Application Architecture

Cloud Based Internet Of Things Waste Management Architecture Ideas Pdf
The below slide explains the cloud based IoT waste management infrastructure that helps to collect and analyze the data on different waste. The different steps involved are GPS data collection, waste management application, cloud internet, etc. Showcasing this set of slides titled Cloud Based Internet Of Things Waste Management Architecture Ideas Pdf. The topics addressed in these templates are GPS Data Collection, Waste Management Application, Cloud Internet. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Frameworks For Implementing Enterprise Architecture Plan Designs Pdf
This slide mentions the common frameworks accepted industry wide to implement enterprise architecture strategy. It includes Zachman Framework, Open Group Architecture Framework and Generalized Enterprise Reference Architecture and Methodology. Showcasing this set of slides titled Frameworks For Implementing Enterprise Architecture Plan Designs Pdf. The topics addressed in these templates are Zachman Framework, Generalized Enterprise, Methodology Designing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
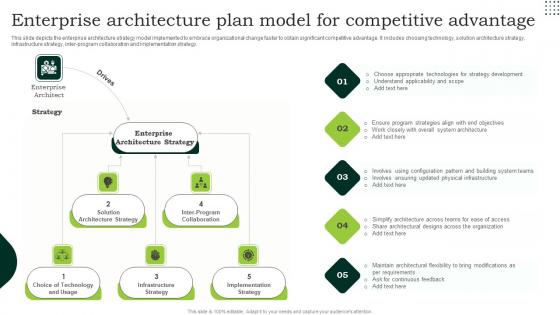
Enterprise Architecture Plan Model For Competitive Advantage Microsoft Pdf
This slide depicts the enterprise architecture strategy model implemented to embrace organizational change faster to obtain significant competitive advantage. It includes choosing technology, solution architecture strategy, infrastructure strategy, inter program collaboration and implementation strategy. Showcasing this set of slides titled Enterprise Architecture Plan Model For Competitive Advantage Microsoft Pdf. The topics addressed in these templates are Enterprise Architecture Strategy, Solution Architecture Strategy, Inter Program Collaboration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
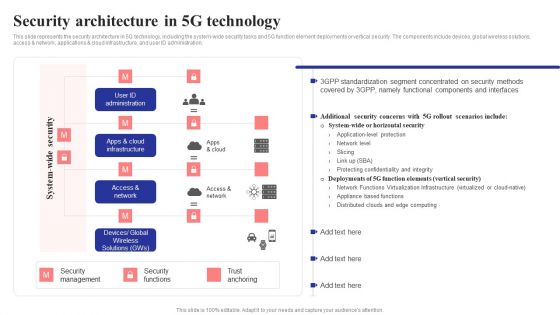
Security Architecture In 5G Technology 5G Network Structure Background PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access network, applications cloud infrastructure, and user ID administration.Are you searching for a Security Architecture In 5G Technology 5G Network Structure Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Architecture In 5G Technology 5G Network Structure Background PDF from Slidegeeks today.
Systems Integration Architecture In Powerpoint And Google Slides Cpb
Introducing our well designed Systems Integration Architecture In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Systems Integration Architecture. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
B2b Integration Concepts And Architecture Ppt Powerpoint Shapes
This is a b2b integration concepts and architecture ppt powerpoint shapes. This is a four stage process. The stages in this process are b2b integration, private process, backend application, partner.

