Client Side Encryption Implementation Guide Ppt Template
Our Client Side Encryption Implementation Guide Ppt Template are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideGeeks and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideGeeks product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
 Impress Your
Impress Your Audience
 100%
100% Editable
Google Slides
Features of these PowerPoint presentation slides:
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide highlights the presentation title: Client-side Encryption Implementation Guide.
Slide 2: This slide states Agenda of the presentation.
Slide 3: This slide shows Table of Content for the presentation.
Slide 4: This slide highlights title for topics that are to be covered next in the template.
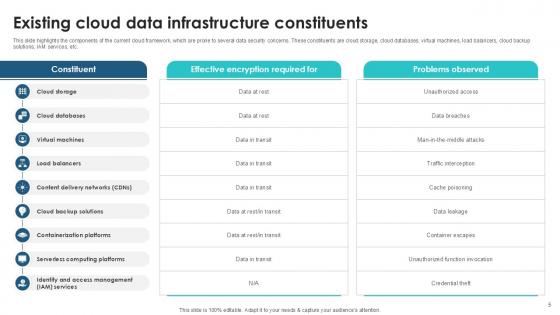
Slide 5: This slide highlights the components of the current cloud framework, which are prone to several data security concerns.
Slide 6: This slide highlights title for topics that are to be covered next in the template.
Slide 7: This slide discusses the security issues faced by the organization due to a lack of encryption in cloud services.
Slide 8: This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc.
Slide 9: This slide highlights title for topics that are to be covered next in the template.
Slide 10: The purpose of this slide is to indicate the performance analysis of the organization’s current security infrastructure.
Slide 11: This slide highlights title for topics that are to be covered next in the template.
Slide 12: The purpose of this slide is to represent the summary of the cloud data encryption implementation project.
Slide 13: This slide highlights title for topics that are to be covered next in the template.
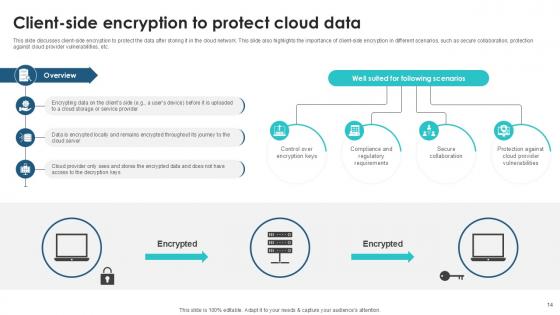
Slide 14: This slide discusses client-side encryption to protect the data after storing it in the cloud network.
Slide 15: This slide discusses server-side encryption to protect the data after storing it in the cloud network.
Slide 16: This slide highlights title for topics that are to be covered next in the template.
Slide 17: This slide represents the timeline to implement cloud data encryption in an organization.
Slide 18: This slide represents the checklist for integrating cloud encryption into business.
Slide 19: This slide highlights title for topics that are to be covered next in the template.
Slide 20: This slide represents the team structure for the cloud data encryption implementation project.
Slide 21: This slide shows the matrix to assign multiple responsibilities to the different team members for the cloud data encryption implementation project.
Slide 22: This slide highlights title for topics that are to be covered next in the template.
Slide 23: This slide represents the different steps involved in the cloud data encryption implementation process.
Slide 24: This slide highlights title for topics that are to be covered next in the template.
Slide 25: This slide demonstrates the process for client-side encryption with keys managed by Key Management System.
Slide 26: This slide demonstrates the decryption process for client-side encryption with keys managed by Key Management System.
Slide 27: This slide shows the client-side encryption and decryption process with the keys provided by the customer.
Slide 28: This slide highlights title for topics that are to be covered next in the template.
Slide 29: This slide demonstrates the process for server-side encryption with keys managed by Key Management System.
Slide 30: This slide demonstrates the decryption process for server-side encryption with keys managed by Key Management System.
