Application Security
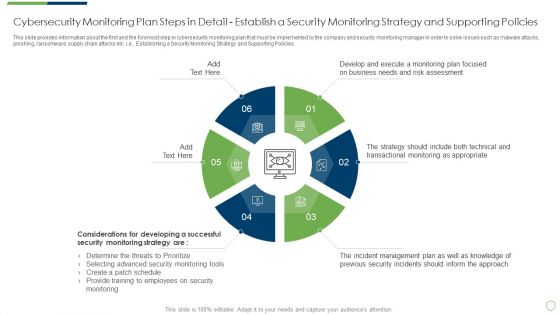
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Log Management Services Slide2 Structure PDF
This is a security information and event management strategies for financial audit and compliance log management services slide2 structure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like log management, configurations, metrics, databases, net working. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF
This slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider triolan during the russian invasion. This modern and well arranged Series Of Cyber Security AttaSeries Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
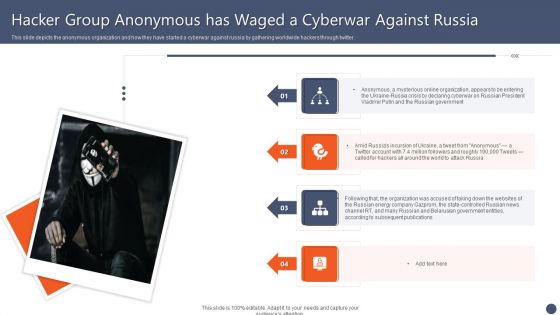
Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF
This slide depicts the anonymous organization and how they have started a cyberwar against russia by gathering worldwide hackers through twitter. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Strategies For Financial Audit And Compliance Hybrid Managed Siem Model Topics PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance hybrid managed siem model topics pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Need For SIEM Software Download PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting security information and event management strategies for financial audit and compliance need for siem software download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
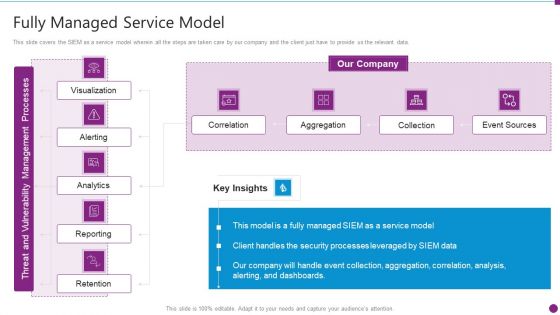
Security Information And Event Management Strategies For Financial Audit And Compliance Fully Managed Service Model Portrait PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance fully managed service model portrait pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Control Techniques For Real Estate Project Construction Site Control Measures For Working At Heights Designs PDF
This modern and well-arranged Security Control Techniques For Real Estate Project Construction Site Control Measures For Working At Heights Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
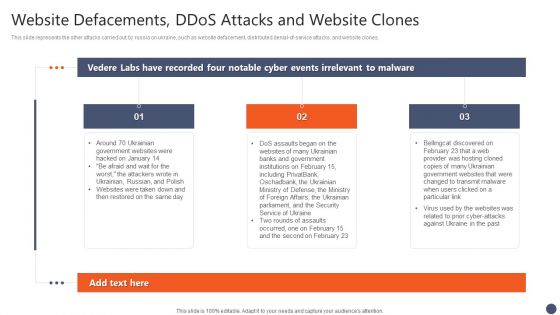
Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF
This slide represents the other attacks carried out by russia on ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. The Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Key Takeaways, Countries, Region and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Series Of Cyber Security Attacks Against Ukraine 2022 Reasons Behind Ukraine And Russia Cyber Warfare Structure PDF
This slide describes the reasons behind ukraine and russia cyber warfare, including natos eastward expansion, ukraine is not a real country according to putin, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Series Of Cyber Security Attacks Against Ukraine 2022 Reasons Behind Ukraine And Russia Cyber Warfare Structure PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
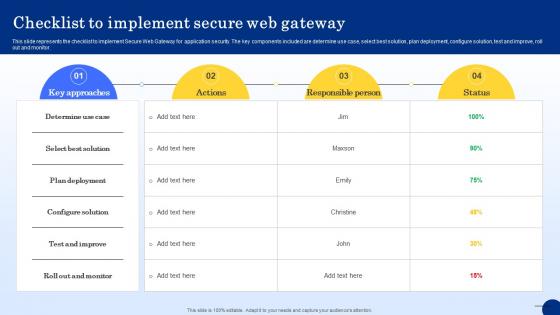
Checklist To Implement Secure Web Gateway Web Threat Protection System
