Harnessing The World of Ethical Hacking PPT Presentation
Our Harnessing The World of Ethical Hacking PPT Presentation are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideGeeks and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideGeeks product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
 Impress Your
Impress Your Audience
 100%
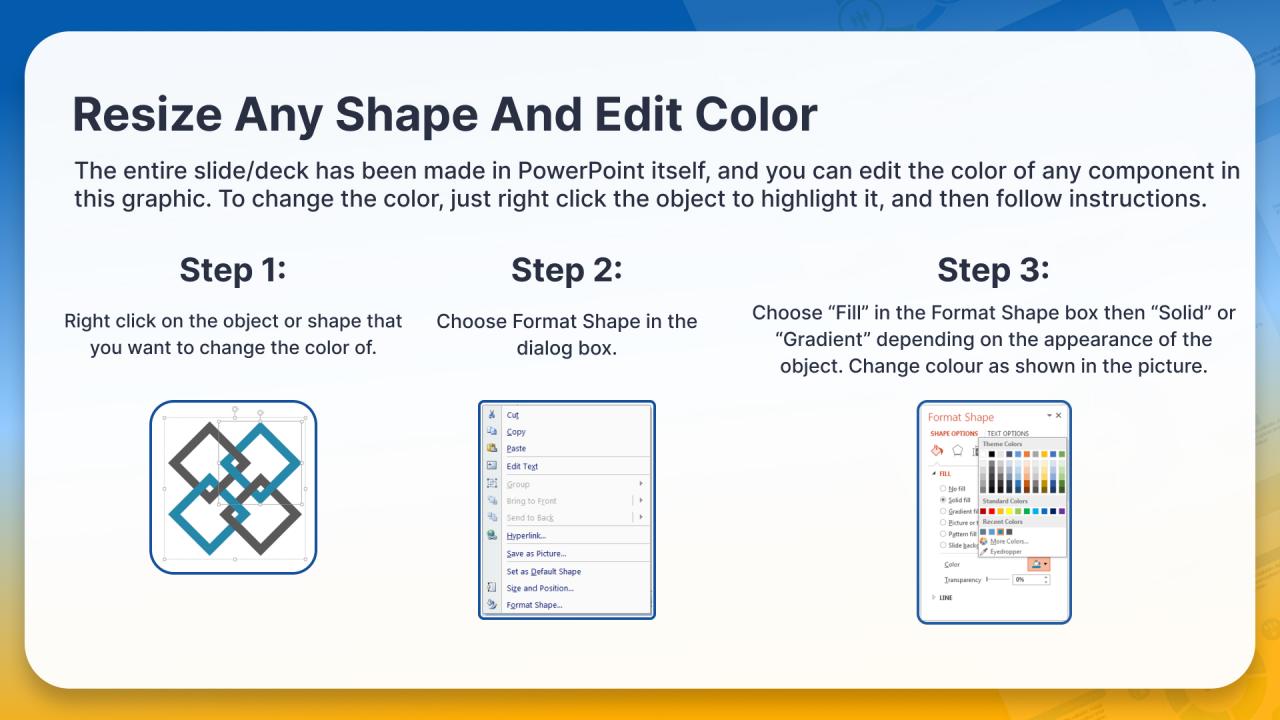
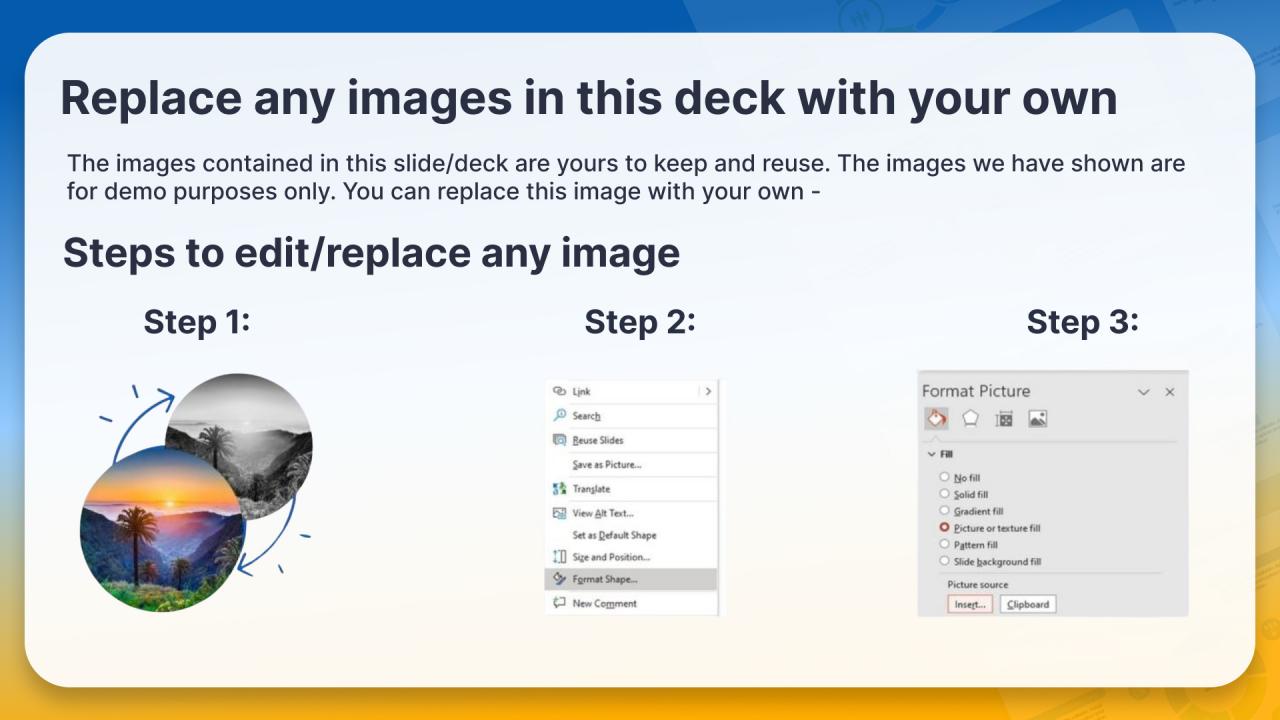
100% Editable
Google Slides
Features of these PowerPoint presentation slides:
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide highlights the presentation title: Harnessing the World of Ethical Hacking.
