocols, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Ensuring Organizational Safety Using AML Transaction Transaction Identity Verification Download PDF from Slidegeeks and deliver a wonderful presentation.

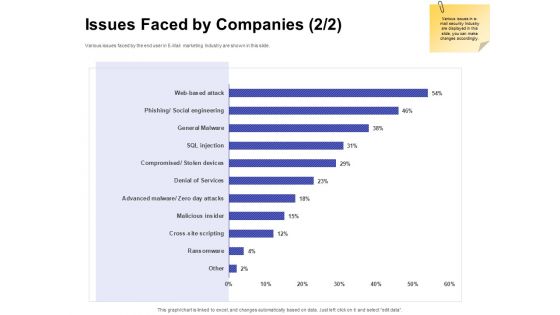
Email Security Market Research Report Issues Faced By Companies Professional PDF
Presenting this set of slides with name email security market research report issues faced by companies professional pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. This Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Security Enhancement Using Cloud Data Security Using Cryptography Elements Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Overview And Process Of Tokenization In Data Security PPT Example
This slide highlights the introduction and phases of tokenization in data security. The purpose of this slide is to showcase the overview and process such as various assets, verification of ownership, transfer to blockchain, etc. Find a pre-designed and impeccable Overview And Process Of Tokenization In Data Security PPT Example. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

IT Protection Network Protection Cyber Attack Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name it protection network protection cyber attack ppt powerpoint presentation complete deck. The topics discussed in these slides are network protection, cyber attack, database server security, laptop protected, cyber threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf
This slide highlights the various limitations of traditional firewall systems. The purpose of this slide is to outline the different issues of traditional firewalls. These include unable to prevent transfer of infected files, do not protect already compromised systems, etc. Create an editable Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Potential Threats Of Traditional Firewall Systems Security Network Security Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF
This slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. Find highly impressive Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

CASB 2 0 IT Cloud Access Security Broker Use Cases
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Presenting this PowerPoint presentation, titled CASB 2 0 IT Cloud Access Security Broker Use Cases, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CASB 2 0 IT Cloud Access Security Broker Use Cases. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CASB 2 0 IT Cloud Access Security Broker Use Cases that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Improving Security By Green Computing Technology Eco Friendly Computing IT
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks.Are you searching for a Improving Security By Green Computing Technology Eco Friendly Computing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Improving Security By Green Computing Technology Eco Friendly Computing IT from Slidegeeks today.
Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Benefits Of Confidential Computing For Secure Computing Framework Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Website Security Management Strategic Plan Step By Step Guide Slides PDF