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Get a simple yet stunning designed Checklist To Implement Secure Web Gateway Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Checklist To Implement Secure Web Gateway Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
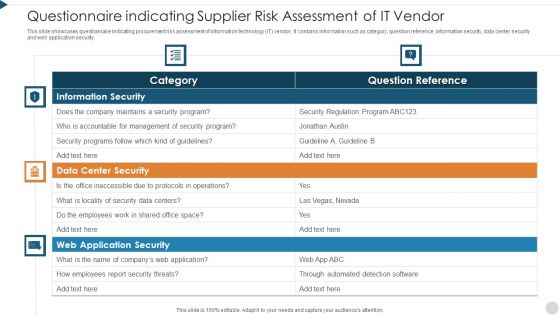
Questionnaire Indicating Supplier Risk Assessment Of It Vendor Themes PDF
This slide showcases questionnaire indicating procurement risk assessment of information technology IT vendor. It contains information such as category, question reference, information security, data center security and web application security. Pitch your topic with ease and precision using this questionnaire indicating supplier risk assessment of it vendor themes pdf. This layout presents information on information security, data center security, web application security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

AI Applications In Banking And Financial Services Formats PDF
This slide covers use of artificial intelligence in banking and financial services. It involves applications such as customer engagement, predictive analytics, cyber security and credit scoring.Presenting AI Applications In Banking And Financial Services Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Engagement, Predictive Analytics, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

AI Applications Use To Improve Business Operations Diagrams PDF
This slide signifies the artificial intelligence software used to increase organisation operations. It covers information about hiring, market prediction, customer analysis and cyber security Presenting AI Applications Use To Improve Business Operations Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Market Prediction, Customer Analysis, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Why Is A Reverse Proxy Important Reverse Proxy For Load Balancing Structure PDF
This slide explains why reverse proxy is essential and how it imposes web application security, application delivery firewalls, cloud bursting, and split application architecture. Deliver an awe inspiring pitch with this creative Why Is A Reverse Proxy Important Reverse Proxy For Load Balancing Structure PDF bundle. Topics like Internet, Reverse Proxy, Application Servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Affirmative Action Plan Applicant Tracking Ppt Example
This is a affirmative action plan applicant tracking ppt example. This is a five stage process. The stages in this process are affirmative action plan, union negotiation costing, availability analysis, workforce utilization, applicant tracking.
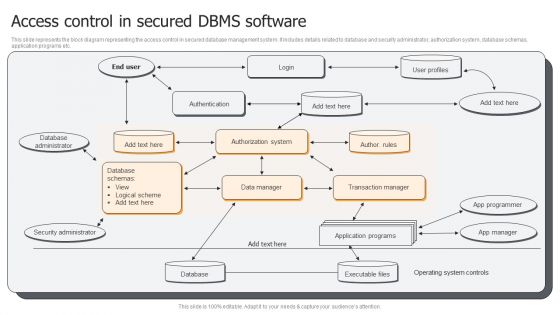
Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF
This slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Database Administrator, Security Administrator, Database, Application Programs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
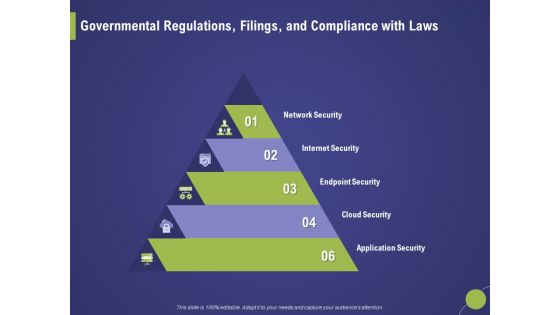
Firm Capability Assessment Governmental Regulations Filings And Compliance With Laws Ppt Outline Slides PDF