Slide 2: This slide states Agenda of the presentation.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide highlights title for topics that are to be covered next in the template.
Slide 5: This slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc.
Slide 6: This slide showcases the principles of security testing such as confidentiality, integrity, authentication, authorization, availability, etc.
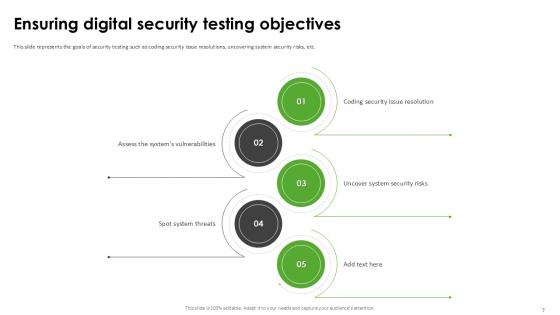
Slide 7: This slide represents the goals of security testing such as coding security issue resolutions, uncovering system security risks, etc.
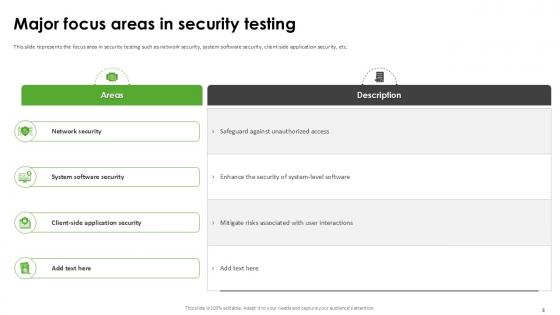
Slide 8: This slide represents the focus area in security testing such as network security, system software security, client-side application security, etc.