SAP Cloud Based Business Intelligence Platform Connectivity Architecture Inspiration PDF
This slide highlights the SAP analytics cloud overview that combines business intelligence, predictive analysis, planning, and digital boardroom capabilities to analyze all data from different platforms. It includes applications SAP digital boardroom, SAP analytics Hub, etc. Showcasing this set of slides titled SAP Cloud Based Business Intelligence Platform Connectivity Architecture Inspiration PDF. The topics addressed in these templates are SAP Digital Boardroom, SAP Analytics Hub, Mobile Experience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Enterprise Resource Planning Software System Architecture Icon Microsoft Pdf
Pitch your topic with ease and precision using this Enterprise Resource Planning Software System Architecture Icon Microsoft Pdf. This layout presents information on Enterprise Resource, Planning Software, System Architecture Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Computing Services Architecture Of Cloud Computing Slides PDF
This slide shows cloud computing architecture, including client infrastructure that falls under the front end and back end elements such as application, service, runtime cloud, management, storage, etc. Deliver and pitch your topic in the best possible manner with this Cloud Computing Services Architecture Of Cloud Computing Slides PDF. Use them to share invaluable insights on Client Infrastructure, Front End, Application, Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
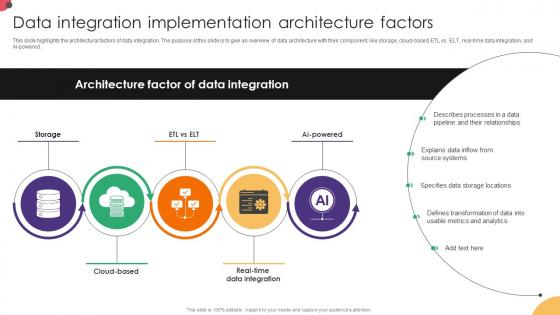
Data Integration Implementation Architecture Factors Data Integration Strategies For Business
This slide highlights the architectural factors of data integration. The purpose of this slide is to give an overview of data architecture with their component, like storage, cloud-based, ETL vs. ELT, real-time data integration, and AI-powered. Find highly impressive Data Integration Implementation Architecture Factors Data Integration Strategies For Business on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Integration Implementation Architecture Factors Data Integration Strategies For Business for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Application Lifecycle Management Ppt Powerpoint Show
This is a application lifecycle management ppt powerpoint show. This is a eight stage process. The stages in this process are inspiration, business case, requirements, design and architecture, development, test, operations, idea conception, development.
Enterprise Data Architecture Plan Elements Icon Pictures Pdf
Showcasing this set of slides titled Enterprise Data Architecture Plan Elements Icon Pictures Pdf. The topics addressed in these templates are Enterprise Data Architecture, Plan Elements Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
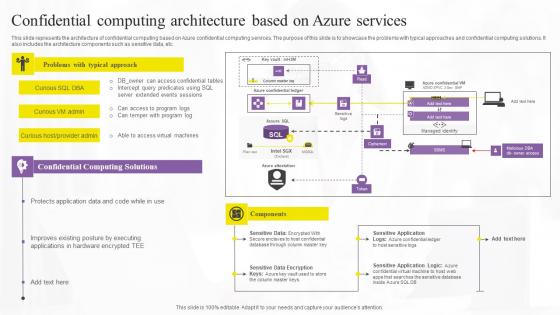
Confidential Computing Architecture Based Confidential Computing Technologies Information Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based Confidential Computing Technologies Information Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based Confidential Computing Technologies Information Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Enterprise Data Architecture Ppt PowerPoint Presentation Summary Templates Cpb
This is a enterprise data architecture ppt powerpoint presentation summary templates cpb. This is a three stage process. The stages in this process are enterprise data architecture.

Enterprise It Architecture Ppt PowerPoint Presentation Infographics Slide Cpb
This is a enterprise it architecture ppt powerpoint presentation infographics slide cpb. This is a three stage process. The stages in this process are enterprise it architecture.

Erp System Architecture Ppt PowerPoint Presentation Infographics Ideas
This is a erp system architecture ppt powerpoint presentation infographics ideas. This is a four stage process. The stages in this process are use, adaptation, applications, data storage.
Architecture Verification In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Architecture Verification In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Architecture Verification that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Architecture Examples In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Architecture Examples In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Architecture Examples that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
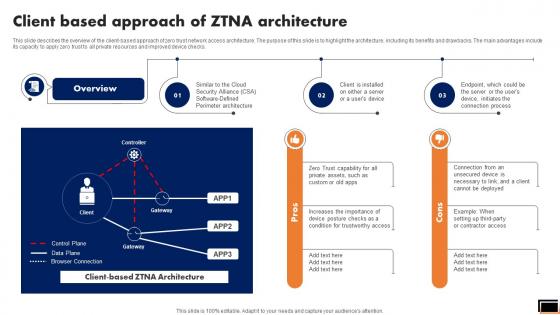
Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Get a simple yet stunning designed Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Client Based Approach Of Ztna Architecture Software Defined Perimeter SDP can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Zero Trust Model Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Other ZTNA Architecture Deployment Approaches to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Other ZTNA Architecture Deployment Approaches.