Presenting this set of slides with name firm capability assessment governmental regulations filings and compliance with laws ppt outline slides pdf. This is a six stage process. The stages in this process are network security, internet security, endpoint security, cloud security, application security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
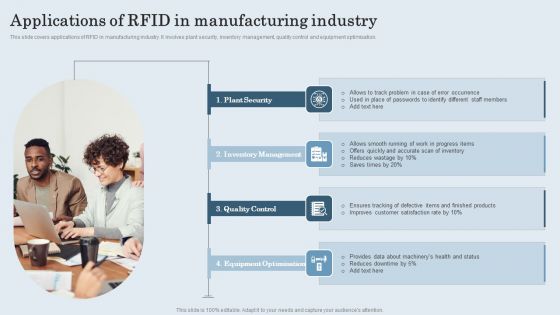
Applications Of RFID In Manufacturing Industry Summary PDF
This slide covers applications of RFID in manufacturing industry. It involves plant security, inventory management, quality control and equipment optimisation. Presenting Applications Of RFID In Manufacturing Industry Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Plant Security, Inventory Management, Quality Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mesh Computing Technology Hybrid Private Public Iaas Paas Saas Workplan Characteristics Of Software As A Service Saas Pictures PDF
Deliver an awe inspiring pitch with this creative mesh computing technology hybrid private public iaas paas saas workplan characteristics of software as a service saas pictures pdf bundle. Topics like high availability, elastic infrastructure, data security, application security, automated provisioning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
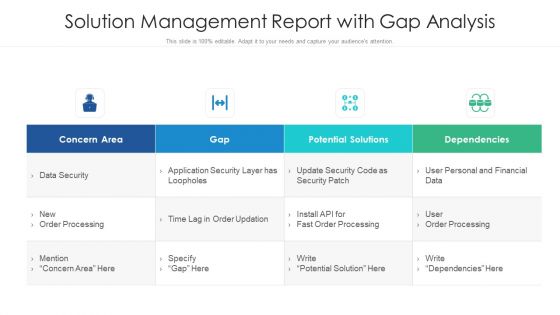
Solution Management Report With Gap Analysis Ppt PowerPoint Presentation Show Gallery PDF
Pitch your topic with ease and precision using this solution management report with gap analysis ppt powerpoint presentation show gallery pdf. This layout presents information on potential solutions, application security, fast order processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Comparative Analytics In Commercial Banking Template Ppt Slides
This is a comparative analytics in commercial banking template ppt slides. This is a three stage process. The stages in this process are application design and development, scalability security compliance, application design and development, application design and development.
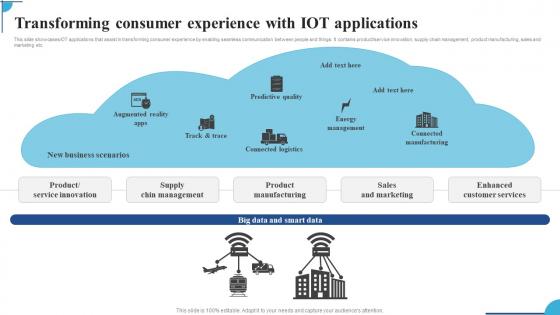
Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf
This slide showcases IOT applications that assist in transforming consumer experience by enabling seamless communication between people and things. It contains product service innovation,supply chain management,product manufacturing,sales and marketing etc. Showcasing this set of slides titled Transforming Consumer Experience With IOT Applications Ppt Slides Pictures Pdf. The topics addressed in these templates are Supply Chin Management,Product Manufacturing,Sales And Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color,background,font etc. as per your unique business setting.

It Infrastructure Template Example Of Ppt
This is a it infrastructure template example of ppt. This is a ten stage process. The stages in this process are data management, network management, monitoring and notification, application management, security management.
Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF
This slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Get a simple yet stunning designed Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Secure Access Service Edge Performance Tracking Dashboard Ppt Inspiration Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
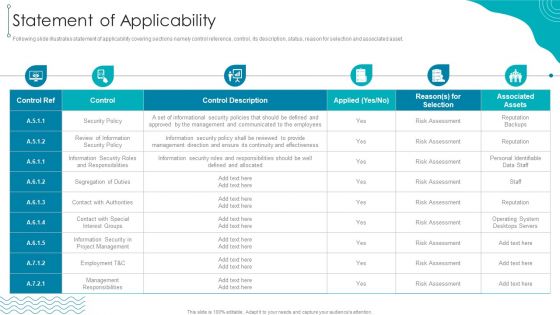
ISO 27001 Organizational Qualifying Procedure Statement Of Applicability Slides PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Statement Of Applicability Slides PDF bundle. Topics like Information Security, Segregation Of Duties, Management Responsibilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Management Services Infrastructure Optimization Ppt Ideas Topics PDF
Presenting construction management services infrastructure optimization ppt ideas topics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like services, applications, security, process, networks. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Web Access Control Solution Relationship Between Secure Access Service Edge And Secure Web Gateway
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Boost your pitch with our creative Web Access Control Solution Relationship Between Secure Access Service Edge And Secure Web Gateway. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
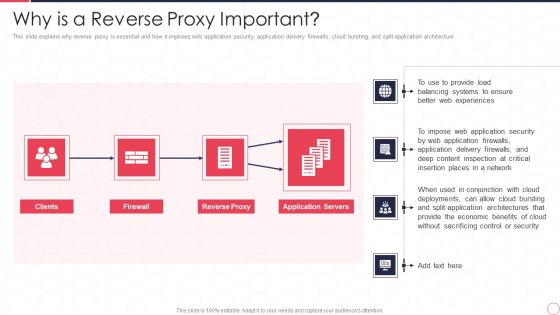
Reverse Proxy Server IT Why Is A Reverse Proxy Important Ppt Layouts Grid PDF
This slide explains why reverse proxy is essential and how it imposes web application security, application delivery firewalls, cloud bursting, and split application architecture. This is a reverse proxy server it why is a reverse proxy important ppt layouts grid pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reverse proxy, application servers, web experiences, insertion places. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
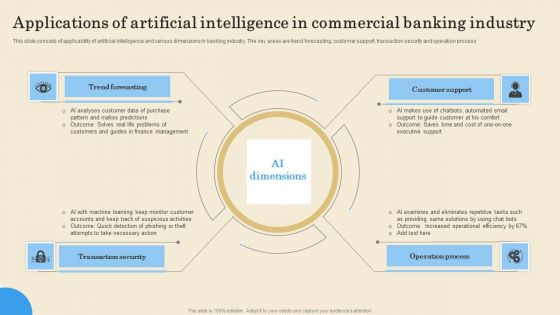
Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF
This slide consists of applicability of artificial intelligence and various dimensions in banking industry. The key areas are trend forecasting, customer support, transaction security and operation process. Persuade your audience using this Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Trend Forecasting, Transaction Security, Operation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
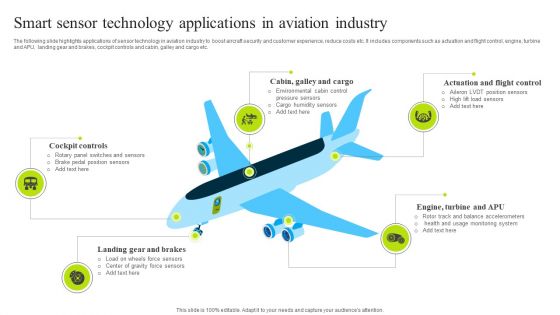
Smart Sensor Technology Applications In Aviation Industry Introduction PDF
The following slide highlights applications of sensor technology in aviation industry to boost aircraft security and customer experience, reduce costs etc. It includes components such as actuation and flight control, engine, turbine and APU, landing gear and brakes, cockpit controls and cabin, galley and cargo etc. Presenting Smart Sensor Technology Applications In Aviation Industry Introduction PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Cockpit Controls, Brakes, Industry. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Blockchain Technology Applications For Cyber Threat Prevention Icons PDF
This slides represents various application of blockchain technology in enhancing cyber safety which helps to speed up data transfer procedures, offer secure transactions, and lower compliance expenses. Key components are IoT security, secure private messaging, etc. Presenting Blockchain Technology Applications For Cyber Threat Prevention Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prevention, Infrastructure, System . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Reverse Proxy Web Server Why Is A Reverse Proxy Important Rules PDF
This slide explains why reverse proxy is essential and how it imposes web application security, application delivery firewalls, cloud bursting, and split application architecture. Present like a pro with Reverse Proxy Web Server Why Is A Reverse Proxy Important Rules PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Platform As A Service Model For Service Applications Ppt PowerPoint Presentation Icon Deck PDF
Showcasing this set of slides titled platform as a service model for service applications ppt powerpoint presentation icon deck pdf. The topics addressed in these templates are organizational security, social graphs, service applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

ISO 27001 Certification Procedure Statement Of Applicability Designs PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Statement Of Applicability Designs PDF. Use them to share invaluable insights on Information Security, Segregation Of Duties, Management Responsibilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