Slide 9: This slide showcases the advantages of software security testing such as identifying weaknesses, enhancing security, ensuring compliance, etc.
Slide 10: This slide highlights title for topics that are to be covered next in the template.
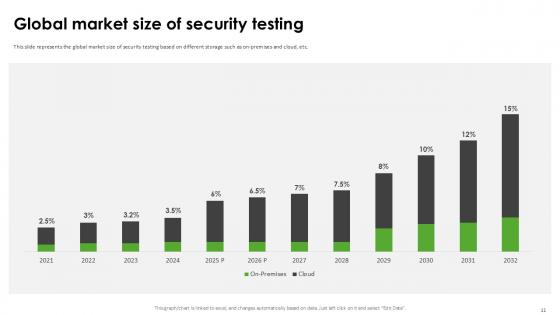
Slide 11: This slide represents the global market size of security testing based on different storage such as on-premises and cloud, etc.
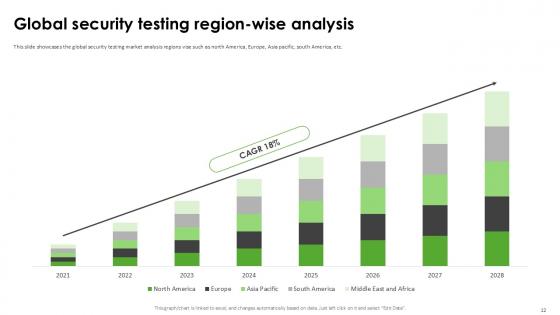
Slide 12: This slide showcases the global security testing market analysis regions vise such as north America, Europe, Asia pacific, south America, etc.
Slide 13: This slide showcases the innovative and future approaches of security testing such as fuzz testing, quantum computing threat assessment, IoT security testing, etc.
Slide 14: This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc.
Slide 15: This slide highlights title for topics that are to be covered next in the template.
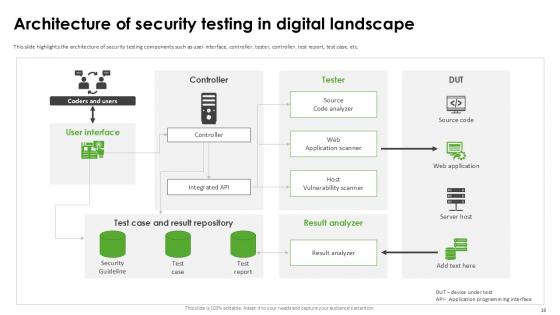
Slide 16: This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc.
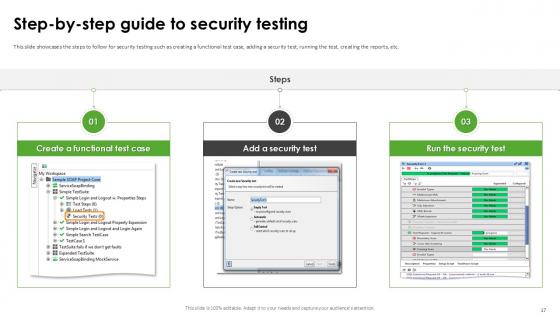
Slide 17: This slide showcases the steps to follow for security testing such as creating a functional test case, adding a security test, running the test, creating the reports, etc.
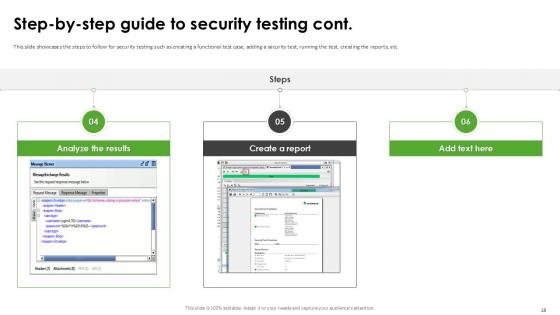
Slide 18: This is another slide continuing the steps to follow for security testing.
Slide 19: This slide highlights title for topics that are to be covered next in the template.
Slide 20: This slide highlights the top open-source tools of security testing such as netsparker, immuniweb, Vega, wapiti, etc.