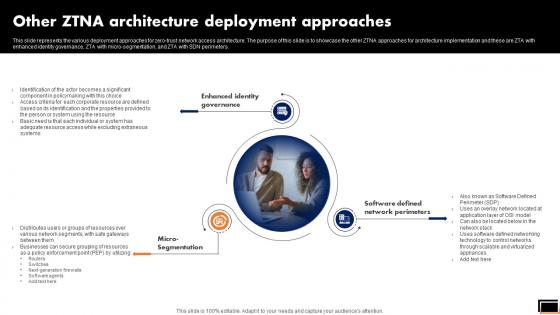
Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf
This slide represents the architecture of confidential computing based on azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Confidential Computing Architecture Based On Secure Computing Framework Elements Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Engineer Software Architecture In Powerpoint And Google Slides Cpb
Introducing our well-designed Engineer Software Architecture In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Engineer Software Architecture. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Cloud Distribution Service Models Architecture Of Cloud Computing Clipart PDF
This slide shows cloud computing architecture, including client infrastructure that falls under the front end and back end elements such as application, service, runtime cloud, management, storage, etc. Presenting Cloud Distribution Service Models Architecture Of Cloud Computing Clipart PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Application, Service, Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
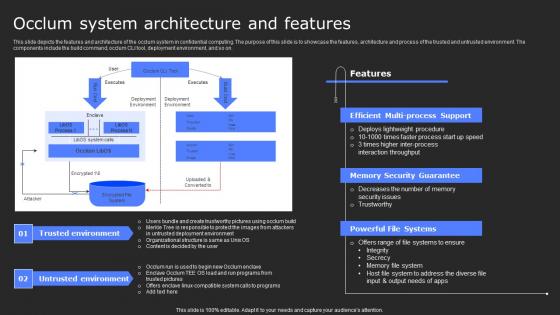
Occlum System Architecture And Features Secure Computing Framework Clipart Pdf
This slide depicts the features and architecture of the occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, occlum CLI tool, deployment environment, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Occlum System Architecture And Features Secure Computing Framework Clipart Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Occlum System Architecture And Features Secure Computing Framework Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
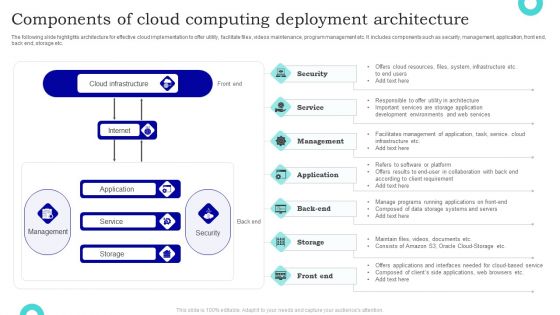
Components Of Cloud Computing Deployment Architecture Sample PDF
The following slide highlights architecture for effective cloud implementation to offer utility, facilitate files, videos maintenance, program management etc. It includes components such as security, management, application, front end, back end, storage etc. Pitch your topic with ease and precision using this Components Of Cloud Computing Deployment Architecture Sample PDF. This layout presents information on Cloud Infrastructure, Application, Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Based Service Models Architecture Of Cloud Computing Themes PDF
This slide shows cloud computing architecture, including client infrastructure that falls under the front end and back end elements such as application, service, runtime cloud, management, storage, etc.Deliver and pitch your topic in the best possible manner with this Cloud Based Service Models Architecture Of Cloud Computing Themes PDF. Use them to share invaluable insights on Client Infrastructure, Clients Communicate, Programs Cloud and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
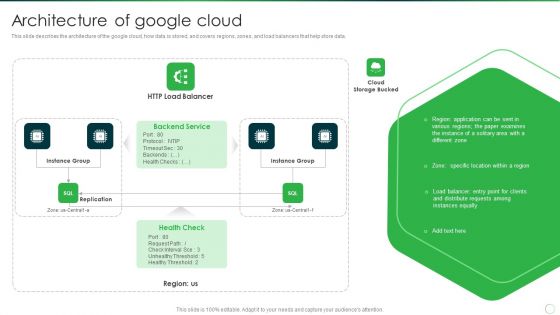
Google Cloud Computing System Architecture Of Google Cloud Elements PDF
This slide describes the architecture of the google cloud, how data is stored, and covers regions, zones, and load balancers that help store data. Deliver an awe inspiring pitch with this creative Google Cloud Computing System Architecture Of Google Cloud Elements PDF bundle. Topics like Backend Service, Application, Cloud Storage Bucked can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
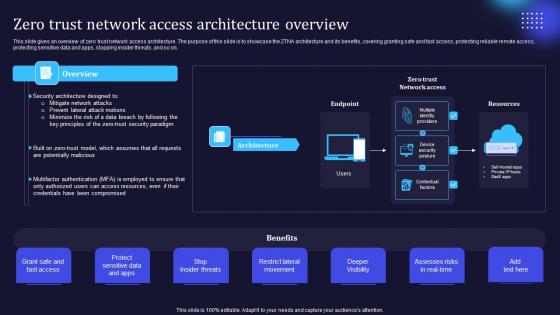
Zero Trust Model Zero Trust Network Access Architecture Overview
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Model Zero Trust Network Access Architecture Overview. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf
This slide discusses the fundamental concepts and terms of serverless architecture. The purpose of this slide is to outline the key terms used in serverless architecture. These are invocation, duration, cold start, concurrency limit and timeout. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Serverless Architecture Fundamental Role Serverless Computing Modern Technology Structure Pdf
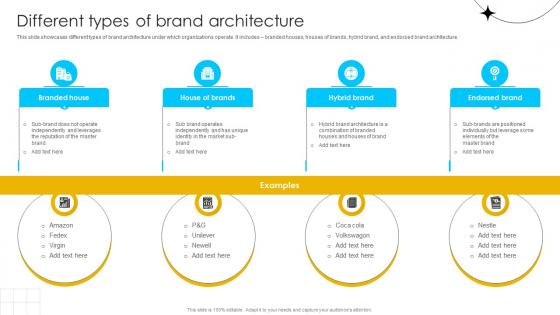
Brand Influence Different Types Of Brand Architecture Strategy SS V
This slide showcases different types of brand architecture under which organizations operate. It includes branded houses, houses of brands, hybrid brand, and endorsed brand architecture. If you are looking for a format to display your unique thoughts, then the professionally designed Brand Influence Different Types Of Brand Architecture Strategy SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Brand Influence Different Types Of Brand Architecture Strategy SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Brand Authority Brand Architecture Elements And Objectives Strategy SS V
This template covers the components of brand architecture, such as brand portfolio, portfolio roles, portfolio graphics, portfolio structure, and product-market context roles. There are so many reasons you need a Brand Authority Brand Architecture Elements And Objectives Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Brand Influence Brand Architecture Elements And Objectives Strategy SS V
This template covers the components of brand architecture, such as brand portfolio, portfolio roles, portfolio graphics, portfolio structure, and product-market context roles. There are so many reasons you need a Brand Influence Brand Architecture Elements And Objectives Strategy SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

BI Implementation Architecture For Data Analysis Slides Pdf
This slide showcases the architecture of BI for gaining effective data analytics for decision-making. This includes five major phases such as source system, data integration, analytics data stores, BI tools, and information delivery. Showcasing this set of slides titled BI Implementation Architecture For Data Analysis Slides Pdf. The topics addressed in these templates are Source Systems, Data Integration, Analytics Data Stores. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
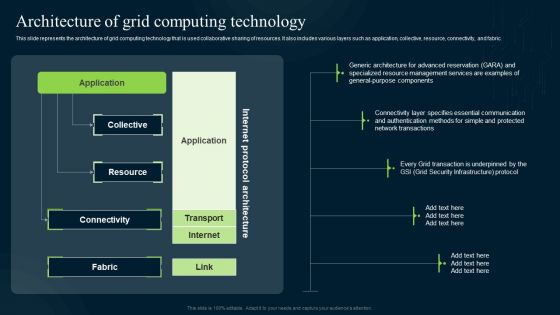
Grid Computing Infrastructure Architecture Of Grid Computing Technology Guidelines PDF
This slide represents the architecture of grid computing technology that is used collaborative sharing of resources. It also includes various layers such as application, collective, resource, connectivity, and fabric. Create an editable Grid Computing Infrastructure Architecture Of Grid Computing Technology Guidelines PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Grid Computing Infrastructure Architecture Of Grid Computing Technology Guidelines PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Key Steps To Design Software Integration Architecture Clipart Pdf
This slide presents various steps of creating a system integration pattern to ensure proper implementation of plan. It includes key components such as determine requirements, conduct analysis, design software infrastructure, develop management plan, design system integration, etc. Pitch your topic with ease and precision using this Key Steps To Design Software Integration Architecture Clipart Pdf. This layout presents information on Determine Requirements, Design Software Infrastructure, Design System Integration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture
This slide gives an overview of the pro-browser-based approach of zero trust network access architecture. The purpose of this slide is to showcase the architecture, pros and cons of the pro-browser-based architecture of ZTNA. The main benefits include simpler access to web apps and their suitability for small and less complex apps. Take your projects to the next level with our ultimate collection of Zero Trust Model Pro Browser Based Approach Of ZTNA Architecture. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf
This slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Zero Trust Network Access Vs Zero Trust Architecture Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
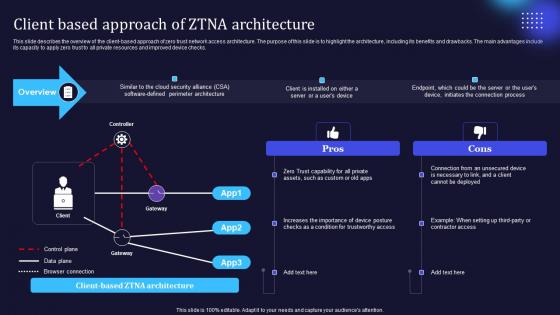
Zero Trust Model Client Based Approach Of ZTNA Architecture
This slide describes the overview of the client-based approach of zero trust network access architecture. The purpose of this slide is to highlight the architecture, including its benefits and drawbacks. The main advantages include its capacity to apply zero trust to all private resources and improved device checks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Model Client Based Approach Of ZTNA Architecture. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Model Client Based Approach Of ZTNA Architecture today and make your presentation stand out from the rest
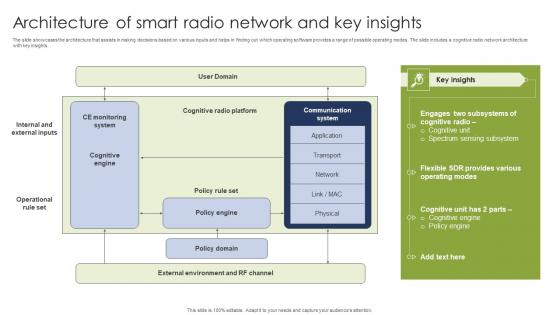
Architecture Of Smart Radio Network And Key Insights Clipart Pdf
The slide showcases the architecture that assists in making decisions based on various inputs and helps in finding out which operating software provides a range of possible operating modes. The slide includes a cognitive radio network architecture with key insights. Pitch your topic with ease and precision using this Architecture Of Smart Radio Network And Key Insights Clipart Pdf. This layout presents information on Policy Engine, Policy Domain, Cognitive Unit. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf
This slide outlines the architecture of container service for kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Boost your pitch with our creative Acktee 20 Architecture And Workflow Secure Computing Framework Guidelines Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Agenda Enhancing Workload Efficiency Through Cloud Architecture Review Slides Pdf
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda Enhancing Workload Efficiency Through Cloud Architecture Review Slides Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda Enhancing Workload Efficiency Through Cloud Architecture Review Slides Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
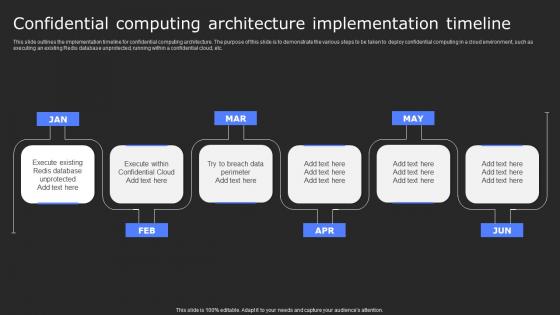
Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf
This slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Secure Computing Framework Confidential Computing Architecture Implementation Structure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
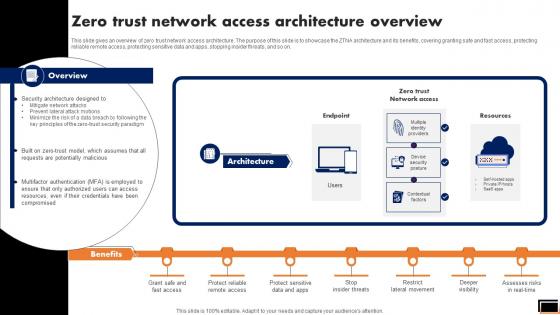
Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Welcome to our selection of the Zero Trust Network Access Architecture Overview Software Defined Perimeter SDP. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. This Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Logical Components Of Zero Trust Architecture Software Defined Perimeter SDP features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Zero Trust Model Logical Components Of Zero Trust Architecture
This slide describes the core logical components of the zero-trust network architecture model. The purpose of this slide is to showcase the various architectural parts and functions of logical elements, such as the policy engine, policy administrator, and policy environment point. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Zero Trust Model Logical Components Of Zero Trust Architecture from Slidegeeks and deliver a wonderful presentation.