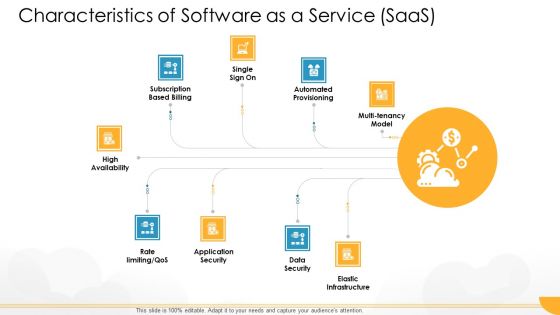
Technology Guide For Serverless Computing Characteristics Of Software As A Service Saas Background PDF
This is a technology guide for serverless computing characteristics of software as a service saas background pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like high availability, application security, data security, elastic infrastructure, multi tenancy model. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
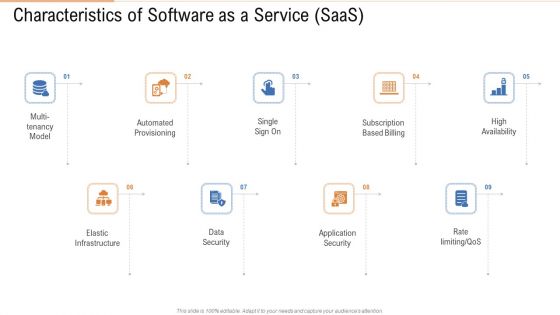
Characteristics Of Software As A Service Saas Ppt File Microsoft PDF
This is a characteristics of software as a service saas ppt file microsoft pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elastic infrastructure, data security, application security, rate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Applications Of Quantum Computing Ppt Professional Format PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. This is a Applications Of Quantum Computing Ppt Professional Format PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financial Modelling, Logistics Optimization, Applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Applications Of Quantum Computing Ppt Pictures Templates PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc. This is a Applications Of Quantum Computing Ppt Pictures Templates PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Financial Modelling, Weather Forecasting, Logistics Optimization, Computational Chemistry. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Quantum Key Distribution Applications Of Quantum Computing Background PDF
This slide represents Quantum computing applications in different sectors such as artificial intelligence and machine learning, drug design and development, cyber security, financial modeling, etc.This is a Quantum Key Distribution Applications Of Quantum Computing Background PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Artificial Intelligence, Design And Development, Cybersecurity And Cryptography You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Relationship Between Secure Access Service Edge Web Threat Protection System
This slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Presenting this PowerPoint presentation, titled Relationship Between Secure Access Service Edge Web Threat Protection System, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Relationship Between Secure Access Service Edge Web Threat Protection System. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Relationship Between Secure Access Service Edge Web Threat Protection System that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Open Source WAF Features Ppt Portfolio Influencers PDF
This slide represents the characteristics of an open-source Web Application Firewall. The purpose of this slide is to give an overview of the primary features of open-source WAF, including continuous passive security assessment, real-time application security monitoring, full HTTP traffic logging, and web application hardening. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Open Source WAF Features Ppt Portfolio Influencers PDF from Slidegeeks and deliver a wonderful presentation.

Secure Online Banking For Money Transfer Background PDF
Persuade your audience using this secure online banking for money transfer background pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including secure online banking for money transfer. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
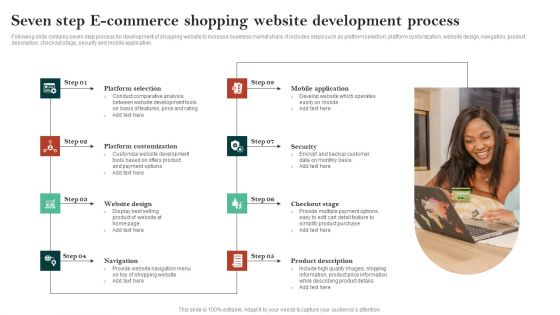
Seven Step E Commerce Shopping Website Development Process Guidelines PDF
Following slide contains seven step process for development of shopping website to increase business market share. It includes steps such as platform selection, platform customization, website design, navigation, product description, checkout stage, security and mobile application. Presenting Seven Step E Commerce Shopping Website Development Process Guidelines PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Platform Selection, Mobile Application, Security, Checkout Stage, Product Description. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
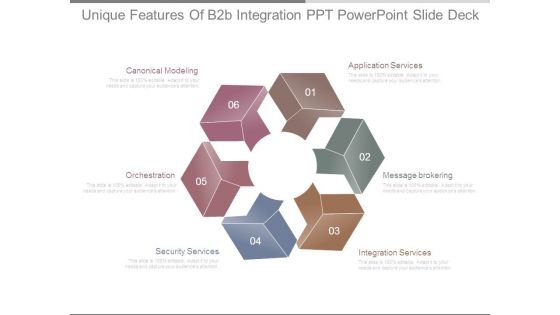
Unique Features Of B2b Integration Ppt Powerpoint Slide Deck
This is a unique features of b2b integration ppt powerpoint slide deck. This is a six stage process. The stages in this process are canonical modeling, application services, orchestration, security services, integration services, message brokering.