Following slide outlines website security action plan to assure safety from external threats and cyber crimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Website Security Management Strategic Plan Step By Step Guide Slides PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Website Security Management Strategic Plan Step By Step Guide Slides PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide
This slide discusses the best security practices for infrastructure as code. The purpose of this slide is to highlight the best practices such as enforcing the passwords, installing the firewall, checking for updates, using content fillers, etc. Find highly impressive Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Best Practices For Infrastructure IAC Tools For Performance Analysis PPT Slide for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
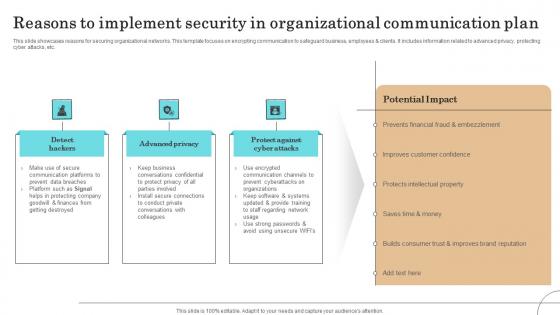
Reasons To Implement Security In Organizational Communication Plan Sample Pdf
This slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Showcasing this set of slides titled Reasons To Implement Security In Organizational Communication Plan Sample Pdf The topics addressed in these templates are Communication Platforms, Protecting Company, Improves Customer Confidence All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V
This slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Slidegeeks is here to make your presentations a breeze with Checklist To Ensure Security Everything About Bitcoin PPT PowerPoint Fin SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
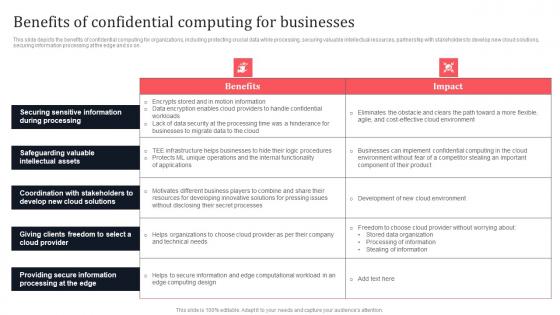
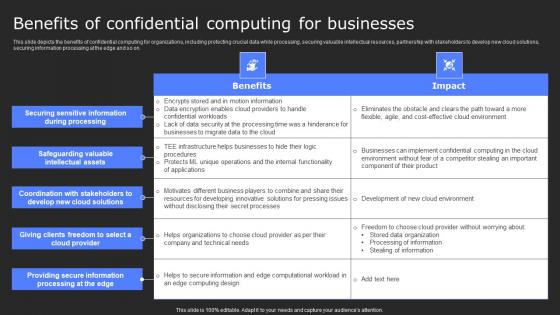
Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf
This slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Do you know about Slidesgeeks Benefits Of Confidential Computing For Businesses Secure Multi Party Ideas Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
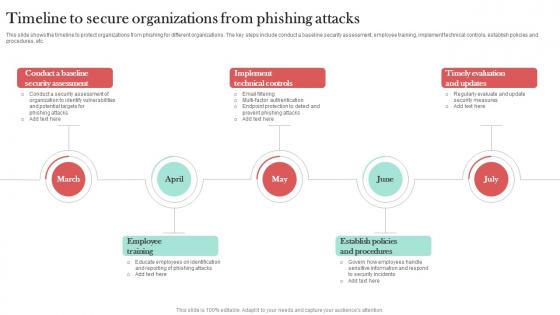
Timeline To Secure Organizations From Man In The Middle Phishing IT
This slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. This Timeline To Secure Organizations From Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Timeline To Secure Organizations From Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
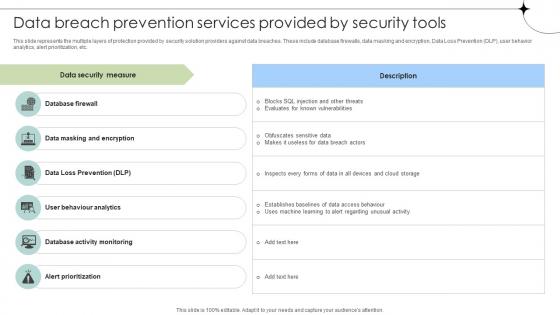
Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Data Breach Prevention Services Provided By Security Tools Data Fortification Strengthening Defenses and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
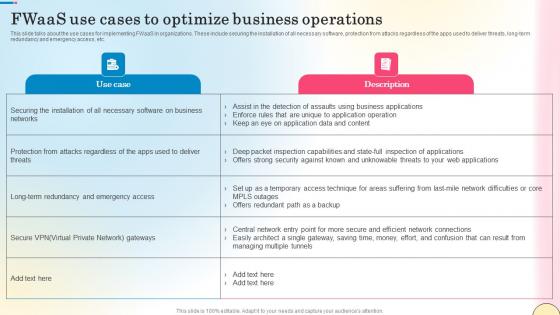
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
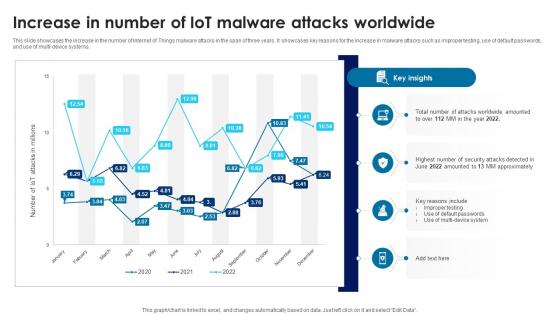
Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V
This slide showcases the increase in the number of Internet of Things malware attacks in the span of three years. It showcases key reasons for the increase in malware attacks such as improper testing, use of default passwords, and use of multi-device systems. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Building Trust With IoT Security Increase In Number Of IoT Malware Attacks Worldwide IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Zero Trust Network Security Access Architecture Overview Graphics Pdf