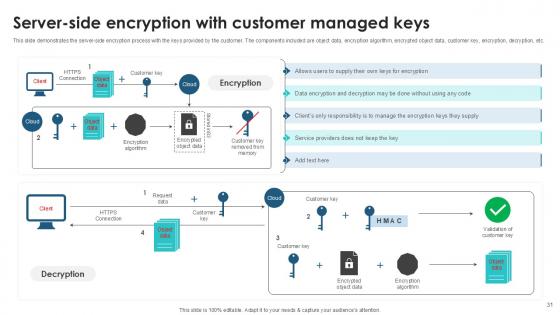
Slide 31: This slide demonstrates the server-side encryption process with the keys provided by the customer.
Slide 32: This slide highlights title for topics that are to be covered next in the template.
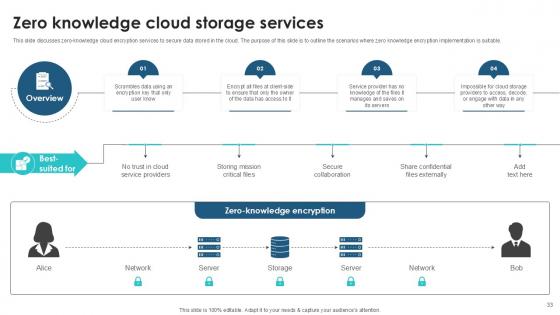
Slide 33: This slide discusses zero-knowledge cloud encryption services to secure data stored in the cloud.
Slide 34: The purpose of this slide is to highlight the several factors to be considered while selecting zero-knowledge encryption service providers.
Slide 35: This slide highlights title for topics that are to be covered next in the template.
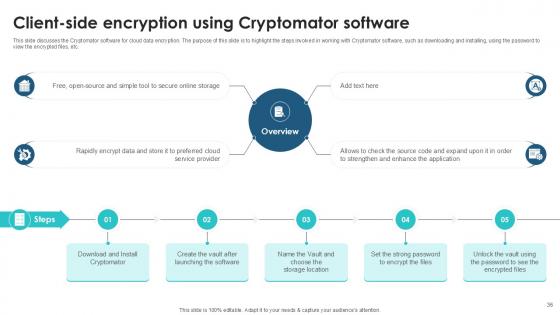
Slide 36: This slide discusses the Cryptomator software for cloud data encryption.
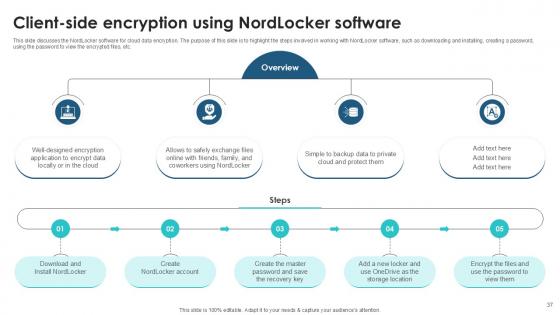
Slide 37: This slide discusses the NordLocker software for cloud data encryption.
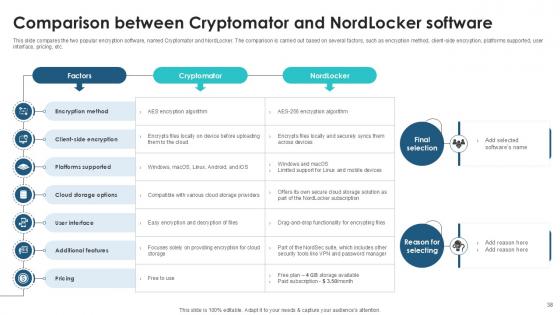
Slide 38: This slide compares the two popular encryption software, named Cryptomator and NordLocker.
Slide 39: This slide highlights title for topics that are to be covered next in the template.