Table Of Contents For Web App Firewall Services IT Guidelines PDF
Presenting table of contents for web app firewall services it guidelines pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like services, application, security, deployment, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a Features Of WAF Protection Against The Owasp Vulnerabilities WAF Platform Summary PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Misconfigurations, Session Management, Security Project. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Cyber Threat Prevention Technology Market Topics PDF
This slide provides the statistical data for IT security software user market to help business and organizations enhance process efficiency. Major security technology are authentication, IoT, Zero trust, Cloud, application security, etc. Pitch your topic with ease and precision using this IT Cyber Threat Prevention Technology Market Topics PDF. This layout presents information on Key Insights, Progressive Rate, Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Regression Testing Applications And Use Cases Corrective Regression Testing Ppt Sample
This slide discusses the applications and use cases of regression testing. The purpose of this slide is to showcase the use cases and applications such as new releases, integration testing, security patches, and so on. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Regression Testing Applications And Use Cases Corrective Regression Testing Ppt Sample and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
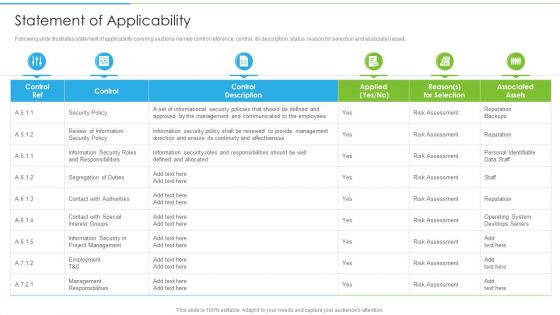
Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF
Following slide illustrates statement of applicability covering sections namely control reference, control, its description, status, reason for selection and associated asset. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Statement Of Applicability Demonstration PDF. Use them to share invaluable insights on Security Policy, Contact Authorities, Project Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Web App Firewall Services IT Features Of WAF Protection Against The OWASP Vulnerabilities Graphics PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This is a web app firewall services it features of waf protection against the owasp vulnerabilities graphics pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, data exposure, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity ML Business Applications Sample Pdf
This slide contains machine learning in cyber security to identify cyber threats, improve available antivirus software and prevent similar attacks. These include email monitoring, machine leaning against bots, and detecting malicious entities. Pitch your topic with ease and precision using this Cybersecurity ML Business Applications Sample Pdf. This layout presents information on Email Monitoring, Machine Leaning, Detecting Malicious Entities. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
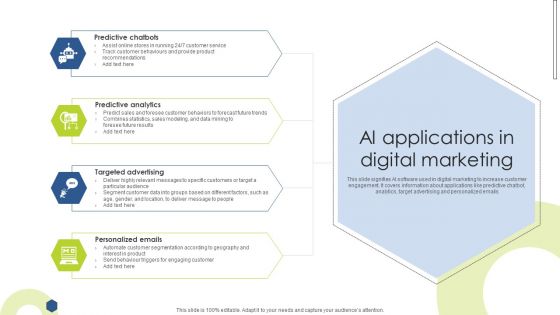
AI Applications In Digital Marketing Inspiration PDF
This slide signifies the smart manufacturing key threats and solutions to overcome. It covers information about challenges like safety in human robot collaboration, security issue and skill development with strategies implemented to overcome them Persuade your audience using this AI Applications In Digital Marketing Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Predictive Chatbots, Predictive Analytics, Targeted Advertising. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Introduction To Next Generation Secure Web Gateway Web Threat Protection System
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. This modern and well-arranged Introduction To Next Generation Secure Web Gateway Web Threat Protection System provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

 Home
Home