Slide 21: This slide represents the types of security testing such as penetration testing, application security testing, web application security testing, etc.
Slide 22: This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc.
Slide 23: This slide highlights title for topics that are to be covered next in the template.
Slide 24: This slide represents the security testing best practices such as thorough testing across development, vulnerability identification and resolution, etc.
Slide 25: The purpose of this slide is to highlight the key approaches for implementing security testing such as identifying and prioritizing assets, choosing appropriate testing tools, etc.
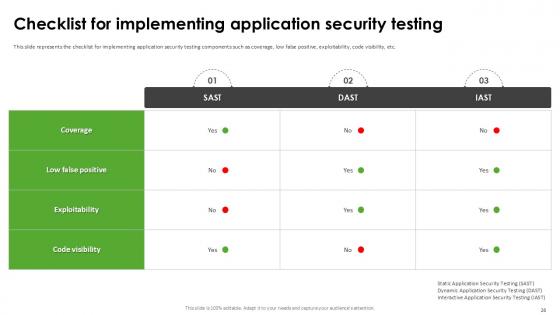
Slide 26: This slide represents the checklist for implementing application security testing components such as coverage, low false positive, exploitability, code visibility, etc.
Slide 27: This slide highlights title for topics that are to be covered next in the template.
Slide 28: This slide highlights the challenges faced during the implementation of security testing such as the velocity of software development, weaknesses in the code, etc.
Slide 29: This slide represents the major challenges of security testing with solutions such as dynamic threat landscape, false positives in security testing, limitation of security testing efficiency, etc.
Slide 30: This slide highlights title for topics that are to be covered next in the template.
Slide 31: The purpose of this slide is to outline the security testing implementation training program such as mode, cost, agenda, and schedule for the training programs.
Slide 32: The purpose of this slide is to highlight the estimated cost of various training components, such as instructors' cost, training material cost, etc.
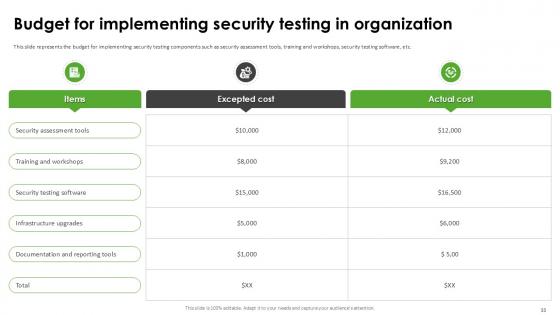
Slide 33: This slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc.
Slide 34: This slide highlights title for topics that are to be covered next in the template.
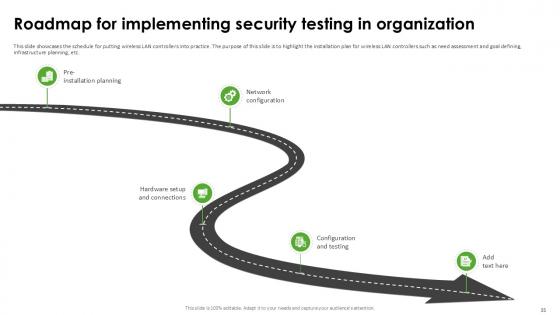
Slide 35: This slide showcases the schedule for putting wireless LAN controllers into practice.
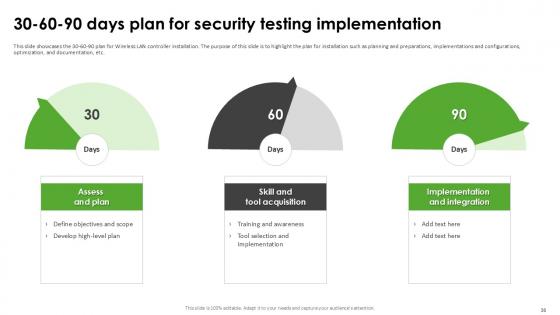
Slide 36: This slide showcases the 30-60-90 plan for Wireless LAN controller installation.
Slide 37: This slide highlights title for topics that are to be covered next in the template.