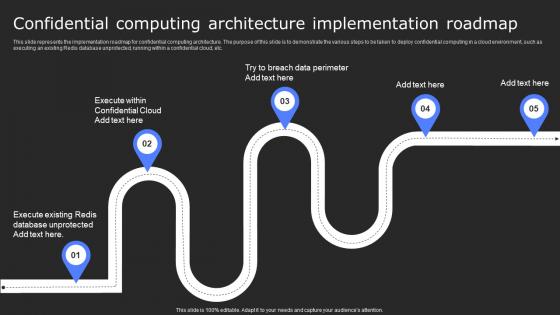
Confidential Computing Architecture Secure Computing Framework Themes Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Confidential Computing Architecture Secure Computing Framework Themes Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
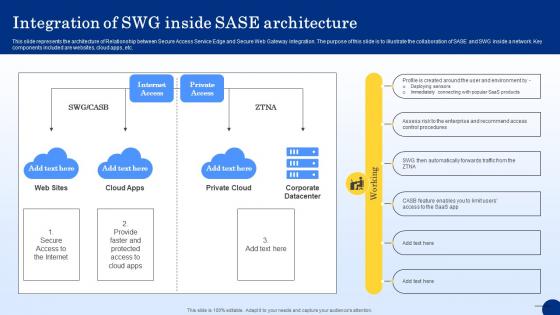
Integration Of SWG Inside SASE Architecture Web Threat Protection System
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of SWG Inside SASE Architecture Web Threat Protection System to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
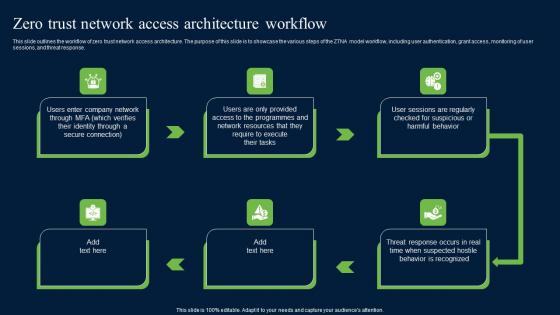
Zero Trust Network Access Architecture Workflow Themes Pdf
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Zero Trust Network Access Architecture Workflow Themes Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Zero Trust Network Access Architecture Workflow Themes Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Service Layer Architecture In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Service Layer Architecture In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Service Layer Architecture that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Layout Presentation Architecture In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Layout Presentation Architecture In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Layout Presentation Architecture that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Intel Cpu Architecture In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Intel Cpu Architecture In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Intel Cpu Architecture that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Arm Processor Architecture In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Arm Processor Architecture In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Arm Processor Architecture that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Computer Architecture Organization In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Computer Architecture Organization In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Computer Architecture Organization that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Peer Architecture In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Peer Architecture In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Peer Architecture that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Network Access Architecture Workflow Software Defined Perimeter SDP to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
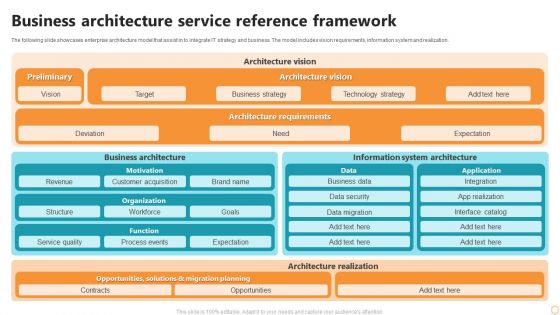
Business Architecture Service Reference Framework Ppt Styles Graphics Pictures PDF
The following slide showcases enterprise architecture model that assist in to integrate IT strategy and business. The model includes vision requirements, information system and realization. Pitch your topic with ease and precision using this Business Architecture Service Reference Framework Ppt Styles Graphics Pictures PDF. This layout presents information on Architecture Vision, Preliminary, Architecture Vision, Architecture Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Zero Trust Model Zero Trust Network Access Architecture Workflow
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Explore a selection of the finest Zero Trust Model Zero Trust Network Access Architecture Workflow here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Zero Trust Model Zero Trust Network Access Architecture Workflow to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

 Home
Home