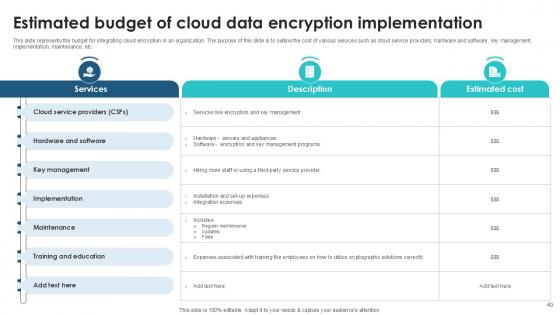
Slide 40: This slide represents the budget for integrating cloud encryption in an organization.
Slide 41: This slide highlights title for topics that are to be covered next in the template.
Slide 42: This slide represents the composition of a training plan for cloud data encryption implementation.
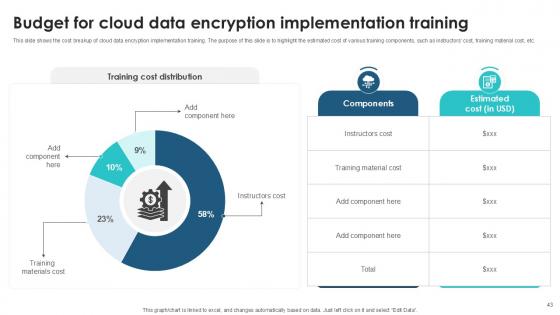
Slide 43: This slide shows the cost breakup of cloud data encryption implementation training.
Slide 44: This slide highlights title for topics that are to be covered next in the template.
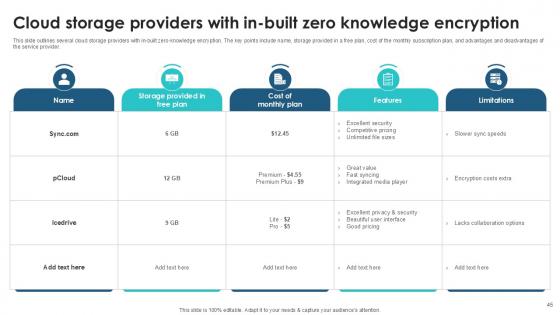
Slide 45: This slide outlines several cloud storage providers with in-built zero-knowledge encryption.
Slide 46: This slide highlights the availability of various services in different zero-knowledge encryption providers to encrypt the data stored in the cloud.
Slide 47: This slide demonstrates the top cloud cryptography solution providers.
Slide 48: This slide highlights title for topics that are to be covered next in the template.
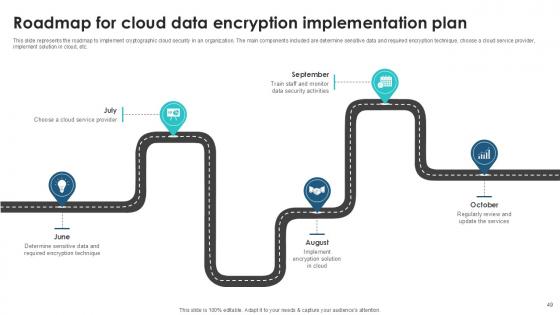
Slide 49: This slide represents the roadmap to implement cryptographic cloud security in an organization.
Slide 50: This slide highlights title for topics that are to be covered next in the template.
Slide 51: The purpose of this slide is to discuss the challenges faced while encrypting cloud data.
Slide 52: This slide highlights title for topics that are to be covered next in the template.
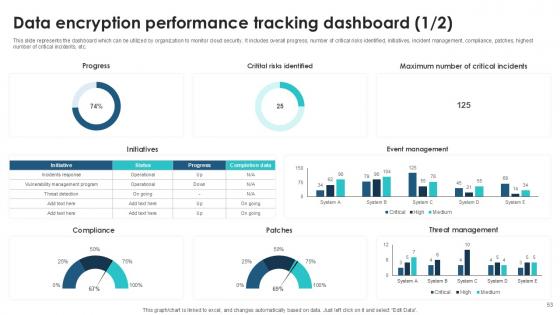
Slide 53: This slide represents the dashboard which can be utilized by organization to monitor cloud security.