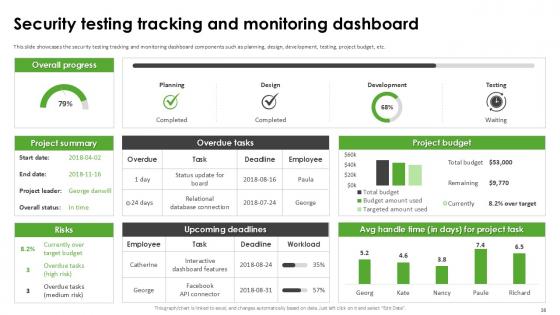
Slide 38: This slide showcases the security testing tracking and monitoring dashboard components such as planning, design, development, testing, project budget, etc.
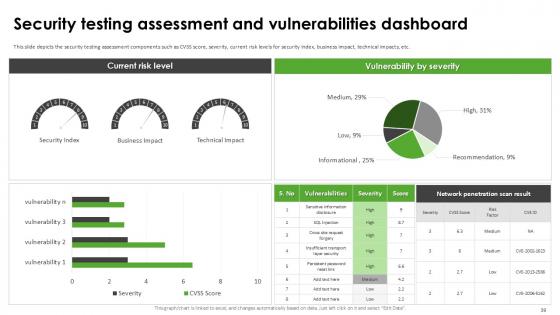
Slide 39: This slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc.
Slide 40: This slide highlights title for topics that are to be covered next in the template.
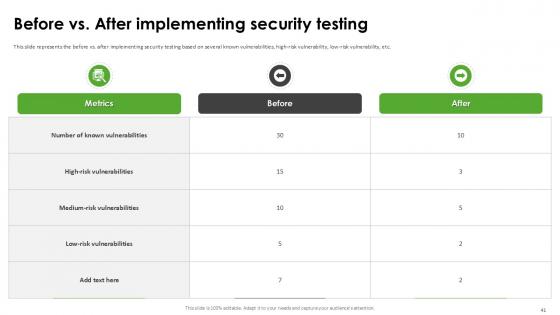
Slide 41: This slide represents the before vs. after implementing security testing based on several known vulnerabilities, high-risk vulnerability, low-risk vulnerability, etc.
Slide 42: This slide highlights title for topics that are to be covered next in the template.
Slide 43: This slide represents the security testing case study of - IT health check with objectives, skills used, and approaches to be used.
Slide 44: This slide contains all the icons used in this presentation.
Slide 45: This slide is titled as Additional Slides for moving forward.
Slide 46: This slide showcases the evolution of security testing from late 1960 when the inception of security testing was unclear to universal practice for all sizes.
Slide 47: This is an Idea Generation slide to state a new idea or highlight information, specifications, etc.
Slide 48: This is Our Target slide. State your targets here.
Slide 49: This slide depicts Venn diagram with text boxes.
Slide 50: This slide shows Post It Notes. Post your important notes here.
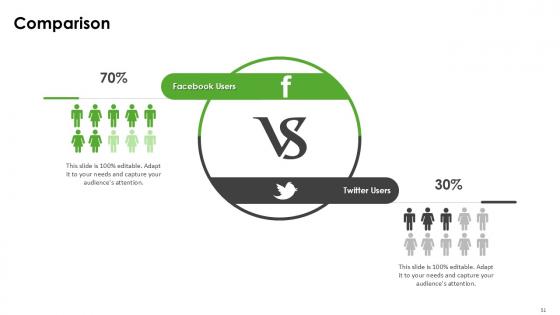
Slide 51: This is a Comparison slide to state comparison between commodities, entities etc.
Slide 52: This slide contains Puzzle with related icons and text.
Slide 53: This slide displays Mind Map with related imagery.
Slide 54: This is a Thank You slide with address, contact numbers and email address.
Harnessing The World of Ethical Hacking PPT Presentation with all 62 slides:
Use our Harnessing The World of Ethical Hacking PPT Presentation to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Most Relevant Reviews
-
Great quality product.
-
Easily Editable.

 Home
Home