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Zero Trust Network Security Access Architecture Overview Graphics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
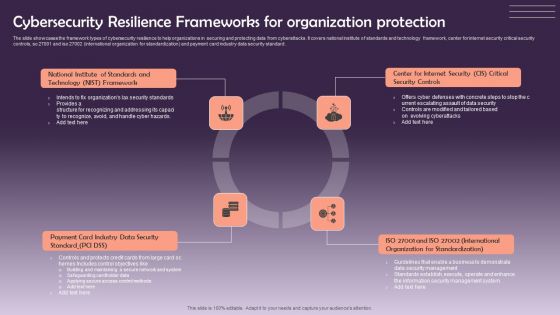
Cybersecurity Resilience Frameworks For Organization Protection Information PDF
The slide showcases the framework types of cybersecurity resilience to help organizations in securing and protecting data from cyberattacks. It covers national institute of standards and technology framework, center for internet security critical security controls, so 27001 and iso 27002 international organization for standardization and payment card industry data security standard. Presenting Cybersecurity Resilience Frameworks For Organization Protection Information PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Security, Organization For Standardization, Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the need or importance of workplace safety at organization which includes increased productivity, low compensation claims, reduced absenteeism, protected workplace and low fatalities. Retrieve professionally designed Need Of Workplace Safety Workplace Safety Protocol And Security Practices Template Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

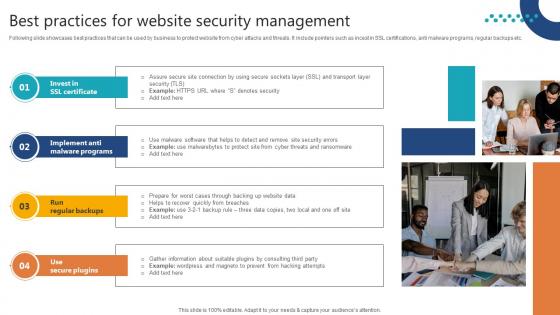
Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
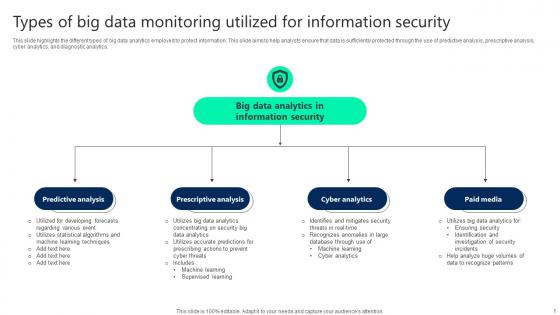
Types Of Big Data Monitoring Utilized For Information Security Elements pdf
This slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Pitch your topic with ease and precision using this Types Of Big Data Monitoring Utilized For Information Security Elements pdf. This layout presents information on Predictive Analysis, Prescriptive Analysis, Cyber Analytics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
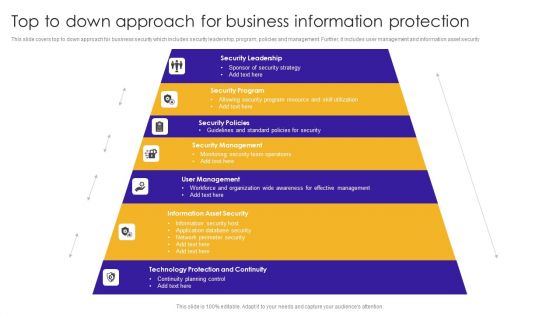
Top To Down Approach For Business Information Protection Demonstration PDF
This slide covers top to down approach for business security which includes security leadership, program, policies and management. Further, it includes user management and information asset security.Pitch your topic with ease and precision using this Top To Down Approach For Business Information Protection Demonstration PDF. This layout presents information on Security Leadership, Security Program, Security Policies. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
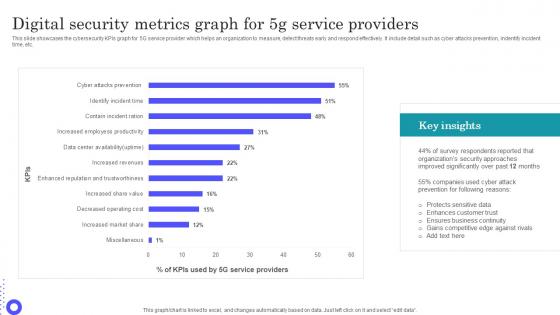
Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf
Showcasing this set of slides titled Digital Security Metrics Graph For 5g Service Providers Guidelines Pdf The topics addressed in these templates are Protects Sensitive, Enhances Customer, Ensures Business Continuity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Application Protection Testing Flow Chart Themes PDF
This slide covers business application security testing flow chart which includes secure application model, security standard recognition and privacy testing.Pitch your topic with ease and precision using this Business Information Application Protection Testing Flow Chart Themes PDF. This layout presents information on Security Consistency, Target Weighting, Target Recognition. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home