Slide 54: This slide represents the dashboard that can be utilized by organizations to monitor security risks.
Slide 55: This slide highlights title for topics that are to be covered next in the template.
Slide 56: This slide represents the various factors that showcase the improvement of application security after adopting encryption.
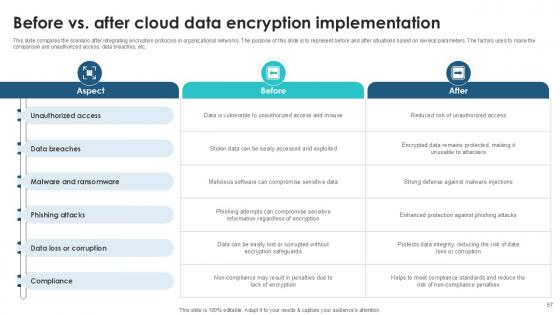
Slide 57: This slide compares the scenario after integrating encryption protocols in organizational networks.
Slide 58: This slide contains all the icons used in this presentation.
Slide 59: This slide is titled as Additional Slides for moving forward.
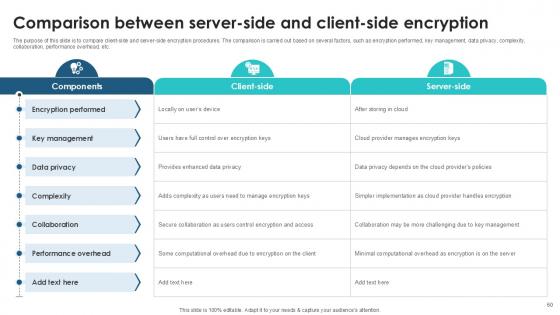
Slide 60: The purpose of this slide is to compare client-side and server-side encryption procedures.
Slide 61: This slide represents the key management process for encrypted cloud storage.
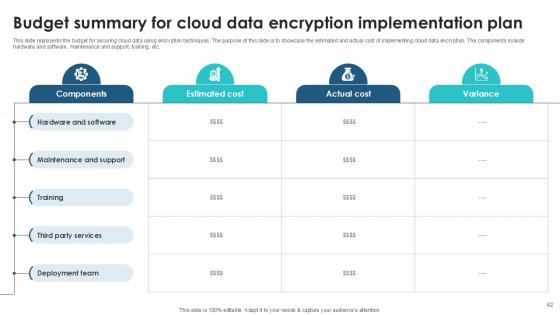
Slide 62: This slide represents the budget for securing cloud data using encryption techniques.
Slide 63: This slide contains Puzzle with related icons and text.
Slide 64: This slide depicts Venn diagram with text boxes.
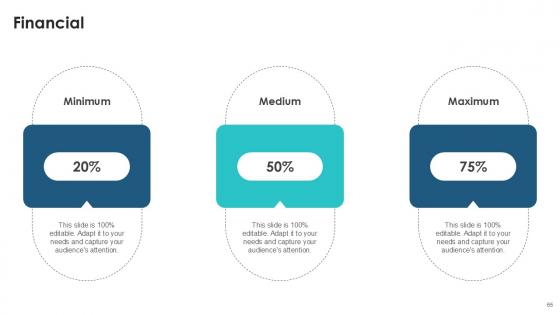
Slide 65: This is a Financial slide. Show your finance related stuff here.
Slide 66: This slide shows SWOT describing- Strength, Weakness, Opportunity, and Threat.
Slide 67: This is a Thank You slide with address, contact numbers and email address.
Client Side Encryption Implementation Guide Ppt Template with all 75 slides:
Use our Client Side Encryption Implementation Guide Ppt Template to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
Most Relevant Reviews
-
The Designed Graphic are very professional and classic.
-
Best way of representation of the topic.

 Home
Home